📢 Unlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Get foundational access to breach intelligence — track breaches, leaks, and threats in real-time with unfiltered screenshots and expert summaries.
⚠ Disclaimer
This report includes actual screenshots and/or text that may include unredacted personally identifiable information (PII) gathered from publicly available sources. The sensitive information presented within this report is intended solely for cybersecurity awareness and threat intelligence purposes. Dark Web Informer explicitly condemns unauthorized access, distribution, or misuse of the personal data displayed or referenced here. Users must treat exposed data responsibly and ethically.
📌 Overview
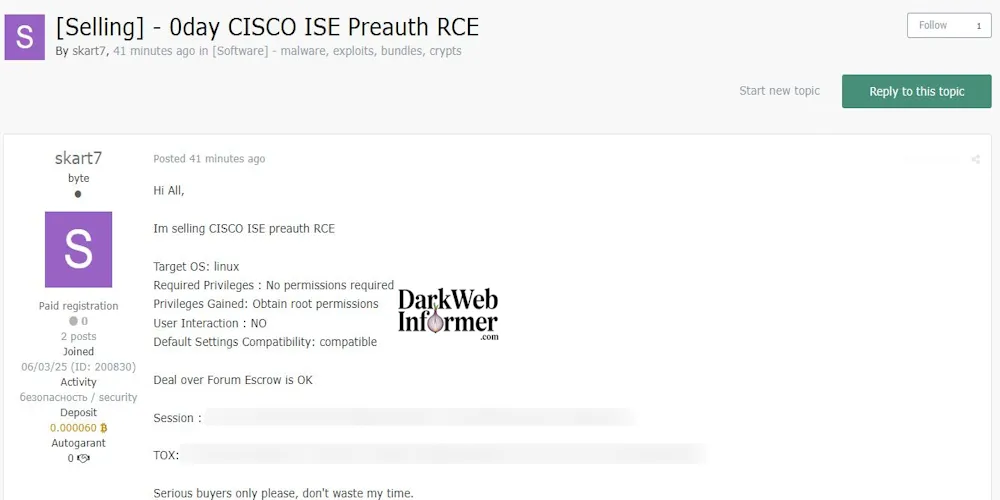
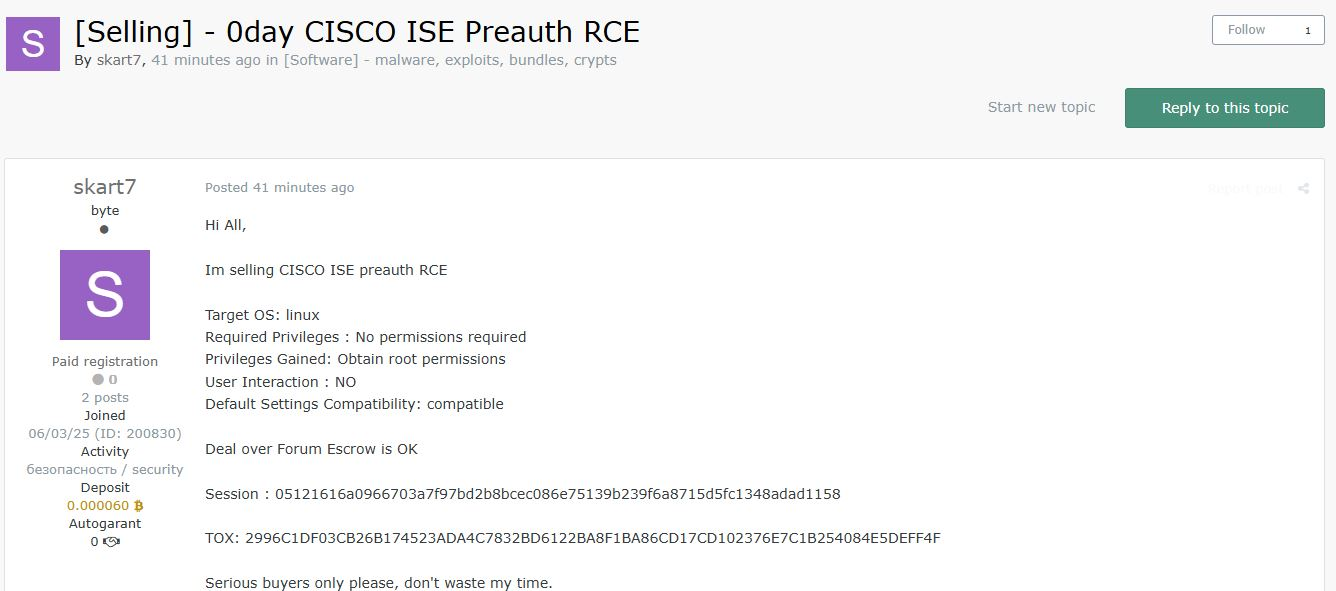
Threat actor skart7 has posted a listing offering a zero-day remote code execution (RCE) exploit targeting Cisco Identity Services Engine (ISE) running on Linux. The exploit is advertised as pre-authentication, requiring no user interaction or credentials, and results in root access upon successful use. Compatibility with default configurations is claimed, suggesting wide applicability to vulnerable deployments.
📊 Key Details
| Attribute | Information |
|---|---|
| Date | 2025-06-04, 01:06:57 PM |
| Threat Actor | skart7 |
| Victim Country | Not specified |
| Industry | Not specified |
| Organization | Cisco |
| Victim Site | Not specified (targets Cisco ISE deployments) |
| Category | Malware (0day Exploit) |
| Severity | Low (targeted, technical, pre-auth RCE) |
| Network | openweb |
Subscriber-only content…
🔗 Claim Post (Plain Text)
https://forum.exploit.in/topic/260306/
📢 Threat Actor’s Claim
Exploit Target:
- Platform: Linux
- Software: Cisco Identity Services Engine (ISE)
- Exploit Type: Remote Code Execution
- Authentication Required: No
- User Interaction: None
- Privilege Gained: Root access
- Compatibility: Default settings confirmed as compatible
Additional Details:
- Deal via forum escrow supported
- Threat actor warns against time-wasters
- Session ID and TOX contact provided:
Session: 05121616a0966703a7f97bd2b8bcec086e75139b239f6a8715d5fc1348adad1158TOX: 2996C1DF03CB26B174523ADA4C7832BD6122BA8F1BA86CD17CD102376E7C1B254084E5DEFF4F
📸 Screenshot
🛡️ WhiteIntel.io Data Leak Information
(No victim site disclosed)
⚔️ Tactics, Techniques, and Procedures (TTPs)
| Tactic | Technique ID | Description |
|---|---|---|
| Initial Access | T1190 | Exploit Public-Facing Application – Cisco ISE exposed to network |
| Execution | T1059 | Execution of remote shell commands (root-level access) |
| Privilege Escalation | T1068 | Exploitation of Vulnerability – Direct root escalation |
🚨 Potential Risks
- High-value infrastructure running Cisco ISE may be silently compromised
- Lateral movement and pivoting into secure networks possible
- Risk of widespread exploitation if vulnerability becomes public
- Cisco infrastructure seen in many enterprise, telecom, and government environments
✅ Recommended Security Actions
- Review Cisco ISE deployments and restrict external access
- Implement network-level protections and EDR to detect anomalous behavior
- Apply available patches if/when official CVE or advisory is issued
- Monitor exploit forums and underground markets for proof-of-concept weaponization
💡 Final Thoughts
This listing highlights an increasing trend of pre-authentication vulnerabilities targeting network security appliances, which often sit in trusted segments. The exploit's claim of zero permissions, no interaction, and root access make it especially potent for targeted campaigns against unpatched Cisco ISE deployments.
Stay informed at DarkWebInformer.com