GitHub: https://github.com/Clats97/ClatScope
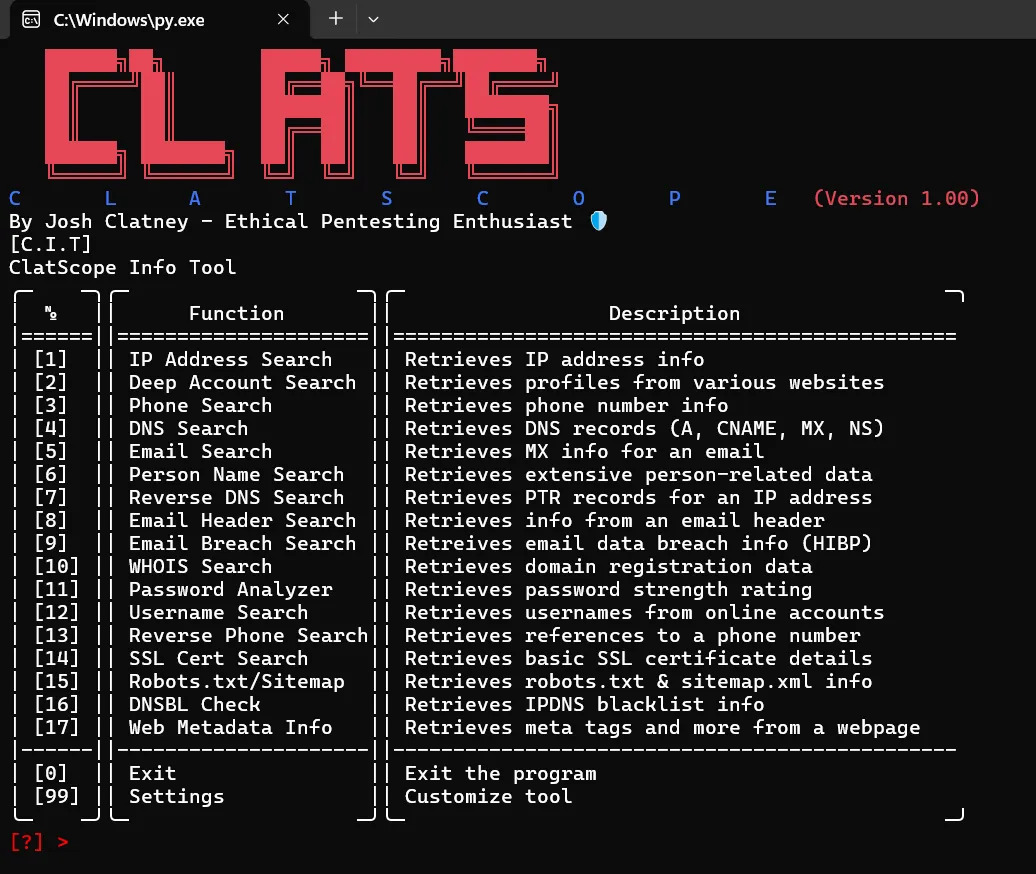
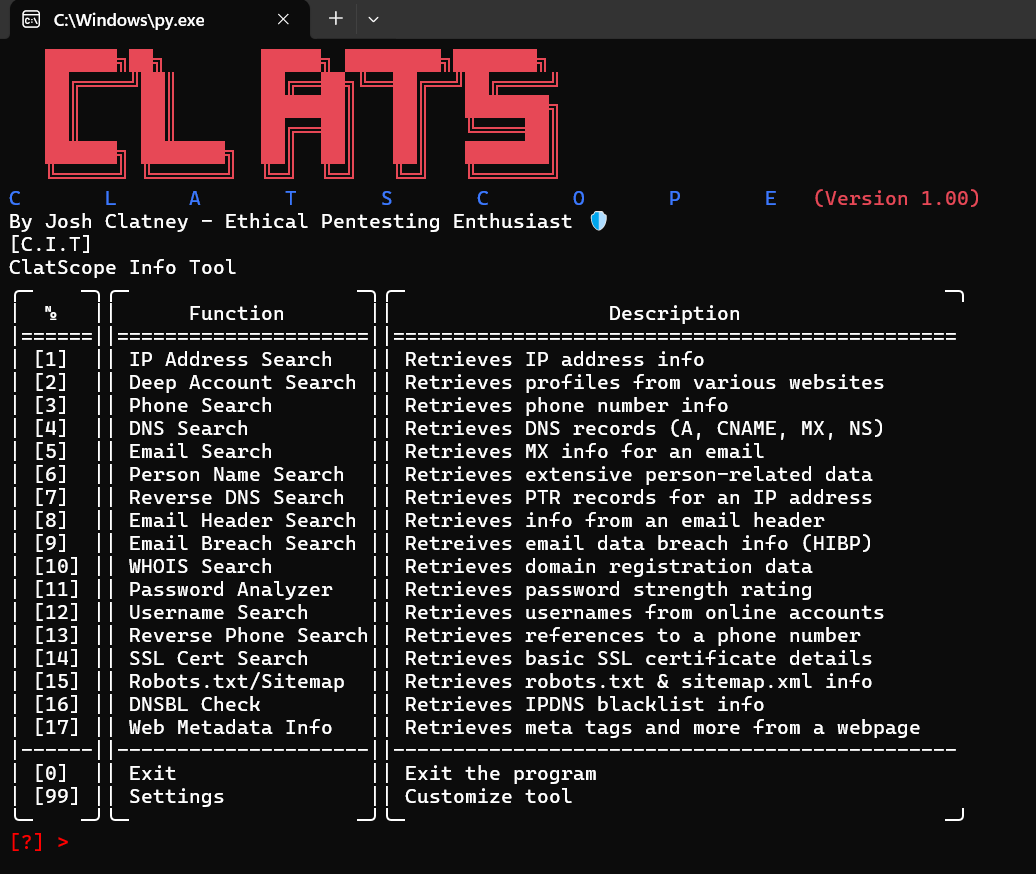
ClatScope Info Tool
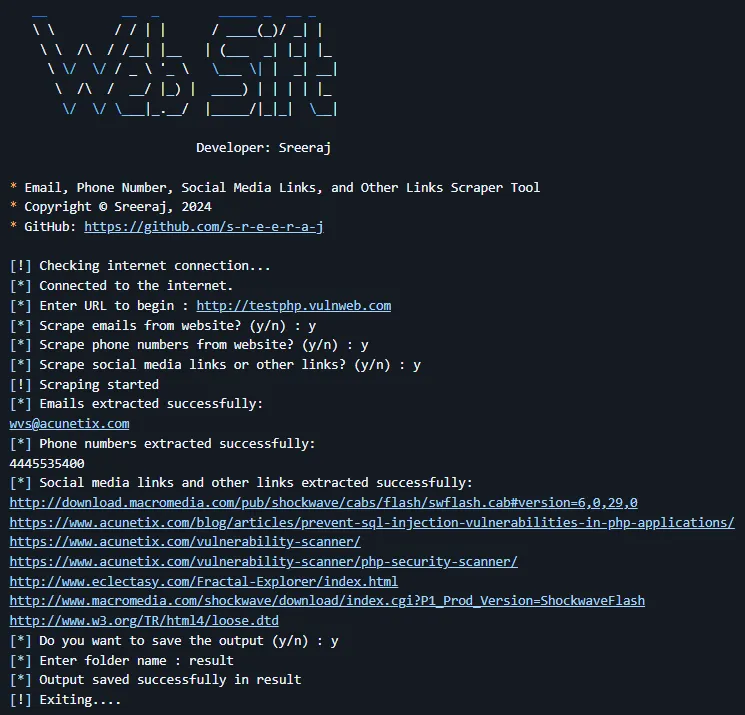
ClatScope Info Tool – A versatile OSINT utility for retrieving geolocation, DNS, WHOIS, phone, email, usernames, person related data, password strength, data breach information and more. Perfect for investigators, pentesters, or anyone looking for a quick reconnaissance script.
ClatScope is an OSINT tool that performs various lookups and analyses on provided data:
- IP Address Lookups:
- Retrieves IP geolocation details, ISP, and region.
- Performs DNSBL checks to see if an IP is blacklisted.
- Phone Number Lookups:
- Fetches basic phone number details (region, carrier).
- Conducts a reverse phone lookup via Google search (Custom Search API).
- Email Lookups and Analysis:
- Checks email validity and existence of mail exchanger (MX) records.
- Performs data breach checks against Have I Been Pwned (HIBP). -Analyzes raw email headers (extracting IP addresses, SPF, DKIM, DMARC alignment, etc.).
- Username Searches:
- Searches across multiple platforms (e.g., Facebook, Twitter, Instagram, etc.) to see if a username exists.
- Domain / Website Lookups:
- DNS record queries (A, CNAME, MX, NS).
- WHOIS details (registrar, creation date, etc) -IS details (registrar, creation date, etc.). -SSL certificate analysis. -Robots.txt and sitemap.xml retrieval to discover site structure. -Webpage metadata extraction (title, meta keywords, meta description).
- Password Strength Checking:
- Evaluates complexity based on length, character variety, and common word usage.
- Additional Features:
- Person name searches (via Google’s Custom Search API) to get text from resulting pages.
- Reverse DNS lookups for IP addresses.
- Settings menu to change color scheme.
Throughout the script, a textual UI is presented, prompting the user for inputs (e.g., IP address, phone number). Results are printed in styled ASCII frames using the pystyle library for aesthetics.
Version: 1.00
Author: Joshua M Clatney aka Clats97 (Ethical Pentesting Enthusiast)
Description
ClatScope Info Tool is an all-in-one OSINT (Open-Source Intelligence) utility script that queries public APIs, DNS records, and other online resources to gather and display information about IPs, domains, emails, phone numbers, and more. You will need a Google Custom Search API and a Have I Been Pwned API to take advantage of all the features ClatScope has to offer.
Features
- IP Information – Extract IP geolocation, ISP, and Google Maps link.
- Deep Account Search & Username Search – Check over 250 websites to see if a given username exists.
- Phone Number Parsing – Validate phone numbers, determine carriers, and check region.
- DNS & Reverse DNS – Retrieve DNS records (A, CNAME, MX, NS) and PTR records.
- Email Lookup – Check MX records, validate format, parse email headers for IP addresses, and more.
- Email Breach Search - Checks Have I Been Pwned to determine if an email address has been compromised.
- Email Header Analysis - Analyzes an email header and extracts data.
- Person Search - Look up public details about a person.
- WHOIS Lookup – Fetch domain registration details.
- Password Strength Check – Rate your password’s strength based on multiple criteria.
- Theme/Color Settings – Adjust console output color.
Installation
- Clone the Repository:git clone https://github.com/Clats97/ClatScope-Info-Tool.git
- Install Dependencies:pip install requests pystyle phonenumbers dnspython email_validator beautifulsoup4 whois
- Run the Script: bash python clatscope_info_tool.py
Usage
When you run the script, it will present you with a menu. Simply type the number corresponding to the function you wish to use, and follow the on-screen prompts. For example:
- IP Info Search – Option [1]
- Deep Account Search – Option [2]
- DNS Search – Option [4]
- etc.
- IN ORDER FOR THE PASSWORD STRENGTH ANALYZER TO WORK PROPERLY, YOU MUST OPEN CLATSCOPE INFO TOOL IN THE FOLDER THAT HAS "PASSWORDS.TXT"
- You will need to enter your own Google Custom Sesarch & Have I been Pwned API key to use all the features in this tool.
- If you want to use the password strength checker against a dictionary or known common-passwords file, place your dictionary file as passwords.txt in the same directory as the script.
- The script references Google Custom Search API keys (API_KEY, CX, and CLIENT_ID) and HIBP API key. If you want to use the features that query external services (like Google search or HIBP), you must obtain valid keys and place them in the script. Important: If you do not have valid API keys, the related external queries (e.g. person search, reverse phone lookup) will fail or return errors.
Below is a closer look at what each function in the script accomplishes:
- Main Menu & main() Function
- Displays the ASCII-based menu.
- Repeatedly prompts for user input.
- Clalls the relevant function (like ip_info(ip) or deep_account_search(nickname)) based on the menu choice.
- ip_info(ip)
- Uses requests.get("https://ipinfo.io/{ip}/json") to fetch IP-related information.
- Displays city, region, country, ISP (org), approximate location, etc.
- deep_account_search(nickname) -Iterates over a large list of possible platform URL formats (e.g., https://twitter.com/{}, https://reddit.com/user/{}, etc.).
- Sends asynchronous HTTP requests with ThreadPoolExecutor to quickly check which URLs respond with status code 200.
- Prints whether each potential profile is “Found” or “Not Found.”
- phone_info(phone_number)
- Parses the phone number using phonenumbers.parse(...).
- Receives geocoding (country, region) and the carrier operator.
- Validates whether the number format is correct.
- reverse_phone_lookup(phone_number)
- Uses Google’s Custom Search API to search references to the phone number on the internet. -Fetches text from each top link and displays them.
- dns_lookup(domain)
- Uses the dns.resolver.resolve() method to query A, CNAME, MX, and NS records.
- Shows “No records found” if none exist.
- email_lookup(email)
- Validates email format with email_validator.
- Checks DNS MX records for the domain.
- Declares “Likely Valid” if MX records are found, or “Might be invalid” otherwise.
- person_search(first_name, last_name, city)
- Leverages Google’s Custom Search API to look for references to a person’s name + location.
- Fetches page text, then displays top results in a nicely formatted table.
- analyze_email_header(raw_headers
- Parses raw email headers using Python’s built-in email.parser.
- Extracts IP addresses from any “Received” lines.
- Performs geolocation on each IP.
- Checks for SPF, DKIM, and DMARC results in Authentication-Results fields.
- haveibeenpwned_check(email)
- Calls the HIBP v3 API.
- If breaches are found, prints each breach name, domain, date, data classes.
- Otherwise, declares “No breaches found.”
- whois_lookup(domain)
- Uses Python’s whois to retrieve domain registration data.
- Shows registrar name, creation/expiration dates, name servers, etc.
- password_strength_tool() / check_password_strength(password)
- Checks password length and usage of uppercase, lowercase, digits, and symbols.
- Looks for common words in the passwords.txt file if present.
- Outputs “Weak,” “Moderate,” or “Strong.”
- check_ssl_cert(domain)
- Creates a secure socket connection on port 443 to retrieve the SSL certificate.
- Prints the certificate issuer, validity range, etc.
- check_robots_and_sitemap(domain)
- Tries to retrieve robots.txt and sitemap.xml from https://{domain}/.
- Prints the HTTP status code and the first few lines of the file, if it exists.
- check_dnsbl(ip_address)
- Reverses the IP (e.g., 1.2.3.4 → 4.3.2.1) and checks several DNS blacklists by querying 4.3.2.1.zen.spamhaus.org, etc.
- If an answer is returned, the IP is blacklisted on that DNSBL.
- fetch_webpage_metadata(url
- Fetches a webpage’s <title>, meta description, and meta keywords to provide quick SEO context.
- settings() / change_color()
- Provides a submenu to alter the default console color for script output.
THIS TOOL IS NOT PERFECT. THERE IS STILL ROOM FOR IMPROVMENT, AND I AM WORKING ON ADDING NEW FEATRURES AND REFINING IT. SOMETIMES A USERNAME SEARCH WILL RESULLT IN A FALSE PPOSITIVE AND/OR THE URL WILL NOT RESOLVE. IT HAS BEEN TESTED AND IS ACCURATE, BUT NOT 100% ACCURATE. VERIFY THE OUTPUTS IF YOU ARE NOT SURE.
Contributing
- Fork this repository`
- Create a new Pull Request
We welcome any improvements or additional OSINT features!
License
This project is released under the Apache 2.0 License.