Alleged Sale of Unauthorized Admin Panel and Shell Access to UK Magento E-commerce Store Processing 400+ Monthly Orders
Unlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Quick Facts
Incident Overview
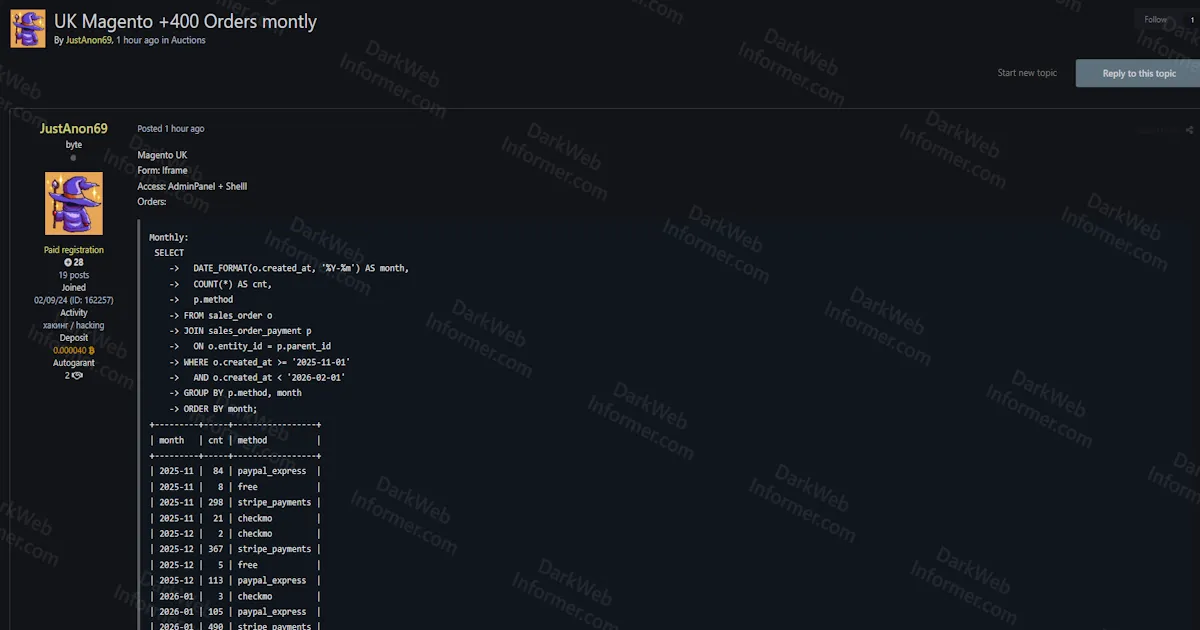
A threat actor using the handle "JustAnon69" has posted an auction listing on the Exploit forum claiming to sell unauthorized access to a UK-based Magento e-commerce store. The listing describes the access as including both admin panel credentials and web shell capabilities, giving a potential buyer full control over the compromised platform.
As proof of the store's value, the threat actor provided SQL query outputs showing monthly and weekly order statistics. The data indicates the store processes over 400 orders per month, with payment methods including Stripe, PayPal Express, and check/money order options. The weekly breakdown shows consistent daily transaction volumes through January 2026, with Stripe payments being the dominant method. The auction starts at $2,000 USD with a $250 step increment and a blitz (buy-it-now) price of $3,500 USD.
This post is for subscribers on the Plus, Pro and Elite tiers
SubscribeAlready have an account? Sign In