GitHub: github.com/presidentbeef/brakeman
Website: brakemanscanner.org
Brakeman is a free, open-source static analysis tool that scans Ruby on Rails applications for security vulnerabilities. Unlike runtime security tools, Brakeman analyzes source code directly—meaning it can identify potential issues at any stage of development without requiring a running application.
What Is Brakeman?
Brakeman performs static analysis on Rails codebases to detect common web application vulnerabilities before they make it to production. It understands Rails patterns and conventions, making it purpose-built for the framework rather than being a generic scanner adapted for Ruby.
The tool is maintained by presidentbeef (Justin Collins) and has accumulated over 7,200 GitHub stars, 150+ contributors, and 4,100+ commits since its creation. It's used in production by organizations including GitHub, Twitter, Groupon, New Relic, and Code Climate.
Installation
Brakeman offers multiple installation methods:
RubyGems:
gem install brakeman
Bundler (development group):
group :development do
gem 'brakeman', require: false
end
Docker:
docker pull presidentbeef/brakeman
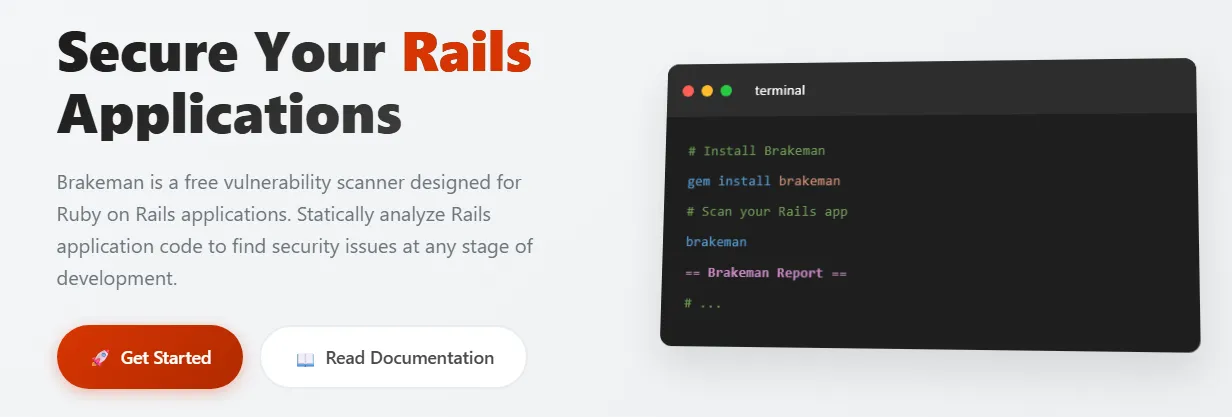
Basic Usage
Running Brakeman is straightforward. From a Rails application's root directory:
brakeman
Or specify a path:
brakeman /path/to/rails/application
For Docker users:
docker run -v "$(pwd)":/code presidentbeef/brakeman
Output Formats
Brakeman supports multiple output formats for integration with various workflows:
- Text (default)
- HTML
- JSON
- JUnit
- Markdown
- CSV
- CodeClimate
- Sonar
- Tabs
Multiple output files can be generated simultaneously:
brakeman -o output.html -o output.json
Compatibility
Brakeman supports Rails versions 2.3.x through 8.x. While it can analyze code written with Ruby 2.0+ syntax, running Brakeman requires Ruby 3.0.0 or higher.
Confidence Levels
Each warning receives a confidence rating:
- High – User input is clearly being used unsafely, or the issue is a straightforward boolean check
- Medium – Unsafe variable usage detected, but the variable may or may not be user input
- Weak – User input was indirectly used in a potentially unsafe manner
Filter by confidence level with the -w flag:
brakeman -w3 # Only high-confidence warnings
Key Features
Selective Scanning: Skip specific checks:
brakeman -x DefaultRoutes,Redirect
Or run only specific tests:
brakeman -t SQL,ValidationRegex
Performance Mode: For faster scans (with potential trade-offs in detection):
brakeman --faster
Comparison Mode: Compare current scan results against a previous report:
brakeman --compare old_report.json
Ignore Configuration: Manage false positives with an ignore file:
brakeman -I
Vulnerability Detection
Brakeman detects numerous vulnerability types including:
- SQL Injection
- Cross-Site Scripting (XSS)
- Command Injection
- Mass Assignment
- Authentication Issues
- Cross-Site Request Forgery (CSRF)
- Dangerous Redirects
- Default Routes
- Dynamic Render Paths
- File Access
- Remote Code Execution
- Session Settings
- Unsafe Deserialization
CI/CD Integration
Brakeman integrates with continuous integration pipelines:
- Jenkins/Hudson plugin available
- Guard plugin for continuous testing
- Multiple GitHub Actions in the marketplace
By default, Brakeman returns non-zero exit codes when warnings are found or errors occur, making it suitable for CI gates. This behavior can be disabled:
brakeman --no-exit-on-warn --no-exit-on-error
Configuration Files
Store Brakeman options in YAML configuration files. Generate a config from current options:
brakeman -C --skip-files plugins/
Output:
---
:skip_files:
- plugins/
Default config locations:
./config/brakeman.yml~/.brakeman/config.yml/etc/brakeman/config.yml
License
Brakeman is free for non-commercial use. The project includes multiple license files covering different use cases.
Resources
- Website: brakemanscanner.org
- GitHub: github.com/presidentbeef/brakeman
- Discussions: GitHub Discussions
Brakeman provides Rails developers with an essential security layer that catches vulnerabilities during development. Its zero-configuration approach, Rails-specific detection, and broad coverage make it a practical addition to any Rails security workflow.