Alleged Sale of Unauthorized Access to WEX Corporate Payment System SOAP API Keys
🧩 Standalone API Access Now Available
Access high-volume threat-intelligence data, automated ingestion endpoints, ransomware feeds, IOC data, and more – independently from the above standard subscriptions.
View API AccessUnlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Quick Facts
Incident Overview
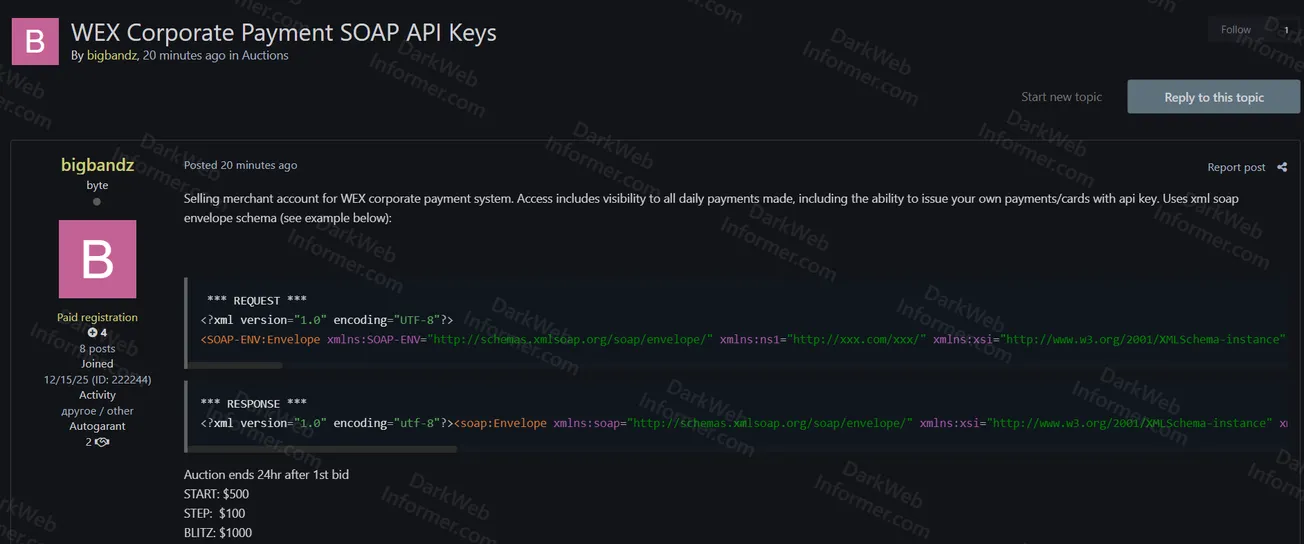
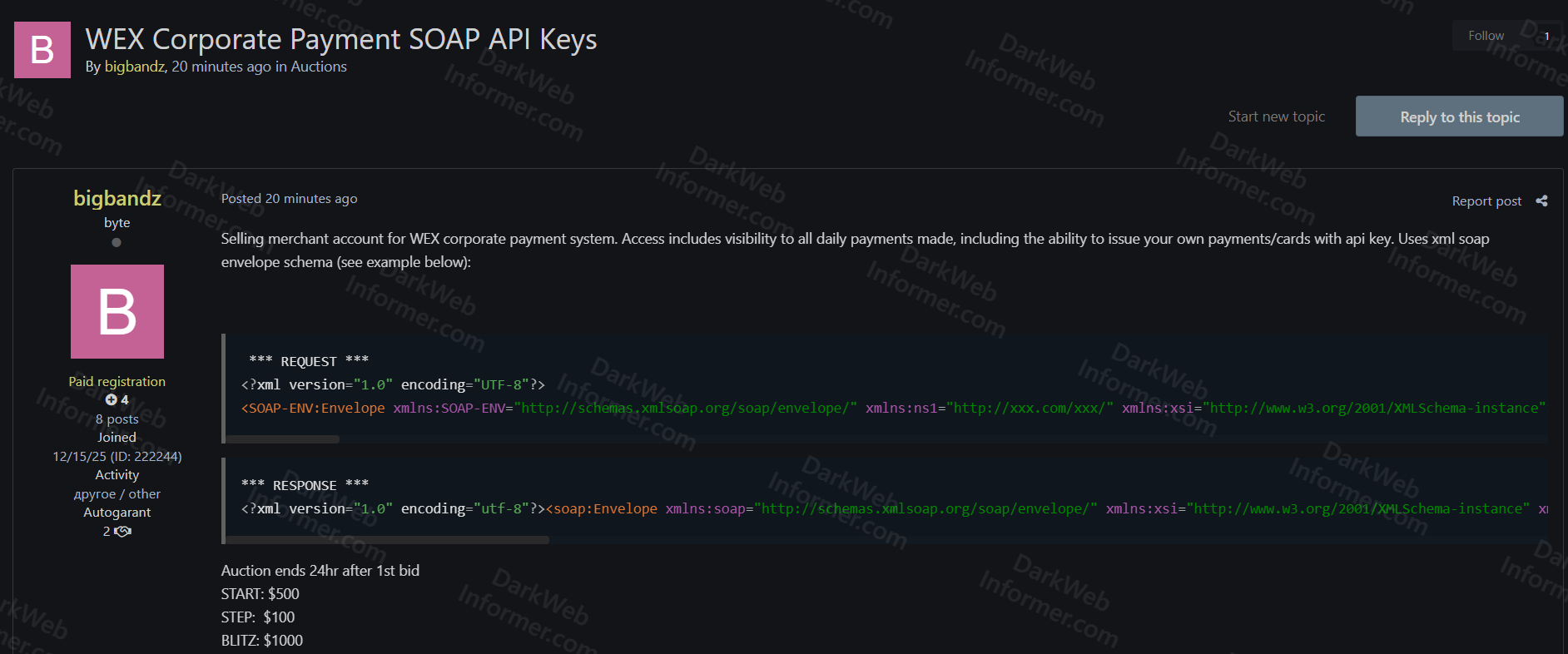
A threat actor using the handle "bigbandz" claims to be selling merchant account access for WEX corporate payment system. The access includes SOAP API keys with visibility to all daily payments made, along with the ability to issue payments and cards using the API key. The system uses XML SOAP envelope schema.
- Access Type: Merchant account for WEX corporate payment system
- API Type: SOAP API Keys using XML envelope schema
- Capabilities: Visibility to all daily payments made through the system
- Fraud Potential: Ability to issue unauthorized payments and cards using the API key
- Example Request: XML version 1.0 with UTF-8 encoding using SOAP-ENV:Envelope schema
- Example Response: XML version 1.0 with utf-8 encoding returning soap:Envelope with XMLSchema-instance
- Auction Details: Ends 24 hours after first bid
- Starting Bid: $500
- Step Increment: $100
- Blitz Price: $1000
Indicators of Compromise (IOCs)
No IOCs were disclosed by the threat actor in this claim.
Breach Claim URL
Unlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Dark Web Informer © 2026 | Cyber Threat Intelligence