Alleged Data Sale of 1.39 Million Douglas Cosmetics Customer Records
🧩 Standalone API Access Now Available
Access high-volume threat-intelligence data, automated ingestion endpoints, ransomware feeds, IOC data, and more – independently from the above standard subscriptions.
View API AccessUnlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Quick Facts
Incident Overview
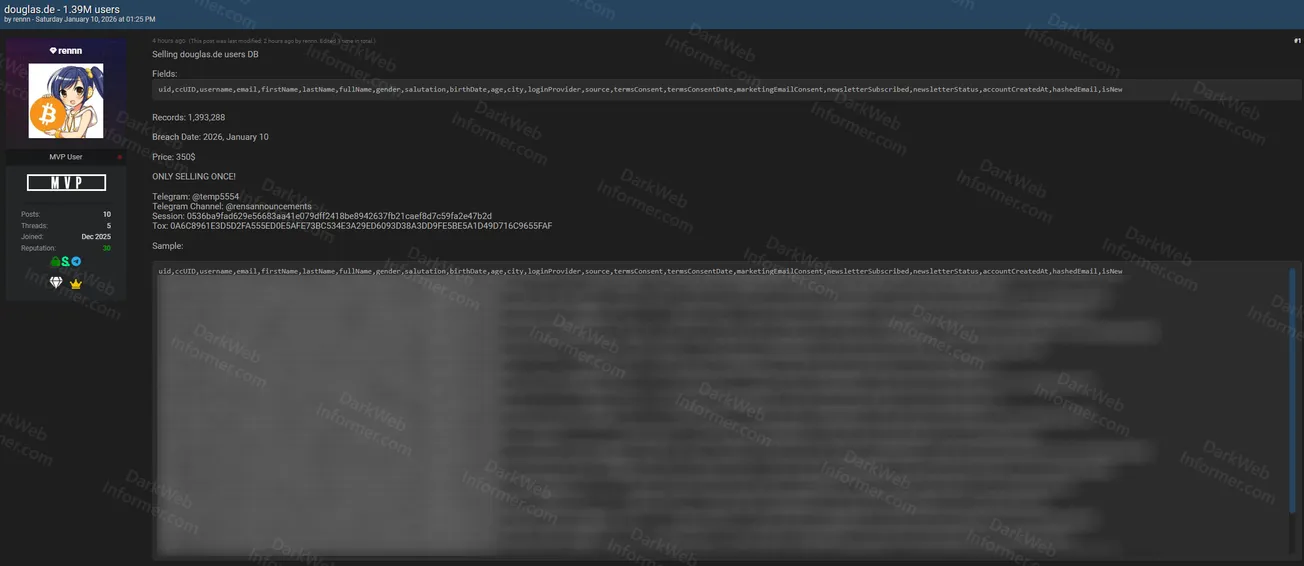
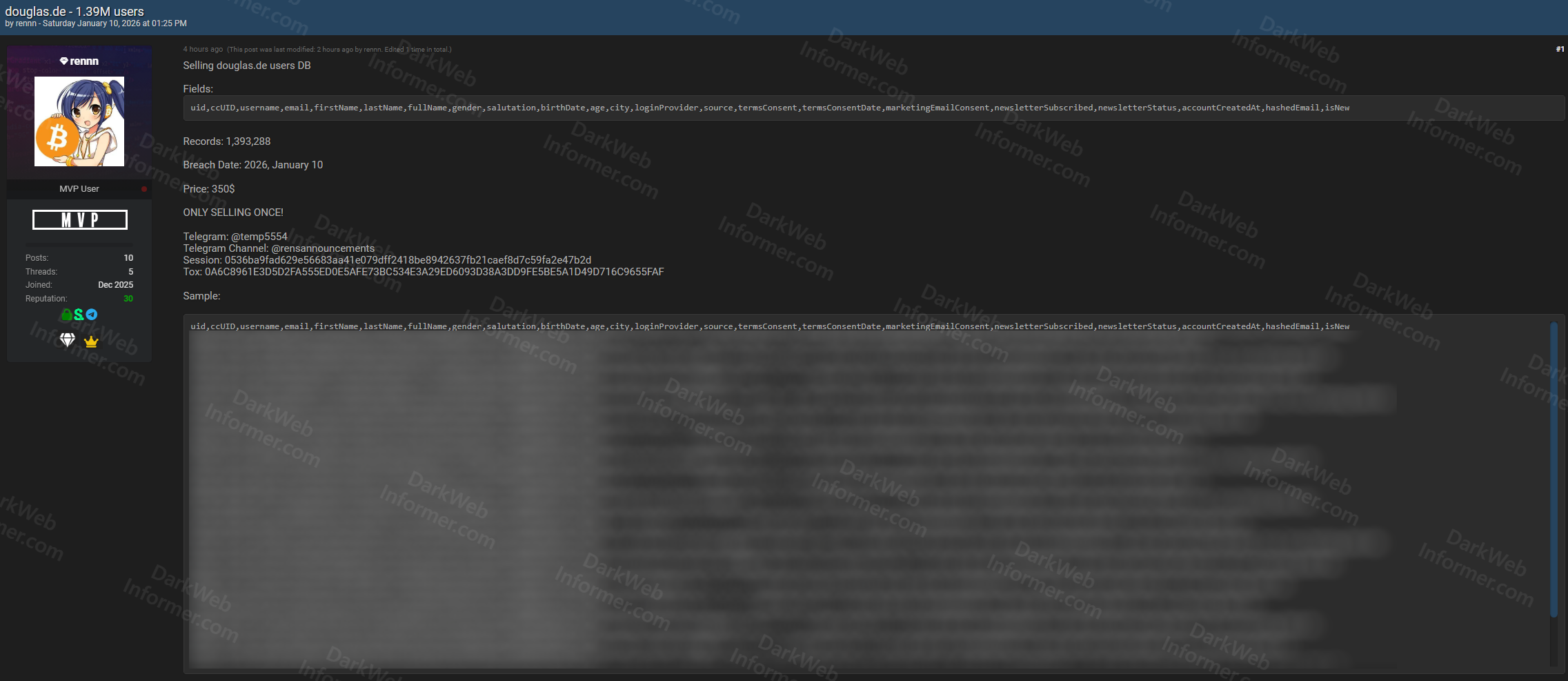
A threat actor using the handle "rennn" posted on BreachForums on January 10, 2026 claiming to be selling customer database records from Douglas Cosmetics (douglas.de), a German cosmetics and beauty retailer, containing 1,393,288 user records.
- Total Records: 1,393,288 customer database entries
- Breach Date: January 10, 2026
- Price: $350 USD
- Sale Status: Only selling once
- Contact Methods: Telegram @temp5554, Telegram Channel @rensmnnouncements
- Session ID: 053d6ad9fad629e56683ea41e079dff2418be894263fb21caef8d7c59fa2e47b29
- TOC: 0A6c89611E9D902F65EFD9E4EF73BC594E3A29FD6D93D38A3D9FFE9BE5A1D49D716C9655FAF
- Data Fields: uid, csID, username, email, firstName, lastName, fullName, gender, salutation, birthDate, age, city, loginProvider, source, termsConsent, termsConsentDate, marketingEmailConsent, newsletterSubscribed, newsletterStatus, accountCreatedAt, hashedEmail, isNew
Breach Claim URL
Unlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Dark Web Informer © 2026 | Cyber Threat Intelligence