⚠ Disclaimer
This report includes actual screenshots and/or text containing unredacted cybersecurity intelligence gathered from publicly available sources. The information presented within this report is intended solely for cybersecurity awareness and threat intelligence purposes. Dark Web Informer explicitly condemns the unauthorized use, distribution, or deployment of exploits and vulnerabilities for malicious purposes. Users must treat this intelligence responsibly and ethically.
📌 Overview
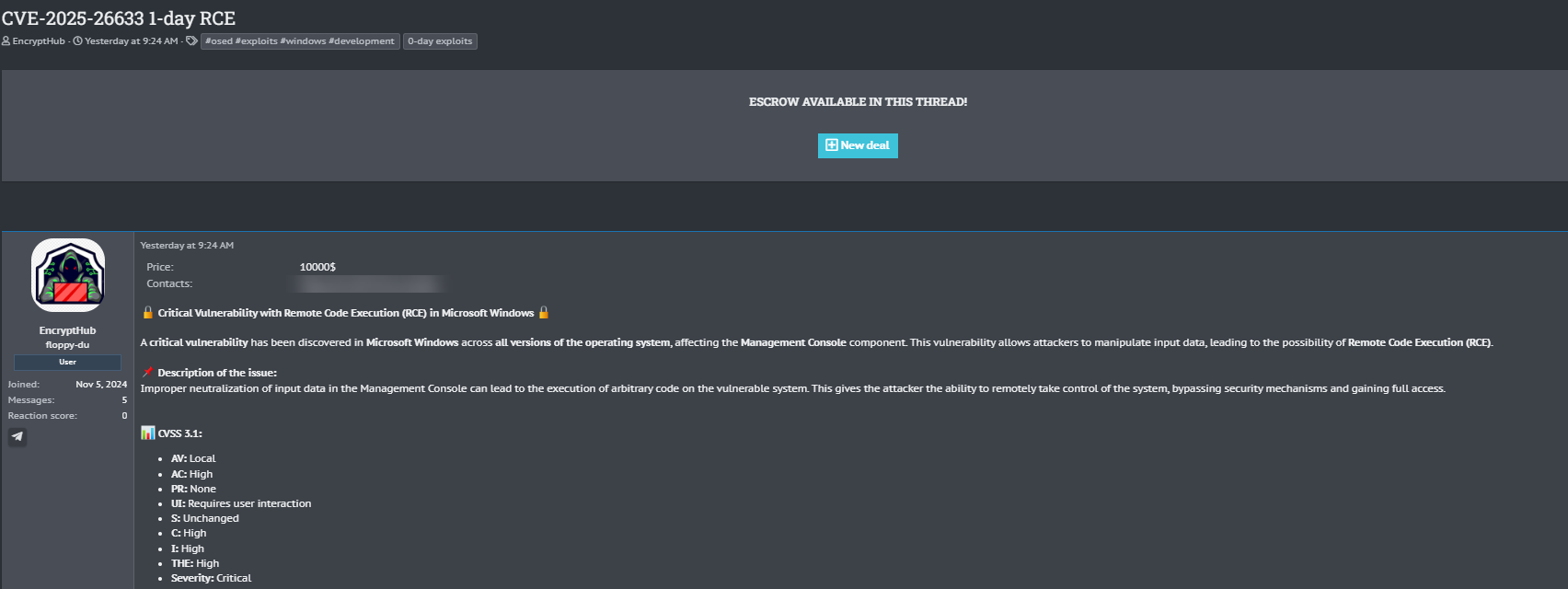
A threat actor known as EncryptHub has listed a 1-day Remote Code Execution (RCE) exploit for sale, allegedly affecting Microsoft Windows. The vulnerability, tracked as CVE-2025-26633, reportedly impacts the Windows Management Console, allowing attackers to manipulate input data and potentially execute arbitrary code on compromised systems.
The exploit is priced at $10,000 USD, with the seller offering escrow services for transactions.
🔑 Key Details
| Attribute | Information |
|---|---|
| 📅 Date | 2025-03-17 16:45:22 |
| 🕵️♂️ Threat Actor | EncryptHub |
| 📜 Category | Malware / Exploit |
| 🌍 Network | Open Web |
| 🖥️ Affected Software | Microsoft Windows (All Versions) |
| 📉 CVSS Score | Critical |
📢 Threat Actor’s Claim – Exploit Breakdown
The forum listing suggests that the exploit allows for:
- Remote Code Execution (RCE) through improper neutralization of input data in the Windows Management Console.
- Privilege Escalation leading to full system compromise with admin access.
- Bypassing Security Mechanisms, including traditional endpoint protections.
- Potential Exploit Chain Usage, enabling further attacks if paired with other vulnerabilities.
🔐 CVSS 3.1 Metrics (As Claimed by Threat Actor)
- Attack Vector: Local
- Attack Complexity: High
- Privileges Required: None
- User Interaction: Requires interaction
- Scope: Unchanged
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
- Threat Level: Critical
📌 Claim URL
XSS Forum Listing
https://xss.is/threads/134565/
📁 Potential Implications – What’s at Risk?
- Enterprise IT Environments – Windows systems across corporate networks could be compromised.
- Cyber Espionage & APTs – The exploit could be leveraged by nation-state actors or criminal groups for targeted attacks.
- Malware Deployment – Attackers could use the vulnerability to install ransomware or persistent backdoors.
- Zero-Day Exploit Chains – This RCE may be paired with other unpatched vulnerabilities for wider-scale attacks.
🚩 Potential Risks – How This Could Impact Organizations & Users
- Widespread Exploitation – If leaked or resold, this exploit could be weaponized by multiple threat actors.
- Critical Windows Vulnerability Exposure – Unpatched systems could be left vulnerable to unauthorized remote control.
- Financial & Operational Damage – Organizations could face data breaches, downtime, and compliance violations.
- Escalation to Zero-Day Status – If a patch is not swiftly issued, this exploit could become a high-value zero-day attack vector.
🚨 Recommended Security Actions – How to Mitigate the Threat
- Apply Security Patches Immediately – If Microsoft releases a patch for CVE-2025-26633, all organizations should apply it without delay.
- Enhance Endpoint Security – Utilize next-gen endpoint protection, such as behavioral-based detection and exploit mitigation tools.
- Monitor for Suspicious Activity – Implement SIEM tools and network traffic analysis to detect potential RCE attempts.
- Restrict User Privileges – Limit administrative privileges to prevent unprivileged processes from escalating access.
- Harden Windows Systems – Disable unnecessary remote access tools and enforce PowerShell logging & application whitelisting.
💡 Final Thoughts – Growing Market for Windows Exploits
The sale of a 1-day RCE exploit for Microsoft Windows demonstrates the persistent demand for critical vulnerabilities in underground cybercrime markets. With Windows being the dominant OS for enterprises and individuals, these types of exploits can have severe consequences if widely adopted by cybercriminals.
Organizations should proactively strengthen defenses, monitor exploit marketplaces, and apply security patches immediately to mitigate risks.
🚨 Stay updated on the latest cyber threats at DarkWebInformer.com









