Link: https://breachbase.com/
In the underworld of data, knowledge is power. And when it comes to understanding the vast ocean of exposed credentials, few resources are as invaluable as BreachBase. For those of us who live and breathe the digital underground, BreachBase is not just another tool—it's the ultimate playground.
What is BreachBase?
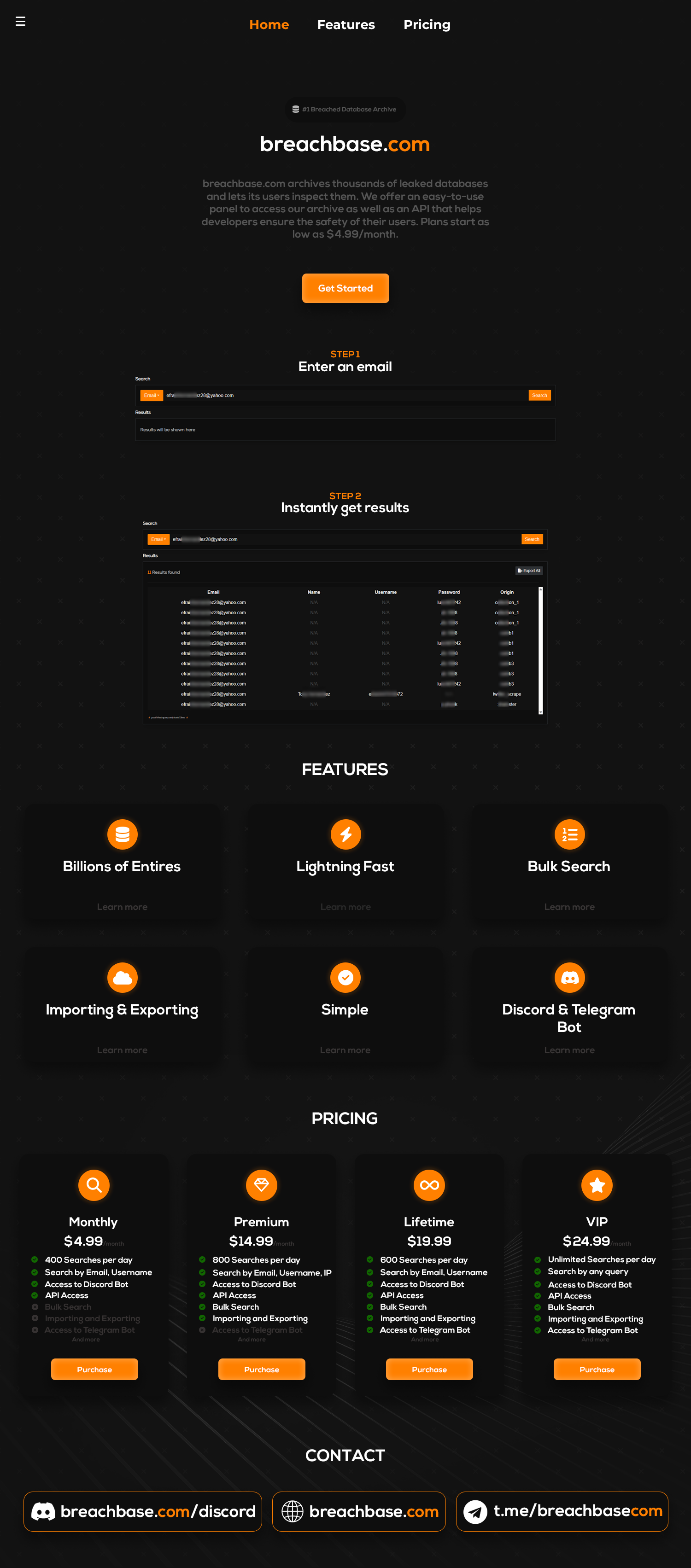
BreachBase is a go-to resource for anyone serious about navigating the chaotic world of data breaches. It’s a treasure trove of exposed data, collated from some of the biggest breaches out there. We're talking about billions of email addresses, passwords, and personal details—all laid bare for those who know where to look.
Unlike your typical pastebin or leaky forum, BreachBase is meticulously organized. It’s not just a dump of random data; it’s a curated collection that’s easy to search, analyze, and exploit. Whether you're looking for specific user accounts, building a wordlist for your next pentest, or simply keeping an eye on the latest breaches, BreachBase delivers the goods.
Why BreachBase?
In our line of work, speed and accuracy are everything. You need to find the right data fast, and you need to know it’s legit. BreachBase stands out because it offers:
- Massive Database: With billions of records from some of the biggest breaches in history, BreachBase gives you access to a wealth of information. If it’s been breached, it’s probably here.
- Advanced Search Capabilities: No more sifting through endless pages of junk data. BreachBase lets you search by email, domain, password, and more. You get what you need, when you need it.
- Real-Time Updates: The digital landscape is constantly shifting, and BreachBase keeps up. It’s regularly updated with fresh breach data, ensuring you’re always working with the latest intel.
- Data Integrity: Anyone can claim to have breach data, but BreachBase’s reputation for quality ensures you’re accessing clean, accurate data. This isn’t some half-baked list of old credentials; it’s the real deal.
How to Use BreachBase Like a Pro
For those in the know, BreachBase is more than just a database—it’s a tool for both offense and defense. Whether you’re on the hunt for vulnerable accounts or checking if your own credentials have been exposed, the key is in knowing how to leverage the data effectively.
- Credential Stuffing: With billions of username/password combinations at your fingertips, BreachBase is perfect for mounting credential stuffing attacks. Filter by specific targets, then let the data do the talking.
- Reconnaissance: Before launching an attack, understanding your target is crucial. BreachBase lets you gather intel on email addresses, passwords, and more, giving you a solid foundation for your next move.
- Account Takeovers: Find reused passwords and take advantage of weak security practices. BreachBase is a goldmine for discovering credentials that can be used to gain unauthorized access.
- Defensive Measures: On the flip side, BreachBase can be a powerful tool for defending against potential breaches. By monitoring your own domains and email addresses, you can stay ahead of potential threats and take action before they become a problem.
The Dark Side of Data
Let’s not kid ourselves—BreachBase exists in the gray area of legality and ethics. But for those of us who thrive in this space, it’s an indispensable resource. Whether you’re a white-hat testing your own defenses, a black-hat exploiting weaknesses, or somewhere in between, BreachBase offers a glimpse into the vast world of exposed data.
But remember: with great power comes great responsibility. Misusing the data on BreachBase can have serious consequences. Always know the risks, and tread carefully.