Dark Web Informer — Cyber Threat Intelligence
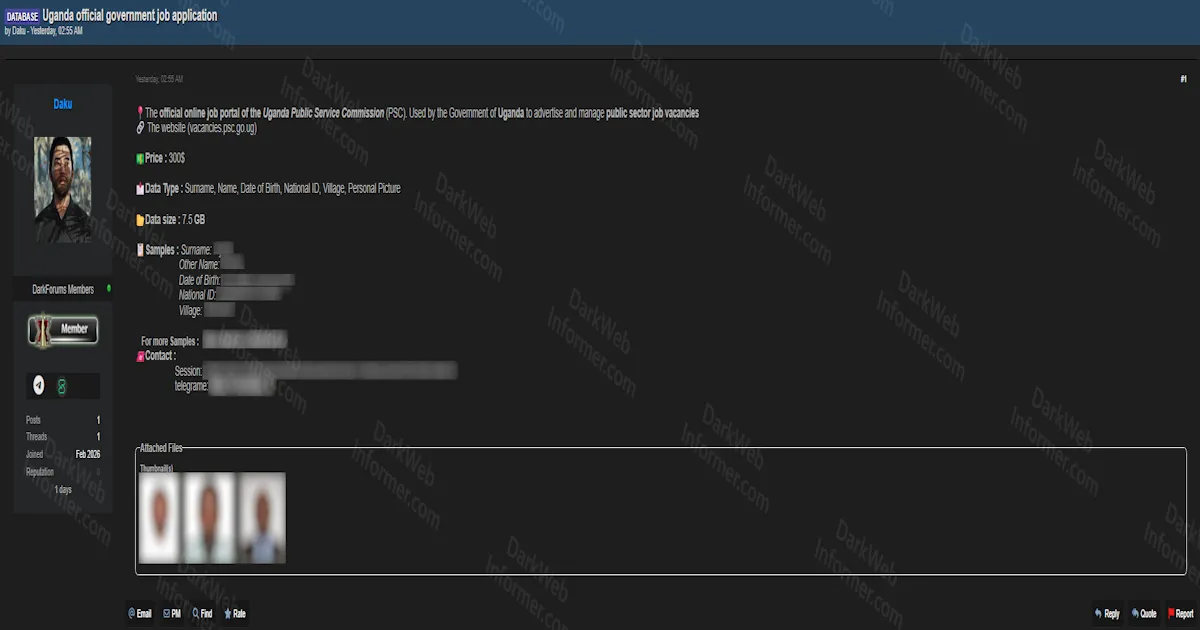
Alleged Sale of Uganda Public Service Commission Job Application Database Containing 7.5 GB of Applicant Records
Unlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
5,100+ Blog Posts (PRO/ELITE)Continuously updated breach reports and threat summaries.
52,200+ Alerts (PRO/ELITE)Daily breach, leak, and DDoS alerts.
Unredacted Threat FeedLive tracking with JSON export.
Leak and Breach CoverageDirect access to claims and posts.
Snippets and Quick FactsConcise summaries of DDoS, defacements, and breaches.
500+ Onion and Clearnet ResourcesVerified index of dark web sites and services.
Real Time Uptime DashboardLive status of 500+ sites.
Whiteintel.io APIIntegrated checks inside breach posts.
High Resolution ImagesUncompressed, watermark free evidence.
Keyword NotificationsBrowser alerts for tracked terms.
Quick Facts
Date & Time
2026-02-01 00:56:20 UTC
Threat Actor
Daku
Victim Country
 Uganda
UgandaIndustry
Government Administration
Victim Organization
Uganda Public Service Commission (PSC)
Victim Site
Category
Data Breach
Severity
🔴 High
Network
Open Web
Victim Profile
Uganda Public Service Commission (PSC)
Government body responsible for public sector recruitment in Uganda Organization
Uganda Public Service Commission
Sector Type
Government
Industry
Government Administration — Public Sector Recruitment
Country
 Uganda
Uganda Domain
Claimed Data Size
7.5 GB
Description
The Public Service Commission is a constitutional body established under the Ugandan Constitution. It manages recruitment, confirmation, and discipline of public officers in the Ugandan civil service. The affected portal handles online job applications from citizens seeking government employment.
Incident Overview
A threat actor using the handle "Daku" has posted a listing claiming to sell a database from the Uganda Public Service Commission (PSC) online job application portal. The PSC is the official government body responsible for advertising and managing public sector job vacancies in Uganda, operating at vacancies.psc.go.ug.