Chrysler falls victim to Everest Ransomware
Incident Overview
The Everest ransomware group claims to have successfully breached Chrysler, a major automotive manufacturer, and obtained 1088 GB of the organization's internal data. The threat actor has publicly announced their intention to publish the stolen data within 6-7 days if their demands are not met.
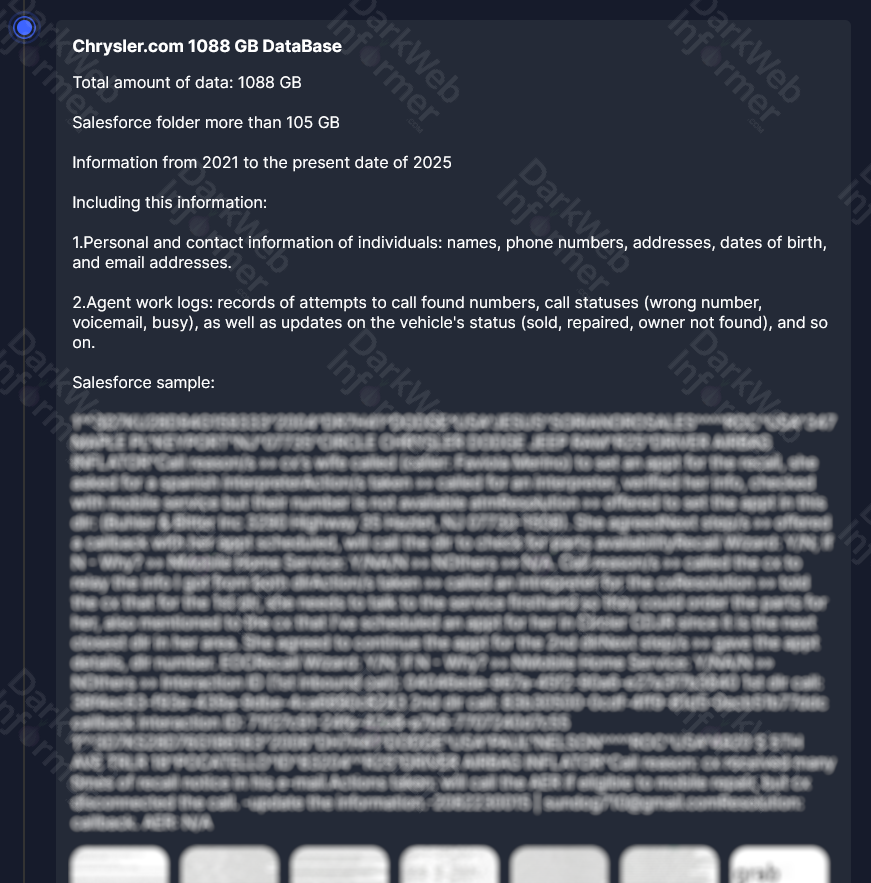
According to the information available from the ransomware group's leak site, the compromised data includes substantial volumes of sensitive corporate information. The 1088 GB dataset reportedly contains:
- Personal and contact information of individuals, including names, phone numbers, addresses, dates of birth, and email addresses
- Salesforce folder containing more than 105 GB of data
- Agent work logs with records of customer interactions, call statuses, and vehicle status updates from 2021 to present (2025)
- Internal communications and operational data
The threat actor has provided sample data demonstrating the authenticity of their claims, including detailed customer interaction logs from Chrysler dealerships showing agent communications, customer service records, and vehicle sales information.
Ransomware attacks on major manufacturing organizations like Chrysler pose significant risks not only to the company's operations but also to customer privacy, as evidenced by the exposed personal information. The incident highlights the ongoing threat posed by sophisticated ransomware groups targeting large enterprises in the automotive sector.
This breach has been classified as medium severity. Organizations in the manufacturing sector should review their security postures and ensure proper backup and incident response procedures are in place.
Unlock Full Breach Intelligence
Premium subscribers gain access to PLUS, PRO, or ELITE features, including breach claim URLs and fully unredacted threat and ransomware feeds with no blur, along with leak and breach coverage, 500+ onion and clearnet resources, uptime monitoring, high-resolution watermark-free images, and more.
API Access for Researchers & Security Teams
SOC teams, researchers, and security professionals can integrate Dark Web Informer's threat intelligence directly into their workflows via API. Access real-time breach data, threat feeds, and monitoring capabilities programmatically.
Learn About API AccessDark Web Informer © 2025 | Cyber Threat Intelligence | DarkWebInformer.com