💡This post is part of Free Post Friday! If you're not a paid subscriber to the platform, these are some of the details you would see if you were a paid subscriber!
💡 Subscribe to DarkWebInformer.com for Unmatched Cyber Threat Intelligence 💡
Take your cybersecurity awareness to the next level with some of these exclusive subscriber-only features:
-
📜
Detailed Threat Posts: Stay updated on breaches, ransomware, DDoS attacks, and more.
-
📡
Exclusive Threat Feeds: Access the latest ransomware victim disclosures, breaches, and other critical updates.
-
🖼️
High-Resolution Screenshots: Gain detailed insights with clarity and precision.
-
🔗
Direct Claim URLs: Instantly access claims with direct links for fast verification.
Why Subscribe? Stay ahead of cyber threats and safeguard your digital assets. Find out all of the exclusive benefits.
Quick Facts:
🔗 DarkWebInformer.com - Cyber Threat Intelligence
📅 Date: 2025-01-03 08:37:42
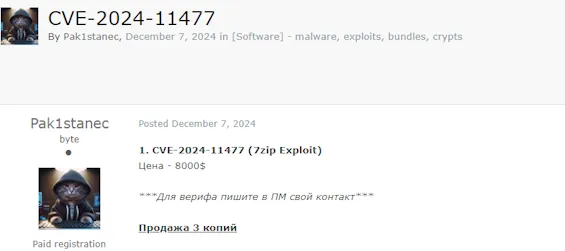
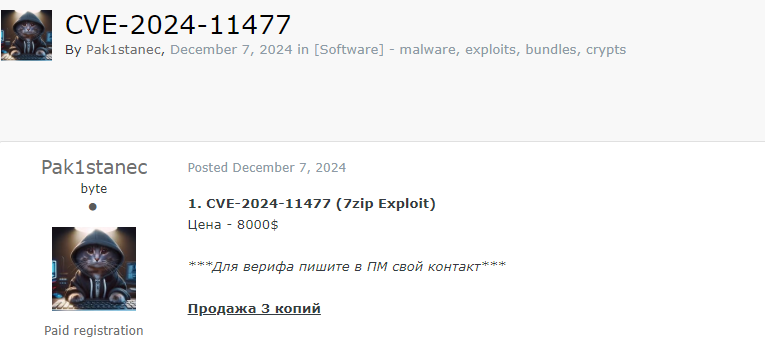
🚨 Title: Alleged Sale of 7zip Exploit CVE-2024-11477
🛡️ Victim Country: Not Specified
🏭 Victim Industry: Not Specified
🏢 Victim Organization: Not Specified
🌐 Victim Site: Not Specified
📜 Category: Vulnerability
🔗 Claim: https://forum.exploit.in/topic/251145/
🕵️♂️ Threat Actor: Pak1stanec
🌍 Network: Openweb
Description:
A threat actor, identified as "Pak1stanec," claims to have an exploit for CVE-2024-11477, a critical vulnerability in the popular file compression software 7zip.
- Exploit Type: Vulnerability in 7zip software
- Price: $8,000 USD
- Availability: Limited to 3 copies
- Verification: Contact required for verification
Analysis:
Potential Impact:
- System Compromise: The exploit could allow unauthorized access or manipulation of systems utilizing 7zip.
- Wide Reach: Due to 7zip's widespread usage, the exploit poses significant risks to various industries.
- Data Breach: Exploitation may result in the unauthorized extraction of compressed and sensitive files.
Severity:
High – The exploit targets a critical vulnerability in a commonly used software, amplifying its threat potential.
Motivation:
Likely financial gain, as the actor is selling the exploit at a premium price.
Recommendations:
For Users and Organizations:
- Immediately update to the latest version of 7zip (if available).
- Limit the use of vulnerable software versions.
- Monitor system logs for signs of exploitation.
For Developers (7zip):
- Patch the vulnerability and release updates promptly.
- Notify users about the potential exploit and recommend immediate updates.
For Authorities:
- Investigate the sale of this exploit and collaborate with cybersecurity experts to mitigate risks.
This incident highlights the persistent threats posed by unpatched vulnerabilities in widely-used software, underlining the need for proactive measures to ensure software security.