Alleged Data Breach of French IT Services Platform Réseau Exposes 73,000 Users
Unlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Quick Facts
Incident Overview
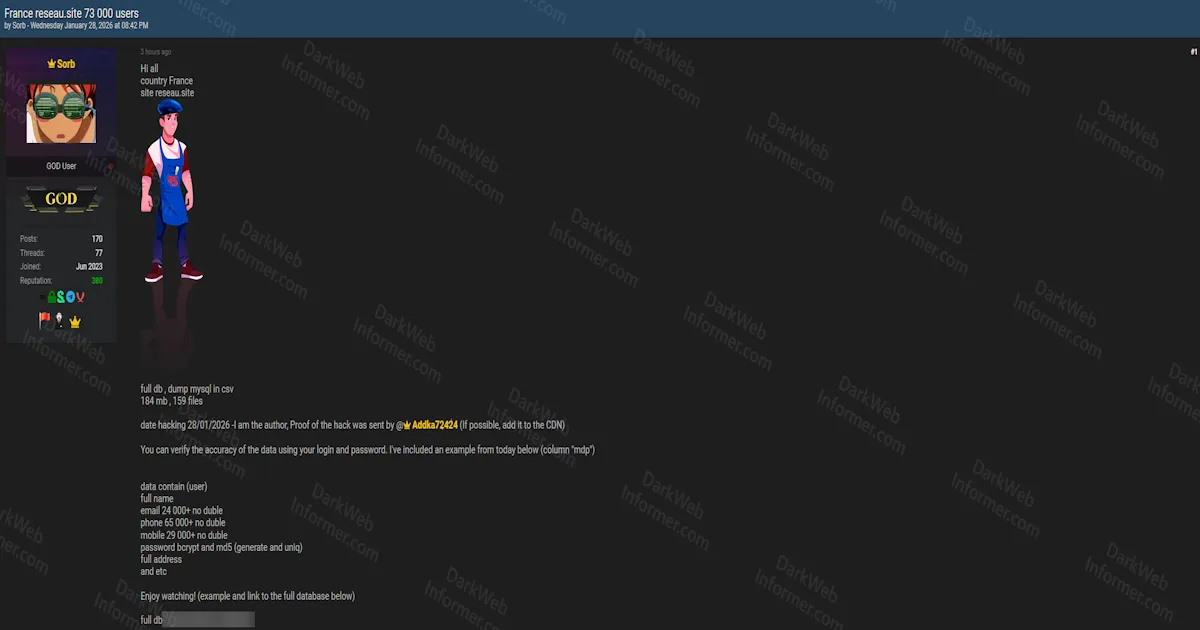
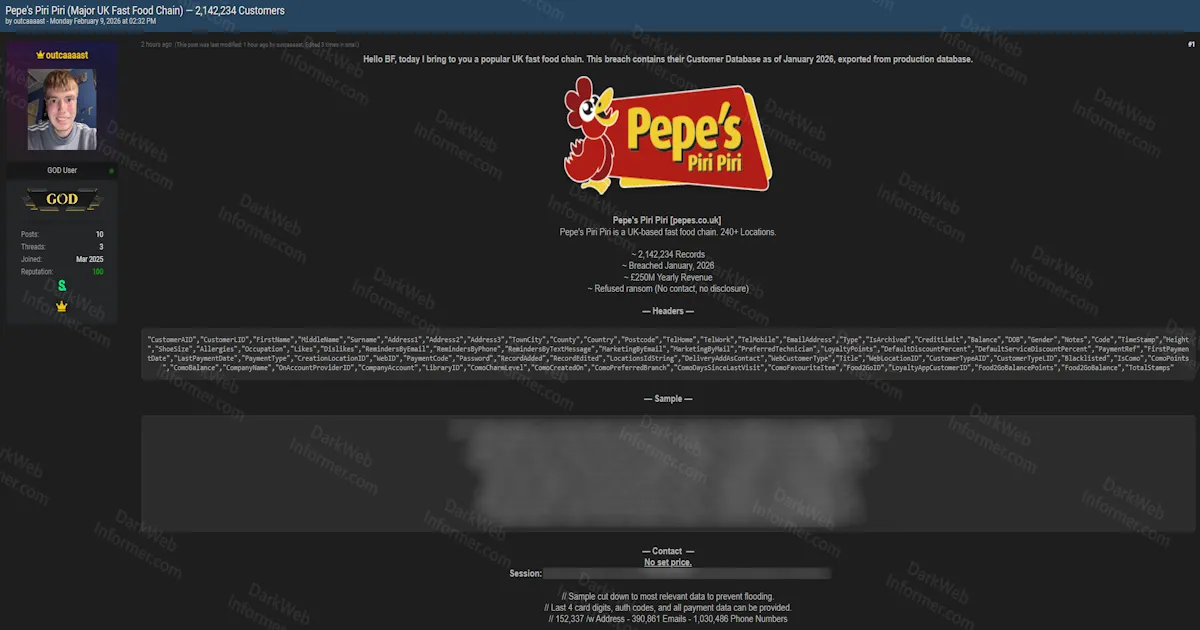
A threat actor operating under the handle "Sorb" has posted on BreachForums claiming responsibility for a data breach targeting reseau.site, a French IT services platform. According to the forum post dated January 28, 2026, the threat actor claims to have exfiltrated the full MySQL database, totaling 184 MB across 159 CSV files.
The alleged dataset reportedly contains over 24,000 unique email addresses (no duplicates), 65,000+ phone numbers, and 29,000+ mobile numbers. The threat actor states the data includes full names, physical addresses, and passwords hashed using bcrypt and MD5 algorithms. The actor claims the hack occurred on January 28, 2026, and states that proof of the hack was sent to another user (@Addka72424) for verification. A sample from the database was provided, and the full dataset has been made available via a file-sharing link.
This post is for subscribers on the Plus, Pro and Elite tiers
SubscribeAlready have an account? Sign In