📢 Unlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Get foundational access to breach intelligence — track breaches, leaks, and threats in real-time with unfiltered screenshots and expert summaries.
⚠ Disclaimer
This report includes actual screenshots and/or text that may include unredacted personally identifiable information (PII) gathered from publicly available sources. The sensitive information presented within this report is intended solely for cybersecurity awareness and threat intelligence purposes. Dark Web Informer explicitly condemns unauthorized access, distribution, or misuse of the personal data displayed or referenced here. Users must treat exposed data responsibly and ethically.
📌 Overview
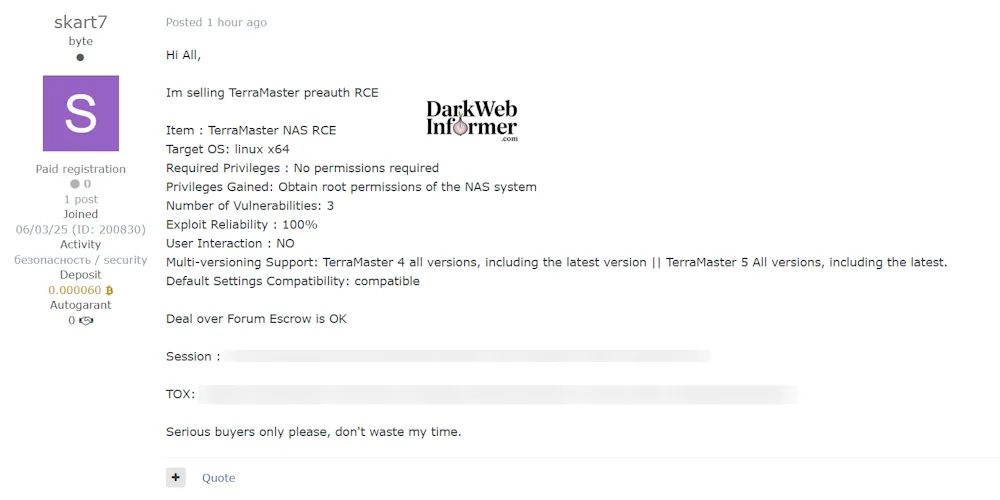
A threat actor operating under the alias skart7 has posted a listing offering a zero-day remote code execution (RCE) exploit targeting TerraMaster NAS devices. The exploit requires no authentication or user interaction, and is said to work on all versions of TOS 4 and TOS 5, including the latest releases. If real, this vulnerability could allow attackers to obtain full root access on affected devices remotely.
📊 Key Details
| Attribute | Information |
|---|---|
| Date | 2025-06-02, 08:54:00 PM |
| Threat Actor | skart7 |
| Victim Country | China |
| Industry | Computer & Network Security |
| Organization | TerraMaster |
| Victim Site | terra-master.com |
| Category | Vulnerability |
| Severity | Low (unconfirmed 0-day with unknown spread) |
| Network | openweb |
Subscriber-only content…
🔗 Claim Post (Plain Text)
https://forum.exploit.in/topic/260187/
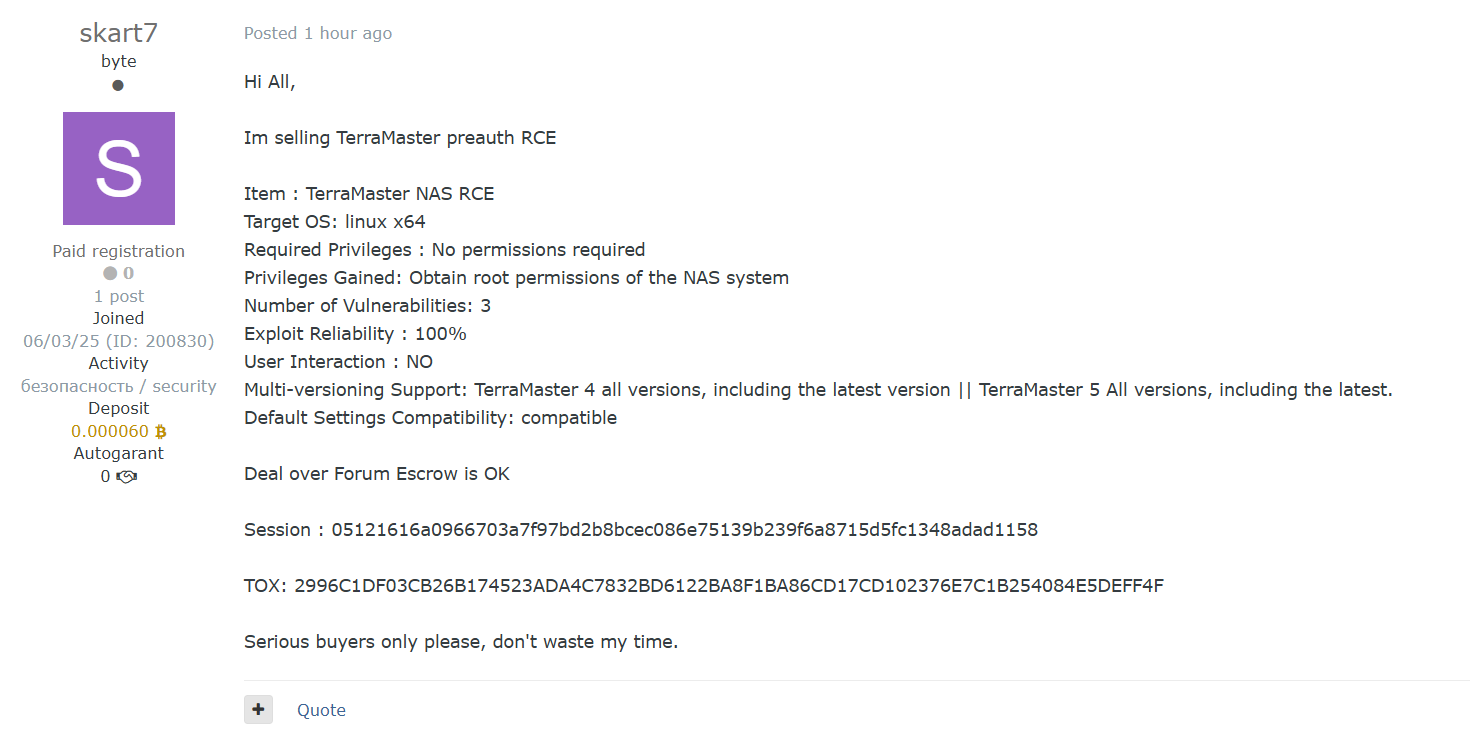
📢 Threat Actor’s Claim
Exploit Details:
- Target: TerraMaster NAS (TOS 4 and 5, all versions)
- Exploit Type: Pre-authentication Remote Code Execution
- Privileges Required: None
- Privileges Gained: Full root access to NAS device
- Exploit Reliability: 100% (claimed)
- User Interaction: None
- Vulnerability Count: 3 underlying issues exploited
- Compatibility: Works under default settings
- Multi-Version Support: All TOS 4 & 5 releases, including the latest
Other Info:
- Forum escrow supported
- TOX and Session contact IDs provided for transaction
- Request for “serious buyers only”
📸 Screenshot
🛡️ WhiteIntel.io Data Leak Information
⚔️ Tactics, Techniques, and Procedures (TTPs)
| Tactic | Technique ID | Description |
|---|---|---|
| Initial Access | T1190 | Exploit Public-Facing Application – Remote attack via NAS web UI |
| Execution | T1059 | Command and Scripting Interpreter – Achieve RCE on Linux target |
| Privilege Escalation | T1068 | Exploitation of Vulnerability – Root-level access on NAS devices |
🚨 Potential Risks
- Full device takeover of unpatched TerraMaster NAS devices
- Remote exfiltration or ransomware deployment without user interaction
- Exploit resale or integration into botnets targeting SMB/home NAS environments
- Possible zero-day status requiring vendor-side investigation
✅ Recommended Security Actions
- Monitor for incoming traffic to NAS ports from unfamiliar IPs
- Temporarily restrict WAN-facing NAS interfaces
- Contact TerraMaster support for official security bulletins
- Conduct firmware integrity and patch validation
- Track and monitor exploit forums for proof-of-concept or resale
💡 Final Thoughts
If validated, this pre-authentication RCE affecting TerraMaster TOS 4 and 5 presents a significant threat to SOHO and SMB environments using NAS solutions. Its combination of stealth, privilege escalation, and reliability make it highly desirable for actors in need of persistence or lateral movement capabilities.
Stay informed at DarkWebInformer.com