Alleged sale of Antivirus/Endpoint Detection and Response Killer
Incident Overview
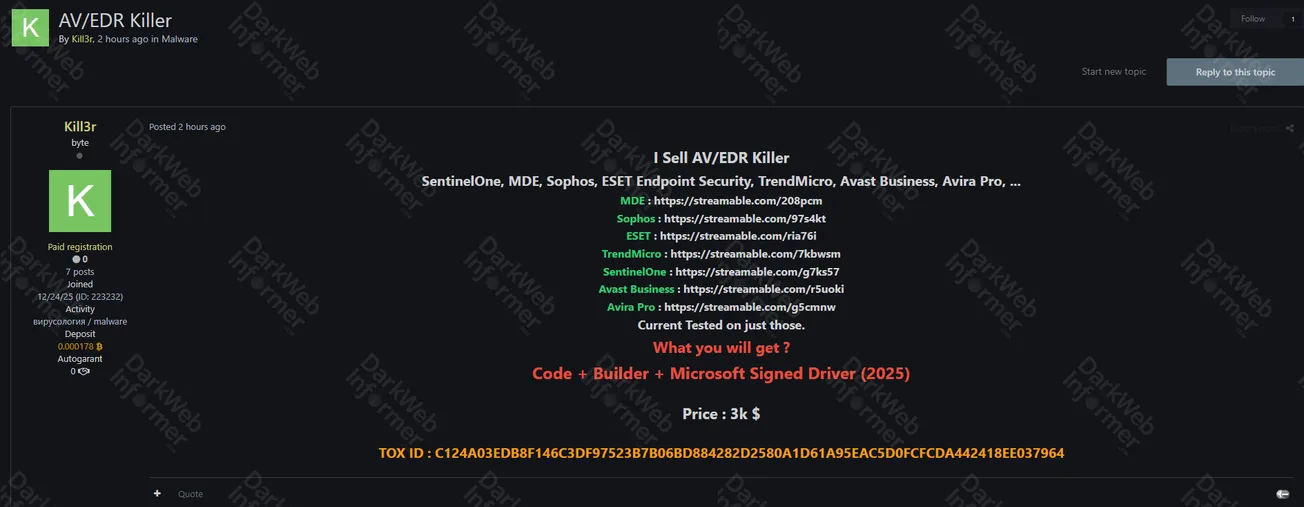
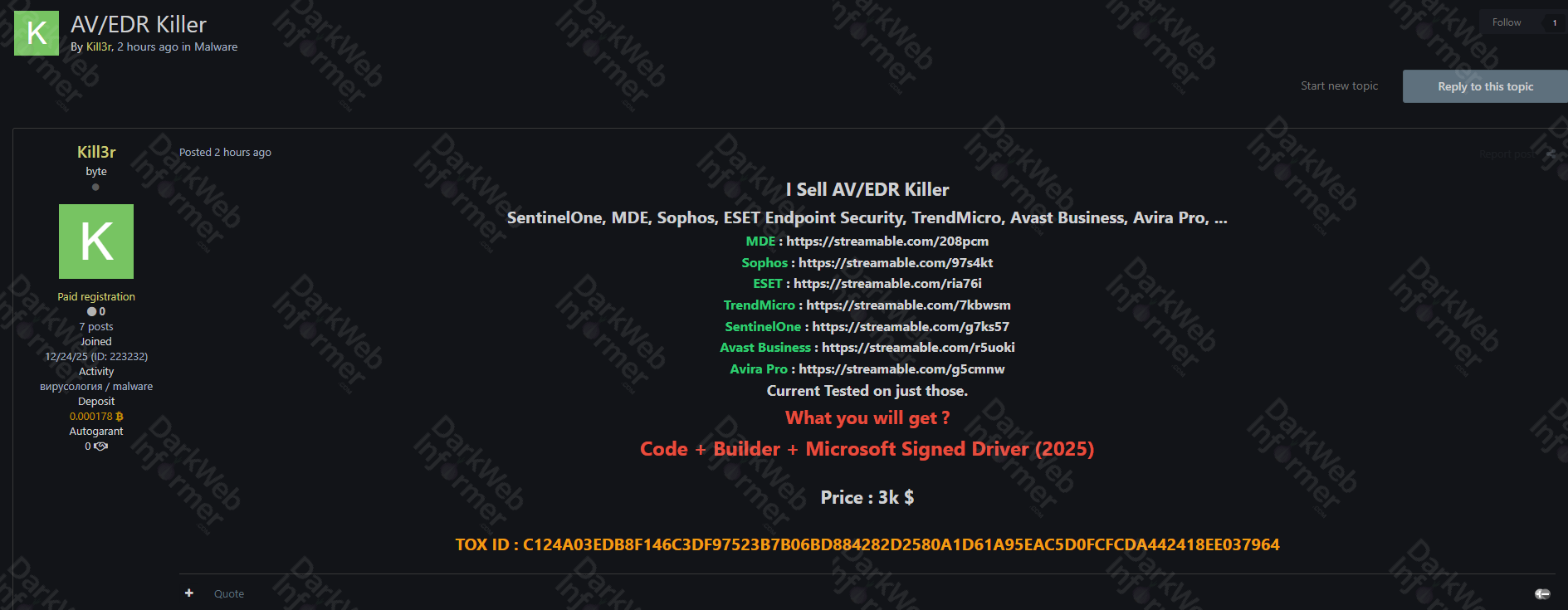
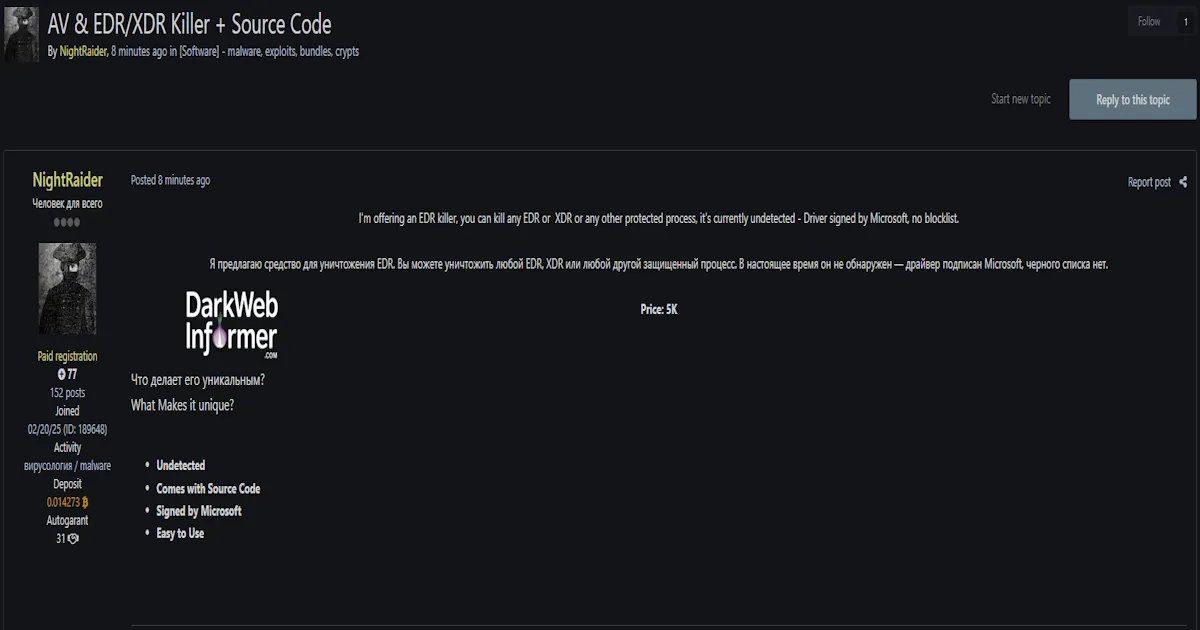
The threat actor claims to be selling an AV/EDR Killer malware tool advertised as capable of disabling and removing multiple enterprise security products. The malware allegedly targets major antivirus and endpoint detection and response (EDR) solutions commonly deployed in corporate environments.
According to the threat actor's advertisement, the tool claims to be effective against the following security products:
- SentinelOne
- Microsoft Defender for Endpoint (MDE)
- Sophos Endpoint Security
- ESET Endpoint Security
- Trend Micro
- Avast Business
- Avira Pro
The offering is advertised as including code, a builder tool, and a Microsoft-signed driver dated 2025. The threat actor claims the tool has been tested against the listed security products. The price is listed at $3,000, with payment details provided via a TOX messaging ID.
Tools designed to disable security software are commonly used by ransomware operators and other threat actors to evade detection and maintain persistence on compromised systems. Such tools often exploit legitimate drivers or use code-signing certificates to bypass security controls.
Unlock Full Breach Intelligence
Premium subscribers gain access to PLUS, PRO, or ELITE features, including breach claim URLs and fully unredacted threat and ransomware feeds with no blur, along with leak and breach coverage, 500+ onion and clearnet resources, uptime monitoring, high-resolution watermark-free images, and more.
API Access for Researchers & Security Teams
SOC teams, researchers, and security professionals can integrate Dark Web Informer's threat intelligence directly into their workflows via API. Access real-time breach data, threat feeds, and monitoring capabilities programmatically.
Learn About API AccessDark Web Informer © 2025 | Cyber Threat Intelligence | DarkWebInformer.com