Alleged Data Breach of French Retail Chain BLACKSTORE Exposing 102K Customer Records
🧩 Standalone API Access Now Available
Access high-volume threat-intelligence data, automated ingestion endpoints, ransomware feeds, IOC data, and more – independently from the above standard subscriptions.
View API AccessUnlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Quick Facts
Incident Overview
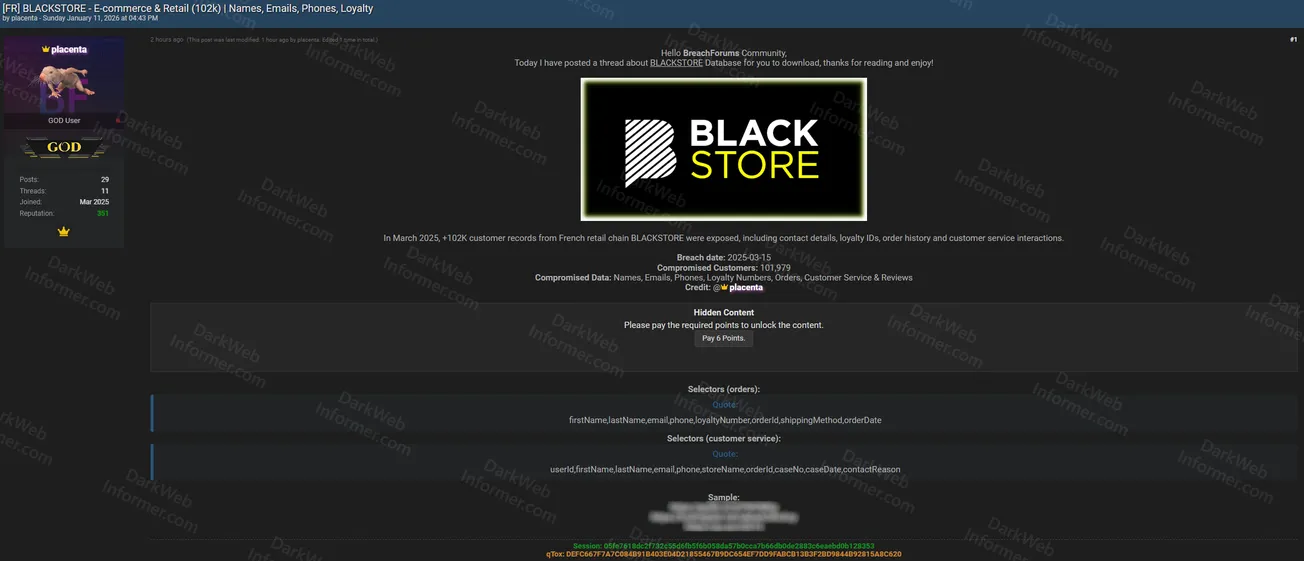
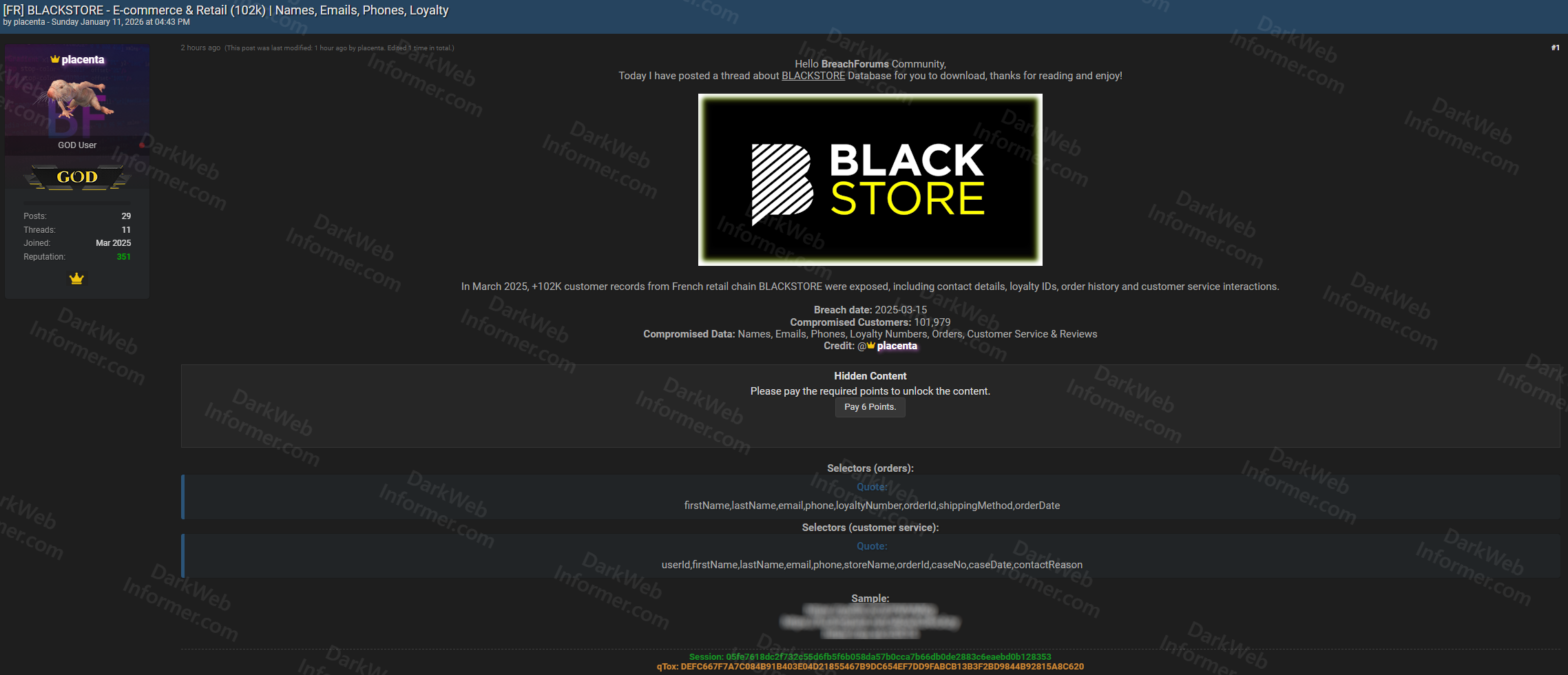
A threat actor using the handle "placenta" claims to have exposed approximately 102,000 customer records from French retail chain BLACKSTORE. The threat actor states that in March 2025, customer records from the French retail chain were exposed, including contact details, loyalty IDs, order history, and customer service interactions.
- Breach Date: March 2025 (2025-03-15)
- Compromised Customers: 101,979 records
- Full Names: First and last names of customers
- Email Addresses: Contact email addresses
- Phone Numbers: Customer phone numbers
- Loyalty Numbers: Loyalty card or membership IDs
- Order History: Purchase history including order IDs, shipping methods, and order dates
- Customer Service Interactions: Support tickets, case IDs, contact reasons, and customer reviews
- Database Selectors (Orders): firstName, lastName, email, phone, loyaltyNumber, orderId, shippingMethod, orderDate
- Database Selectors (Customer Service): userId, firstName, lastName, email, phone, storeName, orderId, caseId, caseNo, caseDate, contactReason
Indicators of Compromise (IOCs)
Session Messenger ID
05fe7618dc2f732c55d6fb5f6b058da57b0cca7b66db0de2883c6eaebd0b128353
Note: This Session ID can be used to identify the threat actor's communication channel.
qTox ID
DEFC667F7A7C084B91B403E04D21855467B9DC654EF7DD9FABCB13B3F2BD9844B92815A8C620
Note: This qTox ID can be used to identify the threat actor's Tox communication channel.
Breach Claim URL
Unlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Dark Web Informer © 2026 | Cyber Threat Intelligence