Alleged Data Breach of Audio Systems Manufacturer Tymphany Exposing Source Code and Confidential Technical Data
🧩 Standalone API Access Now Available
Access high-volume threat-intelligence data, automated ingestion endpoints, ransomware feeds, IOC data, and more – independently from the above standard subscriptions.
View API AccessUnlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Quick Facts
Incident Overview
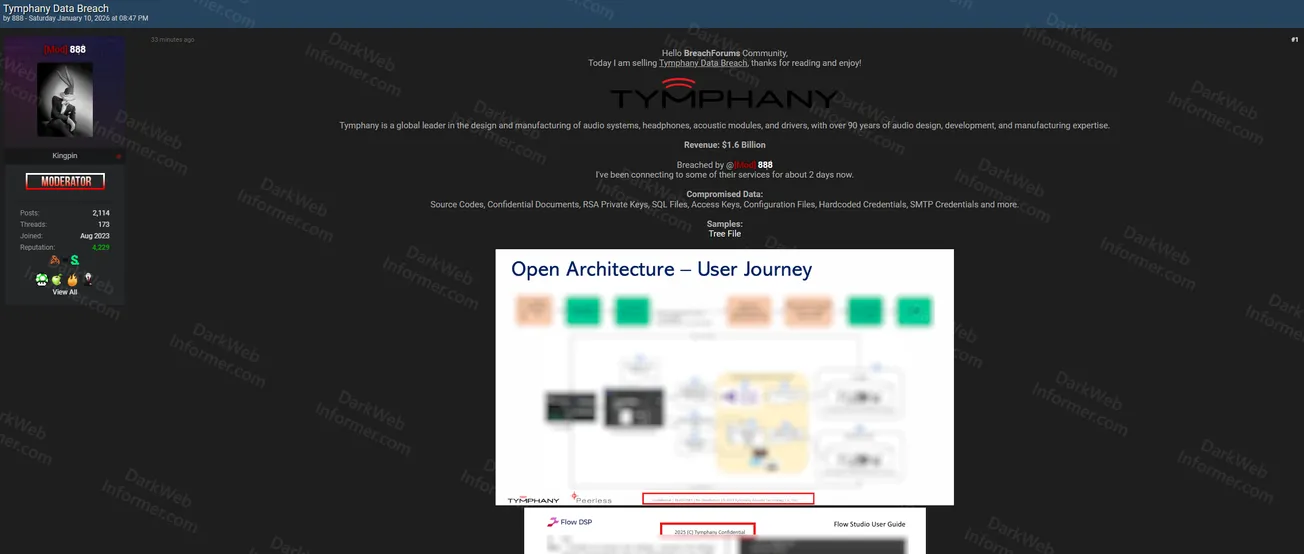
A threat actor using the handle "888" posted on BreachForums on January 10, 2026 claiming to be selling leaked data from Tymphany, a global leader in the design and manufacturing of audio systems, headphones, acoustic modules, and drivers with over 90 years of audio design, development, and manufacturing expertise and $1.6 billion in revenue. The threat actor claims to have been connecting to some of their services for approximately 2 days.
- Company Profile: Global leader in audio systems design and manufacturing with over 90 years of expertise
- Revenue: $1.6 billion
- Breach Duration: Threat actor claims approximately 2 days of access to services
- Source Codes: Proprietary software and development code
- Confidential Documents: Internal technical documentation and business materials
- RSA Private Keys: Cryptographic keys for secure communications
- SQL Files: Database files and schemas
- Access Keys: Authentication credentials for systems and services
- Configuration Files: System and application configuration data
- Hardcoded Credentials: Embedded authentication information in code
- SMTP Credentials: Email server authentication details
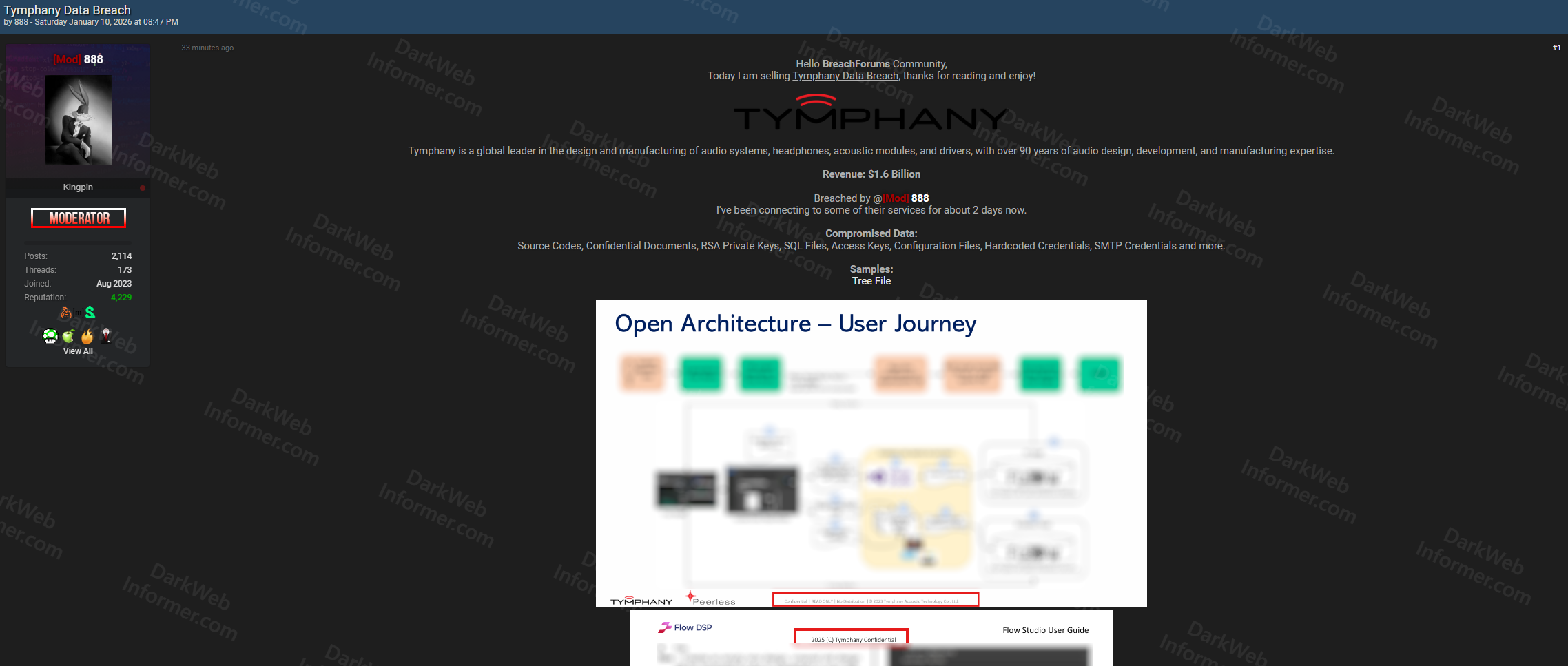
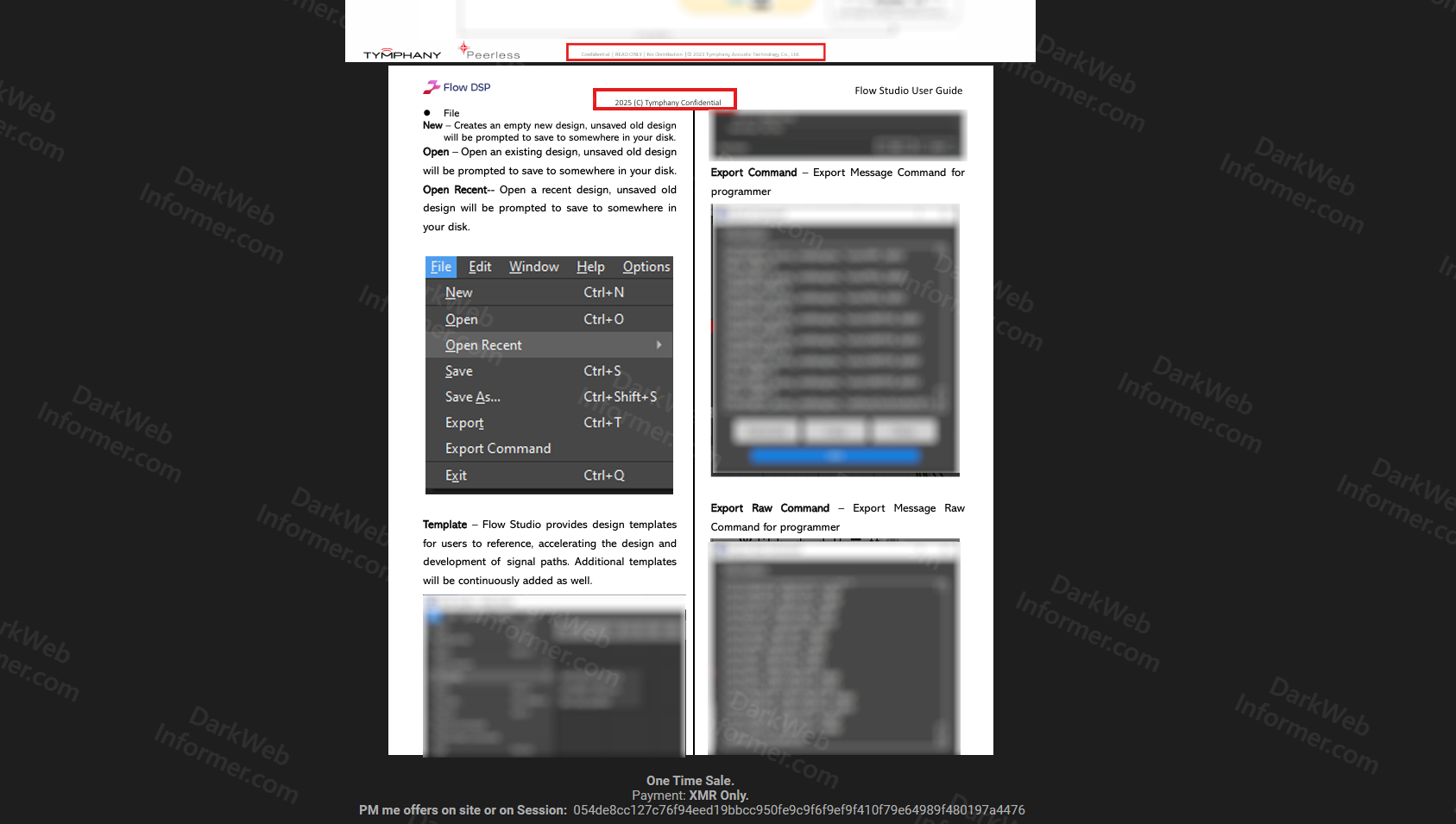
- Sample Files: Tree file structure showing "Open Architecture - User Journey" with Flow DSP documentation, Flow Studio User Guide, and export command examples
- Payment: One-time sale, XMR (Monero) only
- Contact: PM on-site or Session messenger
Indicators of Compromise (IOCs)
Session Messenger ID
054de8cc127c76f94eed19bbcc950fe9c9f6f9ef9f410f79e64989f480197a4476
Note: This Session ID can be used to identify the threat actor's communication channel.
Breach Claim URL
Unlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Dark Web Informer © 2026 | Cyber Threat Intelligence