Critical Pre-Auth RCE Vulnerability in BeyondTrust Remote Support & PRA Exposes Thousands of Instances (CVE-2026-1731)
Vulnerability Overview
BeyondTrust has disclosed a critical pre-authentication remote code execution vulnerability affecting its Remote Support (RS) and Privileged Remote Access (PRA) products. The flaw, tracked as CVE-2026-1731, carries a near-maximum CVSS score of 9.9 and could allow an unauthenticated remote attacker to execute arbitrary operating system commands without any authentication or user interaction — making it trivially exploitable in the right conditions.
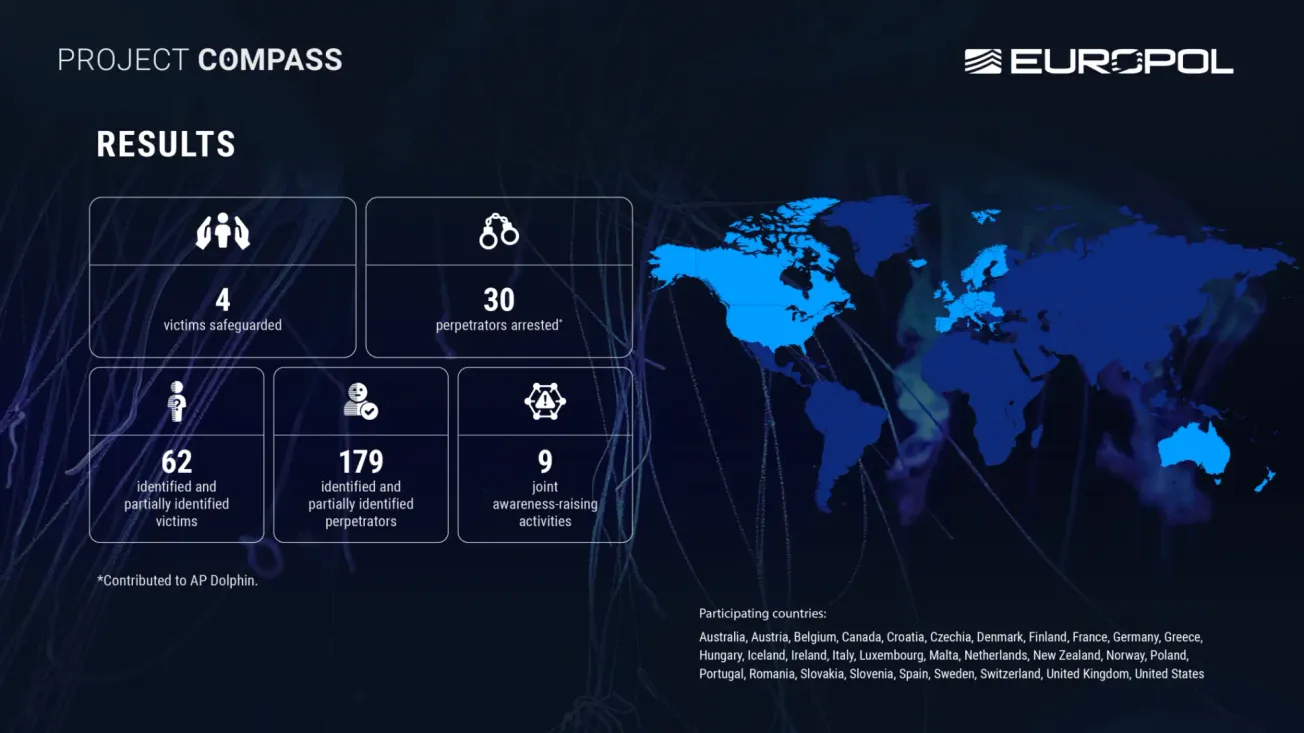
The vulnerability was identified by security researcher Harsh Jaiswal and the Hacktron AI team through AI-enabled variant analysis and was responsibly disclosed to BeyondTrust. According to the researchers, roughly 11,000 BeyondTrust Remote Support instances are currently exposed to the internet, with approximately 8,500 of those being on-premises deployments that remain potentially vulnerable if patches haven't been applied.
This is particularly concerning given BeyondTrust's massive enterprise footprint — the company provides identity security services to more than 20,000 customers across over 100 countries, including 75% of the Fortune 100. Remote Support and Privileged Remote Access are widely deployed for IT helpdesk operations and privileged session management in enterprise environments, meaning the potential blast radius of this vulnerability is significant.
Technical Details
CVE-2026-1731 is classified under CWE-78: Improper Neutralization of Special Elements used in an OS Command (OS Command Injection). The vulnerability exists because the application fails to properly sanitize input in specially crafted client requests, allowing an attacker to inject and execute operating system commands in the context of the site user.
Full technical details of the exploitation method have been withheld to give organizations time to apply patches.
Affected Versions
| Product | Affected Versions | Fixed Version |
|---|---|---|
| Remote Support (RS) | 25.3.1 and prior | 25.3.2+ / Patch BT26-02-RS |
| Privileged Remote Access (PRA) | 24.3.4 and prior | 25.1.1+ / Patch BT26-02-PRA |
Patch & Remediation Status
/appliance interface if automatic updates are not enabled.Historical Context: BeyondTrust as a High-Value Target
While BeyondTrust has confirmed there is no known active exploitation of CVE-2026-1731 at this time, the platform has a documented history of being targeted by sophisticated threat actors.
Exposure Analysis
According to Hacktron AI's scanning via Shodan and FOFA:
Recommendations
- Patch immediately. Self-hosted customers should apply BT26-02-RS or BT26-02-PRA without delay.
- Verify patch status. Confirm that automatic updates are enabled or that the patch has been successfully applied through the
/applianceinterface. - Audit access logs. Review BeyondTrust RS/PRA logs for unusual or unauthorized access patterns, particularly unauthenticated requests.
- Restrict network exposure. Limit internet-facing access to BeyondTrust instances where possible. Place behind VPN or restrict to known IP ranges.
- Monitor for IOCs. Watch for updates from BeyondTrust, CISA, and threat intelligence providers regarding any indicators of compromise.