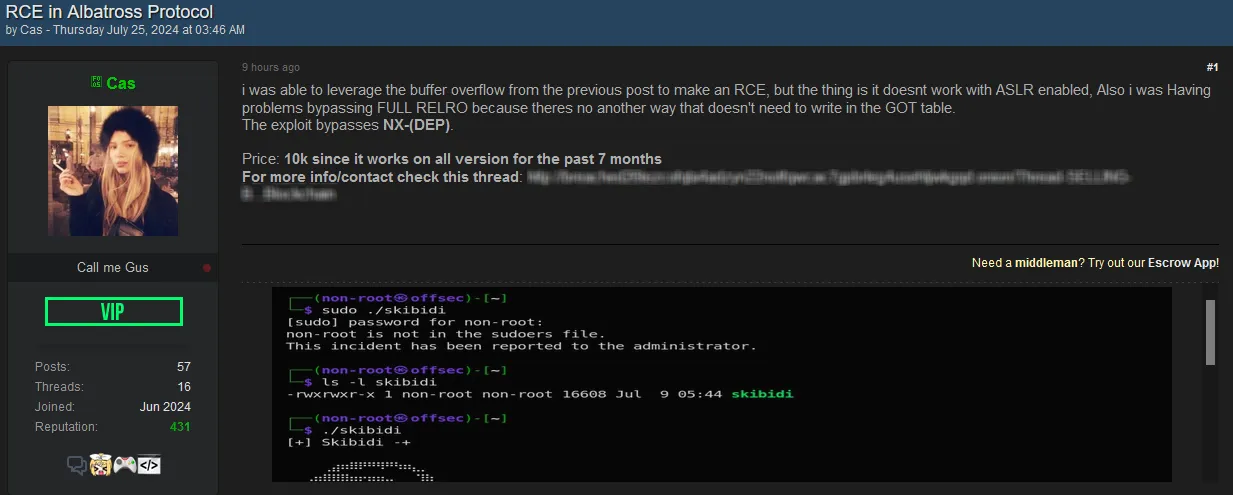
- Username: Cas
- Display Name: Call me Gus
- VIP Status: VIP
- Posts: 57
- Threads: 16
- Joined: June 2024
- Reputation: 431
Listing Details:
- Description:
- Cas was able to leverage a buffer overflow from a previous post to create a Remote Code Execution (RCE) exploit.
- The exploit does not work with ASLR enabled and has issues bypassing FULL RELRO, as it needs to write in the GOT table.
- The exploit bypasses NX (DEP).
Pricing:
- Price: 10k (since it works on all versions for the past 7 months)
(non-root@offsec)-[~]
$ sudo ./skibidi
[sudo] password for non-root:
non-root is not in the sudoers file.
This incident has been reported to the administrator.
(non-root@offsec)-[~]
$ ls -l skibidi
-rwxrwxr-x 1 non-root non-root 16608 Jul 9 05:44 skibidi
(non-root@offsec)-[~]
$ ./skibidi
[+] Skibidi ++