💡 Subscribe to DarkWebInformer.com for Unmatched Cyber Threat Intelligence 💡
Why Subscribe? Let me do the work and save you time.
Stay ahead of cyber threats and safeguard your digital assets while enhancing your cybersecurity awareness with these exclusive subscriber-only features:
-
📜
Detailed Threat Posts: Stay updated on breaches, ransomware, DDoS attacks, and more.
-
📡
Exclusive Threat Feeds: Access the latest ransomware victim disclosures, breaches, and other critical updates.
-
🖼️
High-Resolution Screenshots: All posts include watermark-free, high-resolution images.
-
🔗
Direct Claim URLs: Instantly access claims with direct links for fast verification.
Quick Facts
- Vulnerability ID: https://nvd.nist.gov/vuln/detail/CVE-2024-50603
- Severity: Critical (CVSS: 10)
- Attack Vector: Remote
- Reported On: January 2024
- Affected Product: Aviatrix Controller versions 7.x through 7.2.4820
- Patched: Yes, patch available
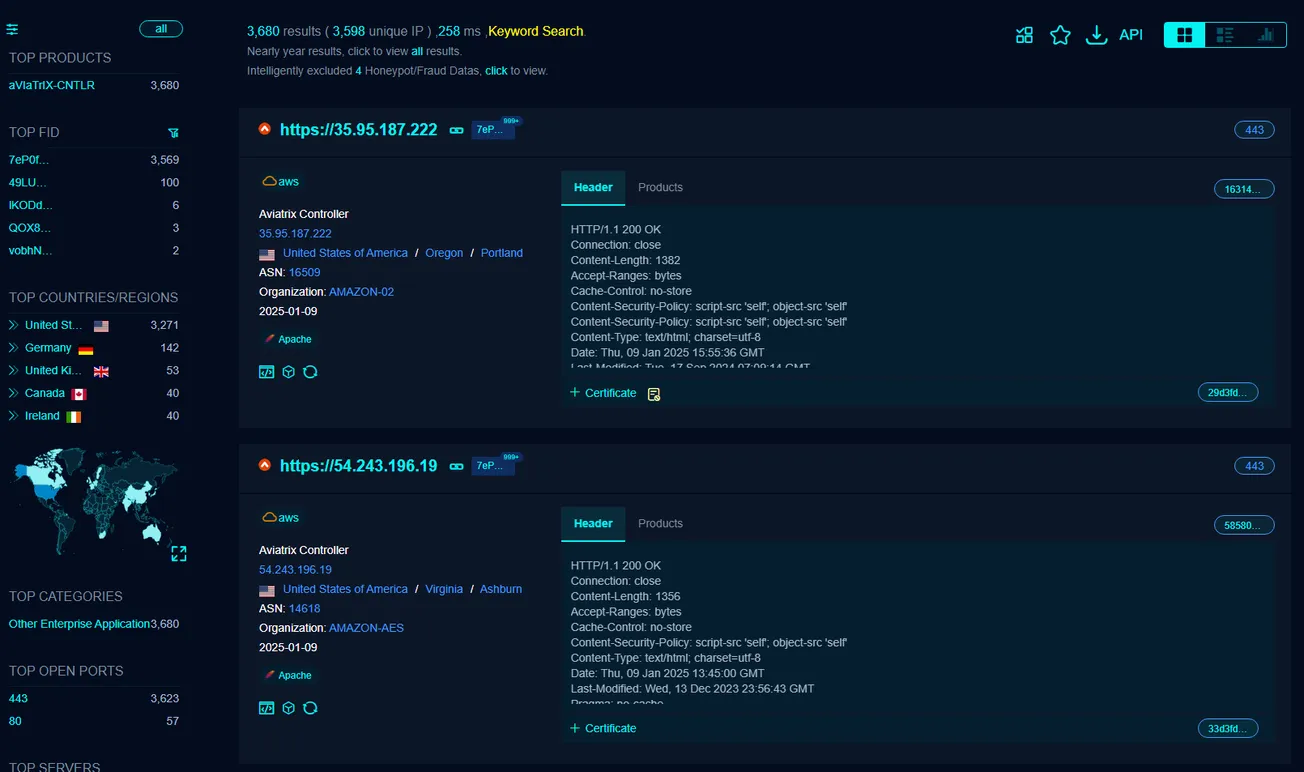
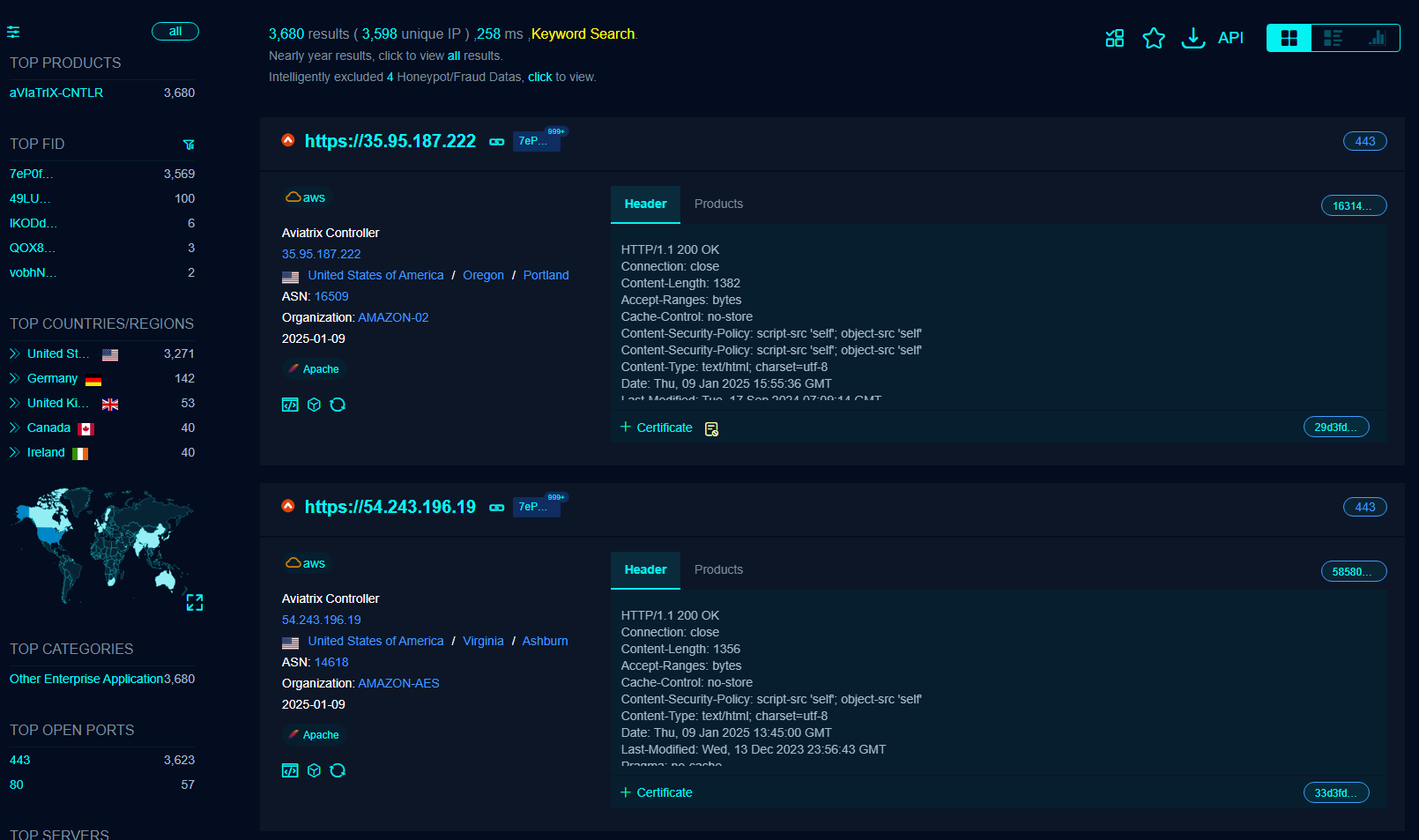
- FOFA Results: https://en.fofa.info/result?qbase64=YXBwPSJhVklhVHJJWC1DTlRMUiI%3D
Description
CVE-2024-50603 is a critical security vulnerability in the Aviatrix Controller, a key component of network infrastructure for many organizations. The flaw allows unauthenticated remote attackers to execute arbitrary commands on the system due to improper neutralization of special elements used in OS commands. This issue stems from improper input handling in specific API endpoints.
Compromised Data
If exploited, this vulnerability could lead to:
- Full compromise of affected systems.
- Unauthorized access to sensitive network configurations.
- Arbitrary command execution.
Details
- Root Cause: The vulnerability lies in the Aviatrix Controller’s API, implemented in PHP. Specific API actions, such as
list_flightpath_destination_instancesandflightpath_connection_test, fail to sanitize user input properly. Parameters such ascloud_typeandsrc_cloud_typeare directly incorporated into system commands without sufficient validation. - Potential Impact: An attacker can exploit this flaw to execute system commands, potentially leading to full system compromise.
- Risk Scope: Analysis via FOFA indicates approximately 3,680 Aviatrix Controllers are exposed to the internet, greatly increasing the risk of exploitation.
Implications
Organizations using the affected versions of the Aviatrix Controller face significant security threats, including:
- Unauthorized system control by attackers.
- Exposure of sensitive network data.
- Potential lateral movement within compromised environments.
Mitigation and Recommendations
To address this vulnerability, organizations should:
- Update Software: Aviatrix has released a patch for this issue. Update the Aviatrix Controller to the latest version immediately.
- Restrict Access: Limit access to the Aviatrix Controller by:
- Restricting its exposure to trusted networks only.
- Implementing strict firewall rules to block unauthorized access.
- Monitor Systems: Continuously review system logs for unusual activity, particularly any command injections or unauthorized access attempts.
- Enhance Security Controls: Apply input validation at all API endpoints to prevent similar vulnerabilities in the future.
Conclusion
CVE-2024-50603 is a critical vulnerability that demands immediate attention from organizations using the Aviatrix Controller. With over 3,600 systems potentially exposed online, the risk of exploitation is high. Applying the latest patch and implementing robust security measures can significantly mitigate these threats.