📢 Unlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Get foundational access to breach intelligence — track breaches, leaks, and threats in real-time with unfiltered screenshots and expert summaries.
About the Exploit
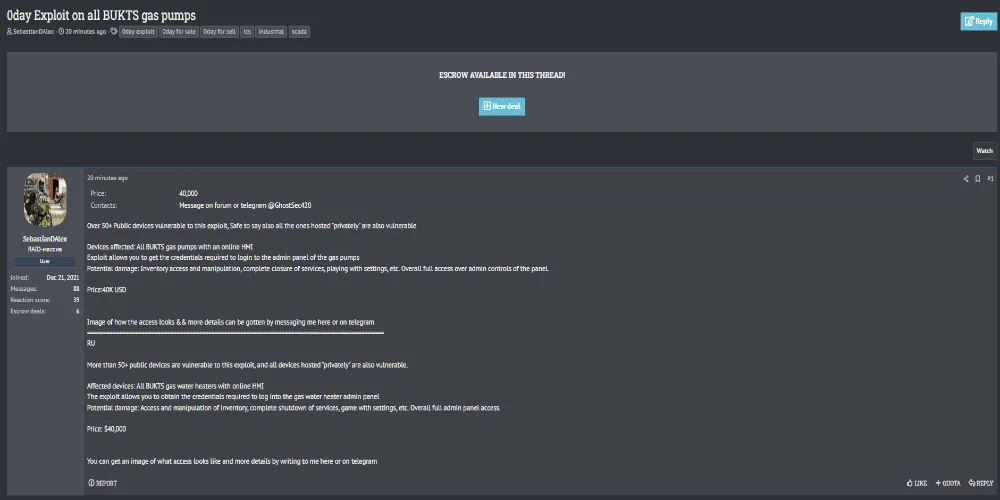
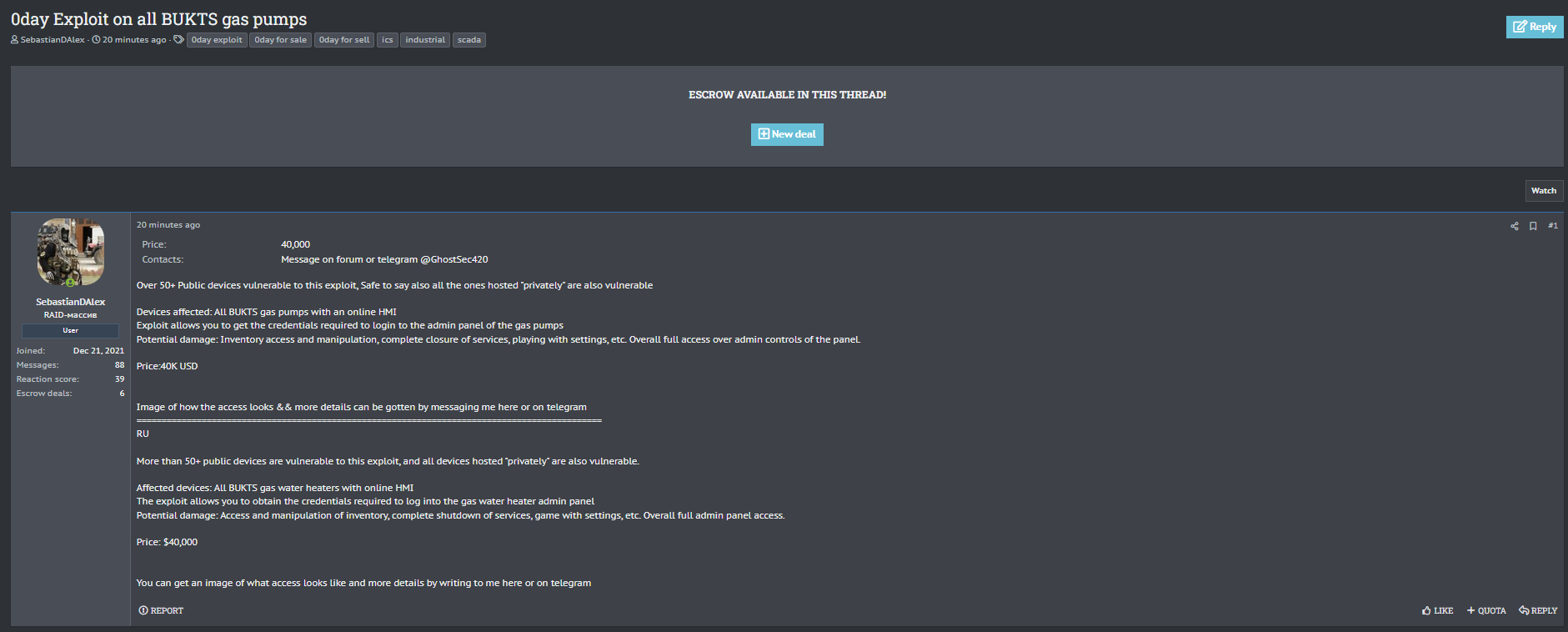
A forum user going by SebastianDAlex has claimed to be selling a zero-day exploit that targets BUKTS gas pumps equipped with online Human-Machine Interfaces (HMI). According to the post, the exploit allows attackers to obtain credentials needed to access the gas pump’s admin panel, effectively giving them full remote control over the systems.
The threat actor claims that over 50 publicly accessible devices are currently vulnerable, and suggests that privately hosted versions of the same devices are also exposed.
⚠️ Disclaimer
Dark Web Informer shares this report for cybersecurity awareness and research purposes only. We do not endorse or support the unauthorized exploitation of industrial control systems (ICS) or SCADA devices.
📌 Overview of the Claim
| Attribute | Details |
|---|---|
| Price | $40,000 USD |
| Devices Affected | All BUKTS gas pumps with online HMI |
| Potential Damage | Inventory manipulation, service shutdown, full admin access, game with settings |
| Delivery | Access credentials for the admin panel |
🧰 Claimed Capabilities
- Obtain credentials for the BUKTS gas pump admin interface
- Full access to inventory controls
- Ability to shut down services remotely
- Modify configuration and system settings
- Control over device operations with no user interaction required
📸 Screenshot Preview
📢 Threat Actor’s Notes
- Escrow is available through the forum to facilitate transactions
- Contact: Forum PM or Telegram (@GhostSec420)
- Additional images and technical details are available upon request via private message
🔗 Claim Post
https://xss.is/threads/142070/
🛡️ Security Implications
Potential Risks
- Compromise of gas station infrastructure
- Disruption of fuel services or manipulation of pump settings
- Inventory tampering or financial fraud
- Use in hacktivism, cybercrime, or ransomware operations targeting ICS environments
Recommended Mitigations
- Immediately audit and restrict online HMI access
- Deploy network segmentation for industrial controls
- Monitor for unauthorized login attempts or abnormal configuration changes
- Apply security patches and update credentials if applicable
💡 Final Thoughts
Attacks on critical infrastructure are becoming increasingly commoditized in underground markets. If this zero-day exploit is legitimate, it represents a serious threat to industrial control systems (ICS) and highlights the urgent need for improved security around Internet-exposed HMI devices.