📢 Unlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Get foundational access to breach intelligence — track breaches, leaks, and threats in real-time with unfiltered screenshots and expert summaries.
About the Exploit:
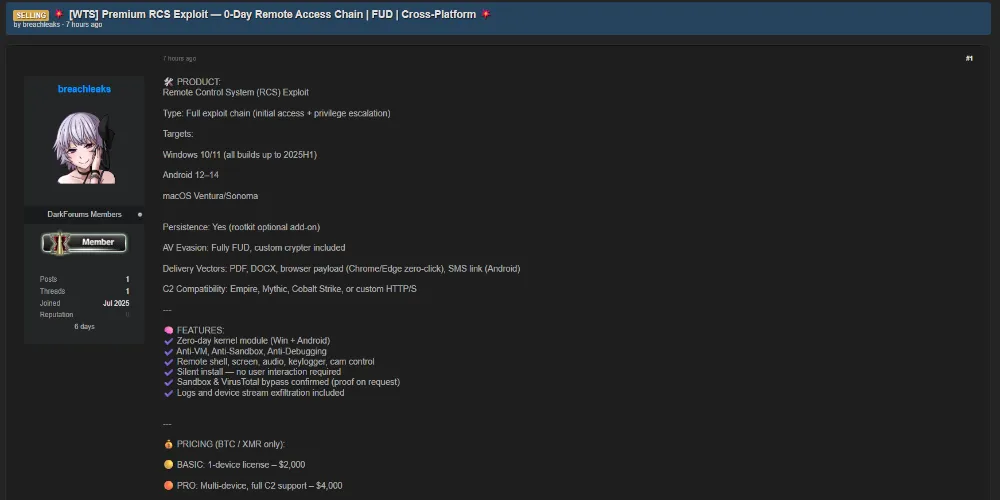
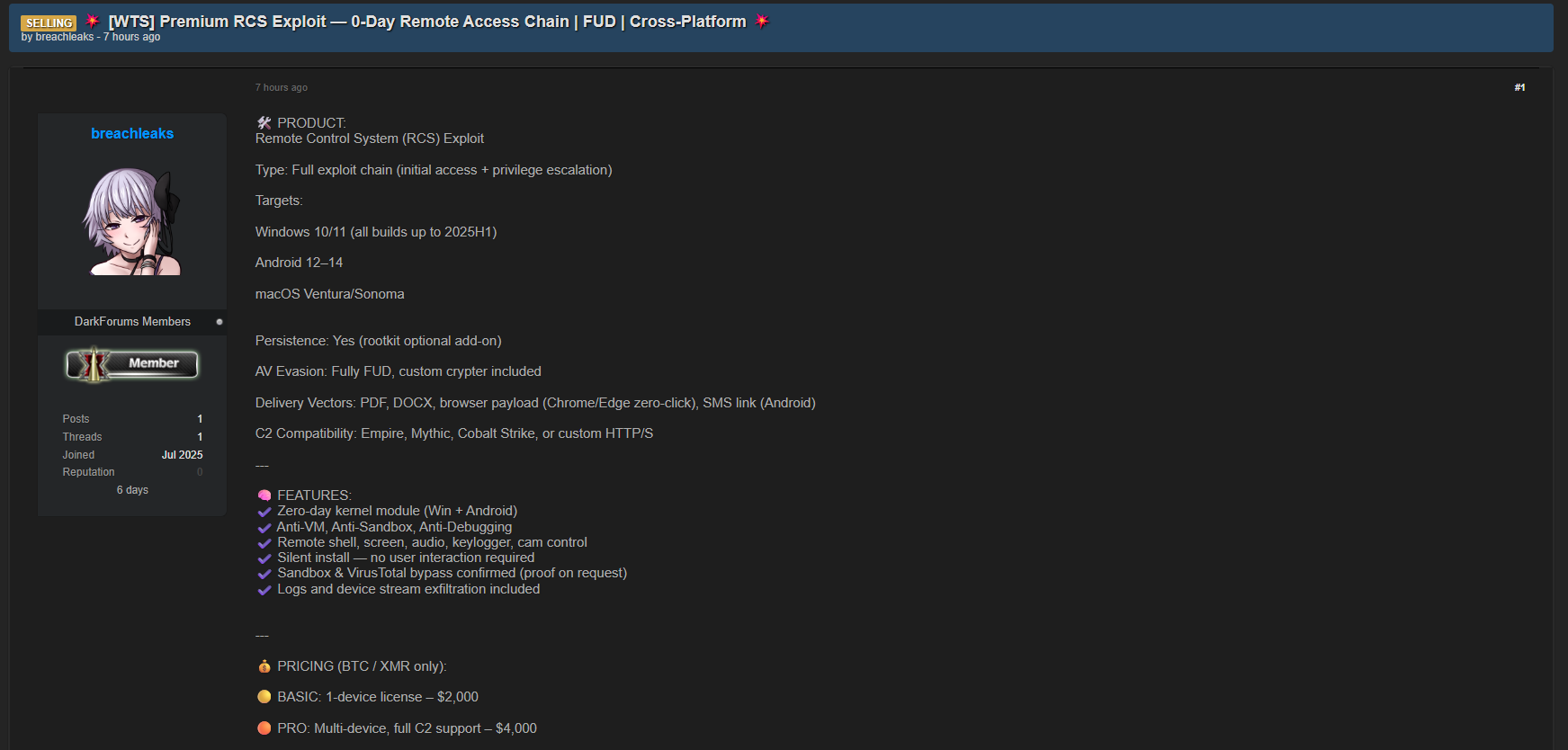
A threat actor using the alias breachleaks is advertising a Remote Control System (RCS) Exploit Chain for sale on an underground forum.
This zero-day exploit allegedly enables:
- Initial Access & Privilege Escalation
- Persistence with optional rootkit
- Fully Undetectable (FUD) execution with sandbox/VM/antivirus evasion
- Cross-platform targeting of Windows, Android, and macOS systems
⚠ Disclaimer
This report includes actual screenshots and/or text from dark web listings. Dark Web Informer explicitly condemns the unauthorized use of security vulnerabilities for malicious purposes. This content is shared for cybersecurity awareness and research only.
📌 Overview
The exploit is advertised as a full chain, affecting the following targets:
| Platform | Details |
|---|---|
| Windows | Windows 10/11 (all builds up to 2025 H1) |
| Android | Android 12–14 |
| macOS | Ventura, Sonoma |
🧰 Features
| Capability | Description |
|---|---|
| Persistence | Yes (with optional rootkit) |
| AV Evasion | Fully FUD, custom crypter included |
| Delivery Vectors | PDF, DOCX, browser payload (Chrome/Edge zero-click), SMS (Android) |
| C2 Compatibility | Empire, Mythic, Cobalt Strike, Custom HTTP/S |
🔧 Additional Highlights
- Zero-day kernel module support (Windows + Android)
- Anti-VM, Anti-Sandbox, Anti-Debugging measures
- Remote shell, screen capture, audio, keylogger, webcam, full cam control
- Silent install – no user interaction required
- Sandbox & VirusTotal bypass confirmed (proof available upon request)
- Logs and live device stream exfiltration included
💰 Pricing (BTC/XMR Only)
| Package | Price |
|---|---|
| BASIC | $2,000 (1-device license) |
| PRO | $4,000 (Multi-device, full C2 support) |
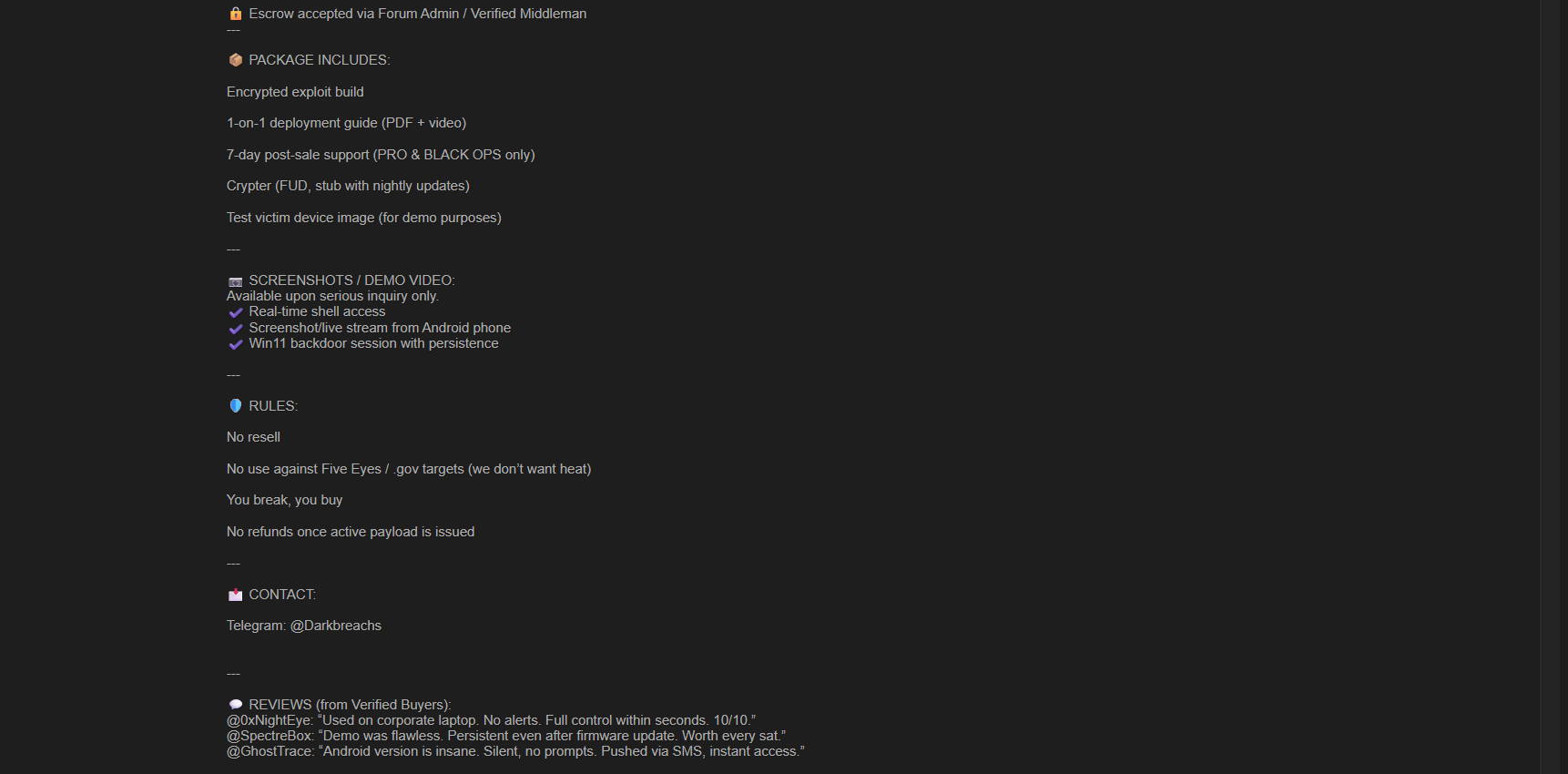
📦 Package Includes
- Encrypted exploit build
- 1-on-1 deployment guide (PDF + Video)
- 7-day post-sale support (PRO only)
- FUD Crypter (stub with nightly updates)
- Test victim device image (demo purposes)
📸 Screenshot Preview
📢 Threat Actor’s Notes
- Escrow: Accepted via forum admin/verified middleman
- Rules:
- No resell
- No use against Five Eyes or government targets
- No refunds once payload is delivered
- Contact: Telegram (redacted in screenshots for safety)
📝 "Verified Buyer Reviews"
| Buyer | Feedback |
|---|---|
| @0xNightEye | "Used on corporate laptop. No alerts. Full control within seconds. 10/10." |
| @SpectreBox | "Demo was flawless. Persistent even after firmware update. Worth every sat." |
| @GhostTrace | "Android version is insane. Silent, no prompts. Pushed via SMS, instant access." |
🔗 Claim Post (Plain Text)
https://darkforums.st/Thread-Selling-%F0%9F%92%A5-WTS-Premium-RCS-Exploit-%E2%80%94-0-Day-Remote-Access-Chain-FUD-Cross-Platform-%F0%9F%92%A5--18397
🛡️ Security Implications
- Potential Risks:
- Enterprise compromise across Windows, Android, macOS devices
- Use in APT toolkits or offensive red team operations
- Resale in exploit-as-a-service models despite rules
- Mitigation Guidance:
- Monitor for zero-click PDF/DOCX payloads
- Harden EDR and sandbox detection systems
- Deploy behavioral anomaly detection on endpoints
💡 Final Thoughts
This listing highlights the commoditization of advanced cross-platform exploit chains in underground markets. The advertised capabilities, if genuine, pose significant risks to corporate, mobile, and personal device security globally.