📢 Unlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Get foundational access to breach intelligence — track breaches, leaks, and threats in real-time with unfiltered screenshots and expert summaries.
🏢 About ZIP
ZIP is a leading Israeli fashion brand specializing in youthful Italian-style clothing and accessories. Founded in 2003 by Ze’ev Aharonson, ZIP operates 54 retail locations across major malls in Israel, with headquarters in Afek Park, Rosh HaAyin, and a workforce of around 450 employees.
⚠ Disclaimer
This report includes actual screenshots and/or text that may include unredacted personally identifiable information (PII) gathered from publicly available sources.
The sensitive information presented within this report is intended solely for cybersecurity awareness and threat intelligence purposes.
📌 Overview
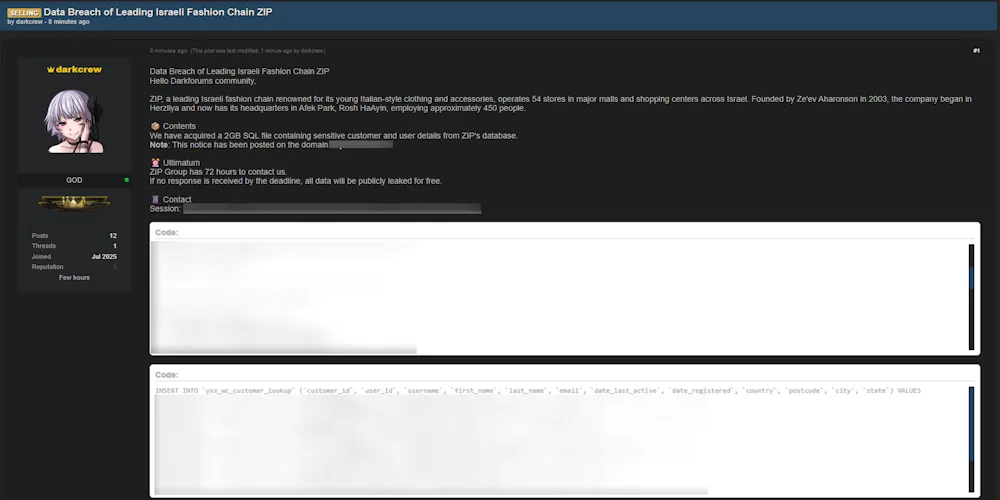
On July 30, 2025, a user named darkcrew posted on a known underground forum offering for sale a 2GB SQL file allegedly containing sensitive customer and user data from ZIP's internal systems. The post includes a 72-hour ultimatum to ZIP Group to respond, or else the full data set will be leaked for free.
📊 Key Details
| Attribute | Information |
|---|---|
| Date | 2025-07-30, 08:48:48 AM |
| Threat Actor | darkcrew |
| Victim Country | 🇮🇱 Israel |
| Industry | Fashion & Apparel |
| Victim Org. | ZIP |
| Victim Site | zipnet.co.il |
| Category | Data Breach |
| Severity | Medium |
| Network | Open Web (darkforums.st) |
Subscriber-only content…