📢 Unlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Get foundational access to breach intelligence — track breaches, leaks, and threats in real-time with unfiltered screenshots and expert summaries.
⚠ Disclaimer
This report includes actual screenshots and/or text that may include unredacted personally identifiable information (PII) gathered from publicly available sources. The sensitive information presented within this report is intended solely for cybersecurity awareness and threat intelligence purposes. Dark Web Informer explicitly condemns unauthorized access, distribution, or misuse of the personal data displayed or referenced here. Users must treat exposed data responsibly and ethically.
📌 Overview
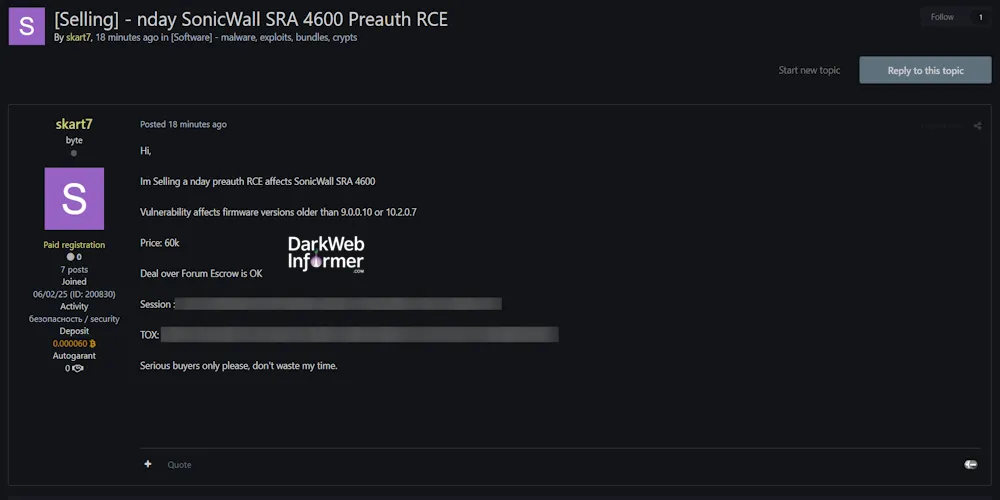
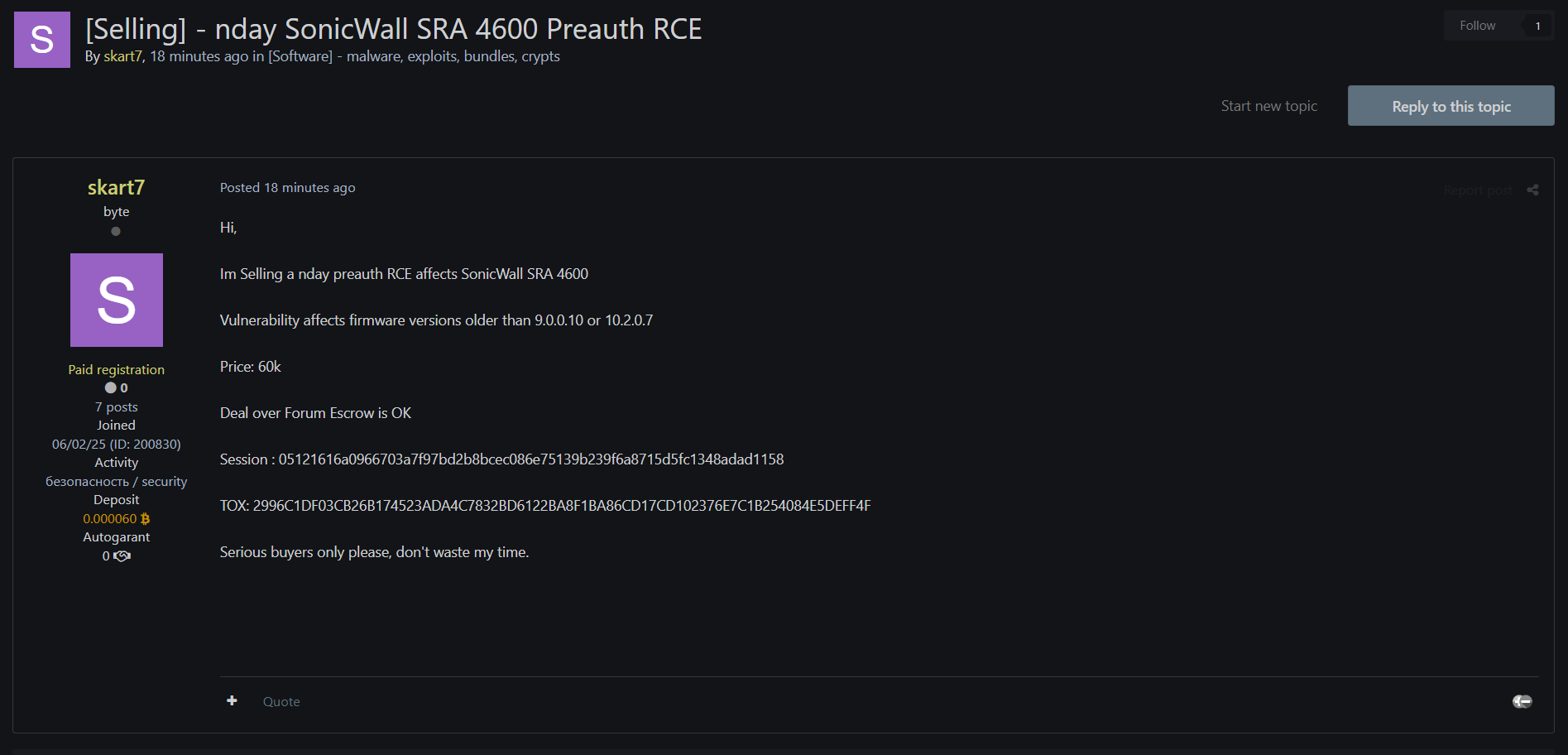
Threat actor skart7 has posted a listing on a cybercrime forum offering a pre-authentication Remote Code Execution (RCE) exploit allegedly affecting SonicWall SRA 4600 devices. This zero-day (nday) vulnerability is said to impact firmware versions older than 9.0.0.10 or 10.2.0.7. The actor claims the exploit is functional and requests a high price of $60,000 USD, accepting escrow-based transactions via the forum.
📊 Key Details
| Attribute | Information |
|---|---|
| Date | 2025-06-08, 7:17:11 PM |
| Threat Actor | skart7 |
| Victim Country | Not specified |
| Industry | Not specified |
| Organization | Not specified |
| Victim Site | Not specified |
| Category | Vulnerability |
| Severity | Low (pending verification) |
| Network | openweb |
Subscriber-only content…
🔗 Claim Post (Plain Text)
https://forum.exploit.in/topic/260540/
Tor Browser recommended for access
📢 Threat Actor’s Claim
- Exploit Type: Pre-auth Remote Code Execution (RCE)
- Target Device: SonicWall SRA 4600
- Affected Versions: Firmware older than 9.0.0.10 or 10.2.0.7
- Price: $60,000 USD
- Transaction Method: Forum escrow accepted
- Contact Methods:
- Session ID: 05121616a0966703a7f97bd2b8bce086e75139b239f6a8715d5fc1348adad1158
- TOX ID: 2996C1DF03CB26B174523ADA4C7832BD6122BA8F1BA86CD17CD102376E7C1B254084E5DEFF4F
- Note: Serious buyers only, no time-wasters
📸 Screenshot
🛡️ WhiteIntel.io Data Leak Information
(No victim site disclosed)
⚔️ Tactics, Techniques, and Procedures (TTPs)
| Tactic | Technique ID | Description |
|---|---|---|
| Initial Access | T1190 | Exploitation of public-facing application vulnerability |
| Execution | T1203 | Exploitation of software vulnerability (Pre-auth RCE) |
🚨 Potential Risks
- Unauthorized remote access to SonicWall VPN appliances
- Potential lateral movement within internal networks
- Exploitable entry point for ransomware or espionage operations
- Supply chain risk if deployed across multiple enterprise clients
- Unpatched appliances could be vulnerable in-the-wild
✅ Recommended Security Actions
- Immediately audit all SonicWall SRA 4600 devices for firmware version
- Upgrade to versions ≥ 9.0.0.10 or ≥ 10.2.0.7 as recommended
- Monitor for unusual activity or external access attempts
- Isolate vulnerable systems and enforce MFA on all remote access points
- Report any exploitation attempts to SonicWall and national CERT authorities
💡 Final Thoughts
The underground sale of a SonicWall SRA 4600 pre-auth RCE highlights the persistent risk posed by unpatched VPN devices in enterprise environments. While the credibility of this particular offering remains unverified, the potential for wide-scale exploitation should prompt immediate defensive measures by any organizations still running outdated firmware.
Stay informed at DarkWebInformer.com