Unlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Stay in the loop across channels.
Verified PGPs for ransomware and threat groups.
🏢 About the Victim
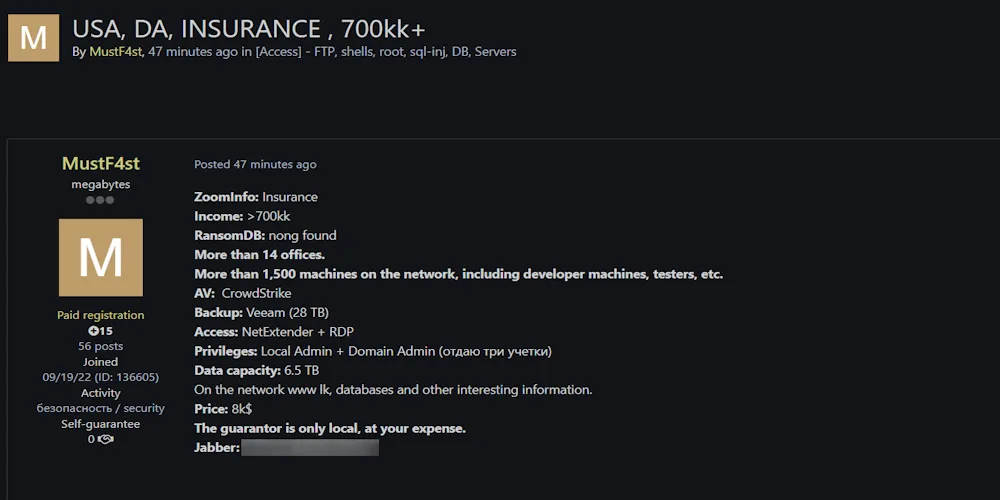
The victim is an unidentified U.S.-based Insurance company, reportedly with more than 14 offices and over 1,500 machines connected to its network. The company’s income is claimed to exceed $700 million.
⚠ Disclaimer
This report includes actual screenshots and/or text that may include unredacted personally identifiable information (PII) gathered from publicly available sources.
The sensitive information presented within this report is intended solely for cybersecurity awareness and threat intelligence purposes.
📌 Overview
On August 21, 2025, a threat actor known as MustF4st advertised unauthorized access for sale to a U.S.-based insurance company.
The actor claimed the access includes NetExtender and RDP with both Local Admin and Domain Admin privileges. Additionally, the company’s environment allegedly has CrowdStrike security deployed and Veeam backups (28TB).
The dataset was priced at $8,000 USD, with access to sensitive systems, databases, and developer/tester machines across the infrastructure.
📊 Key Details
| Attribute | Information |
|---|---|
| Date | 2025-08-21 |
| Threat Actor | MustF4st |
| Victim Country | 🇺🇸 USA |
| Industry | Insurance |
| Victim Org. | Unknown |
| Victim Site | Unknown |
| Category | Initial Access |
| Severity | Medium |
| Network | Openweb |