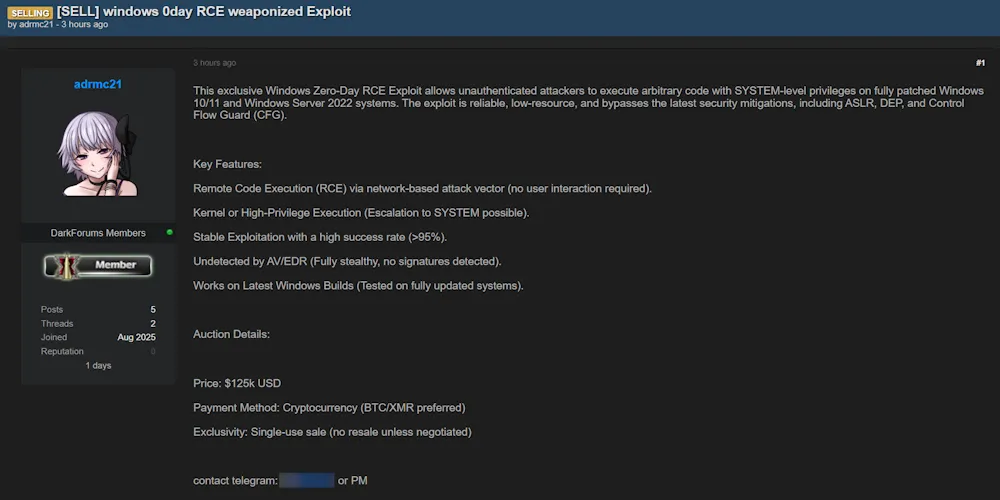
📖 Overview
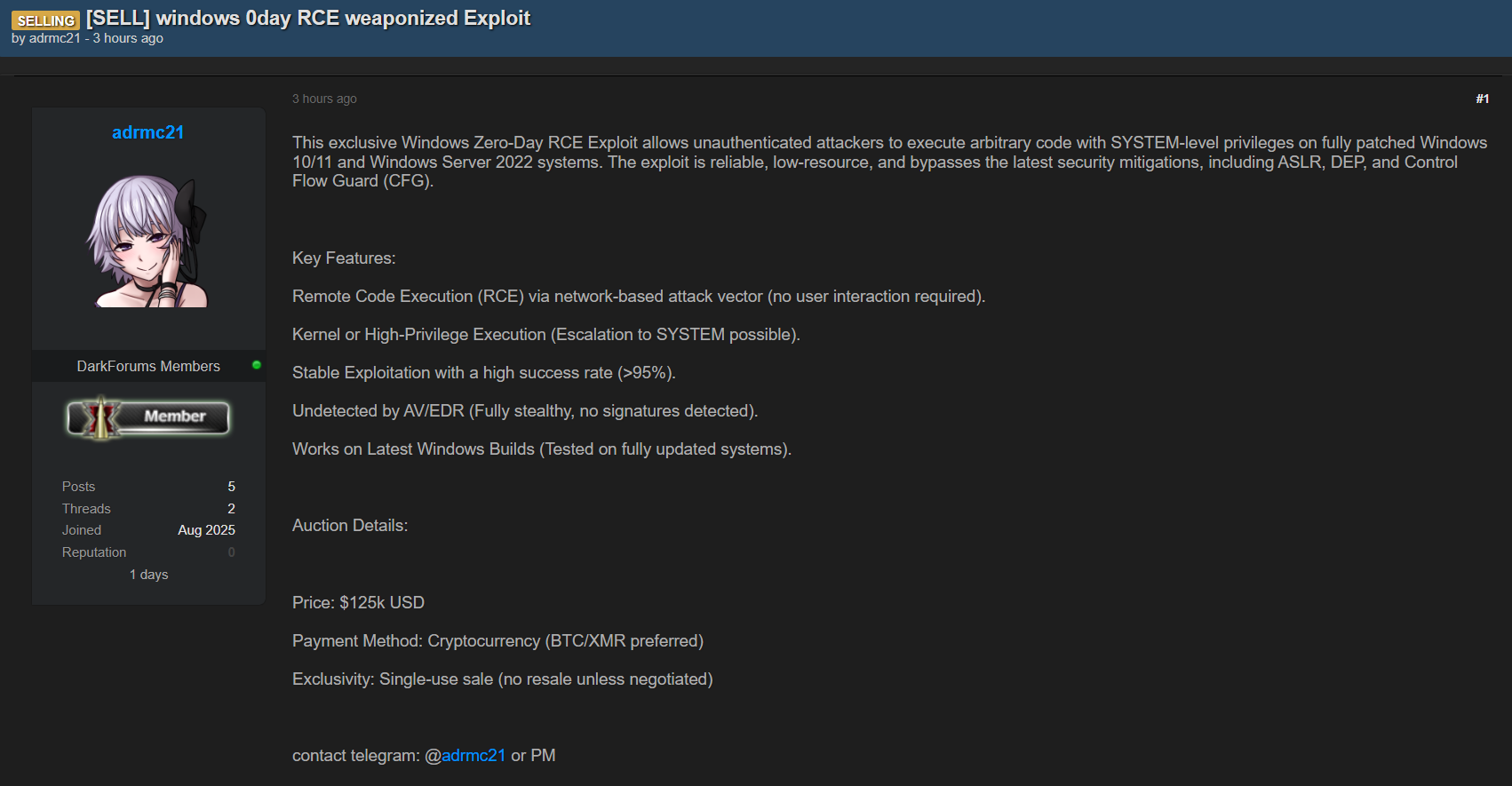
A threat actor is advertising the sale of a Windows zero-day remote code execution (RCE) exploit. The actor claims the exploit provides kernel or high-privilege execution, stable reliability with a high success rate, and evasion of AV/EDR detection. They also state it is compatible with the latest Windows builds, suggesting it could pose a significant risk if legitimate.
📌 Key Details
- Industry: Unknown
- Threat Actor: adrmc21
- Network: openweb
- Category: Vulnerability
- Severity: Low
- Exploit Type: Windows zero-day RCE
- Privilege Level: Kernel or high-privilege execution (claimed)
- Reliability: Stable with high success rate (claimed)
- Evasion: AV and EDR bypass (claimed)
- Compatibility: Latest Windows builds (claimed)
- Delivery: Weaponized exploit package (format not specified)
- Price: 125,000$
🔗 Claim Post (Plain Text)
Claim Post: Available on the Threat Feed for subscribers.
📸 Screenshot Preview
🛡️ WhiteIntel.io Access Infostealers Check
This section is available exclusively for paid subscribers in the Ransomware/Threat Feed posts.
🧩 TTPs (MITRE ATT&CK Mapping)
- TA0001 – Initial Access: Exploitation of public-facing applications
- TA0002 – Execution: Use of weaponized exploit for arbitrary code execution
- TA0004 – Privilege Escalation: Kernel or high-privilege execution
- TA0005 – Defense Evasion: Avoiding AV/EDR detection
👤 Threat Actor Profile: adrmc21
Summary
- Total Matches: 1
- First Seen: 2025-08-19
- Last Seen: 2025-08-19
- Data Start: 2024-10-02
- Countries: –
- Industries: –
📊 Threat Actor Activity
| Date | Country | Sector / Industry | Type | Target / Exploit | Network |
|---|---|---|---|---|---|
| 2025-08-19 | Unknown | – | Vulnerability | Windows Zero-Day RCE Exploit | openweb |
🚨 Potential Risks
If legitimate, the sale of a Windows zero-day exploit is highly dangerous. Such an exploit could enable attackers to fully compromise systems, bypass security tools, and move laterally within networks. It creates the possibility of widespread malware campaigns, ransomware attacks, and espionage activity targeting both enterprises and individuals.
✅ Recommended Security Actions
- Apply the latest Microsoft security patches as soon as they are released
- Monitor for abnormal process execution or privilege escalation attempts
- Enforce endpoint monitoring and logging for suspicious exploit behavior
- Segment critical systems to reduce the blast radius of a potential compromise
- Conduct red-team testing and simulate RCE exploit attempts to identify weak points
💡 Final Thoughts
Zero-day vulnerabilities represent some of the most severe risks in cybersecurity because defenders have no prior warning. While many advertised exploits are fraudulent, even the possibility of a working Windows RCE zero-day appearing in underground markets is alarming. Continuous monitoring, layered defenses, and rapid patching remain critical to reducing exposure to these types of high-impact threats.