Advanced Malware Delivery System Bypassing Windows SmartScreen, MOTW, and Defender Available for Sale
🧩 Standalone API Access Now Available
Access high-volume threat-intelligence data, automated ingestion endpoints, ransomware feeds, IOC data, and more – independently from the above standard subscriptions.
View API AccessUnlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Quick Facts
Incident Overview
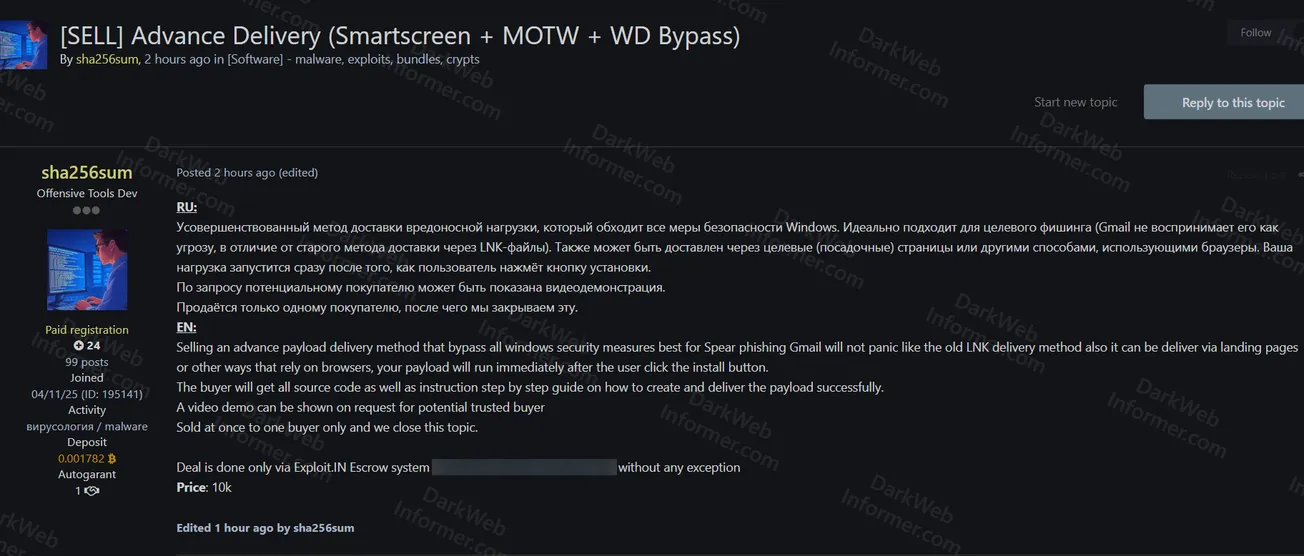
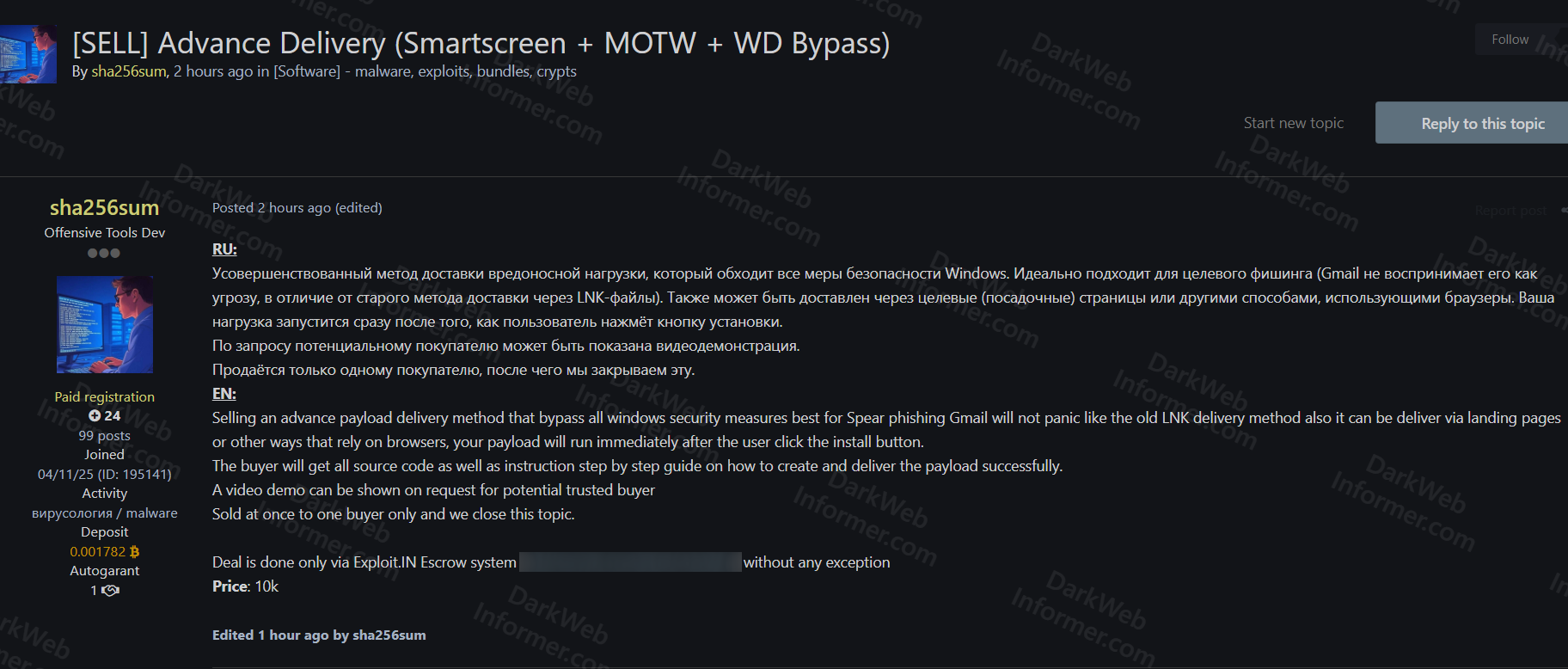
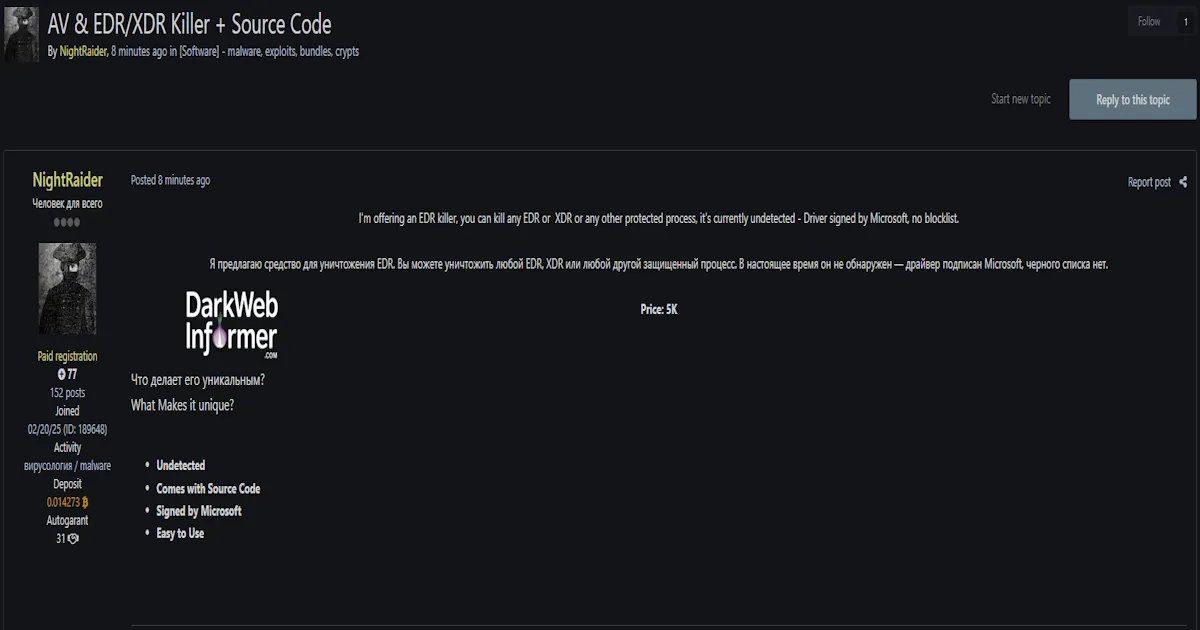
A threat actor using the handle "sha256sum" claims to be selling an advanced payload delivery method that bypasses all Windows security measures. The delivery system is designed to circumvent SmartScreen, Mark of the Web (MOTW), and Windows Defender, making it ideal for spear phishing campaigns. Unlike older LNK file delivery methods, this system can also be delivered via landing pages or other browser-based methods that rely on immediate payload execution after the user clicks the install button.
- Delivery Method: Advanced payload delivery system
- Security Bypasses: Windows SmartScreen, Mark of the Web (MOTW), Windows Defender
- Use Case: Ideal for spear phishing campaigns, particularly targeting Gmail users without triggering panic
- Delivery Channels: Landing pages and other browser-based methods
- Execution: Payload runs immediately after user clicks install button
- Package Contents: Full source code and step-by-step instruction guide
- Instructions: Detailed guide on how to create and deliver the payload successfully
- Video Demo: Available on request for potential trusted buyers
- Sale Terms: Sold at once to one buyer only, topic closed after purchase
- Transaction: Deal done only via Exploit.IN Escrow system without any exception
- Price: 10,000 USD
Indicators of Compromise (IOCs)
No IOCs were disclosed by the threat actor in this claim.
Listing URL
Unlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Dark Web Informer © 2026 | Cyber Threat Intelligence