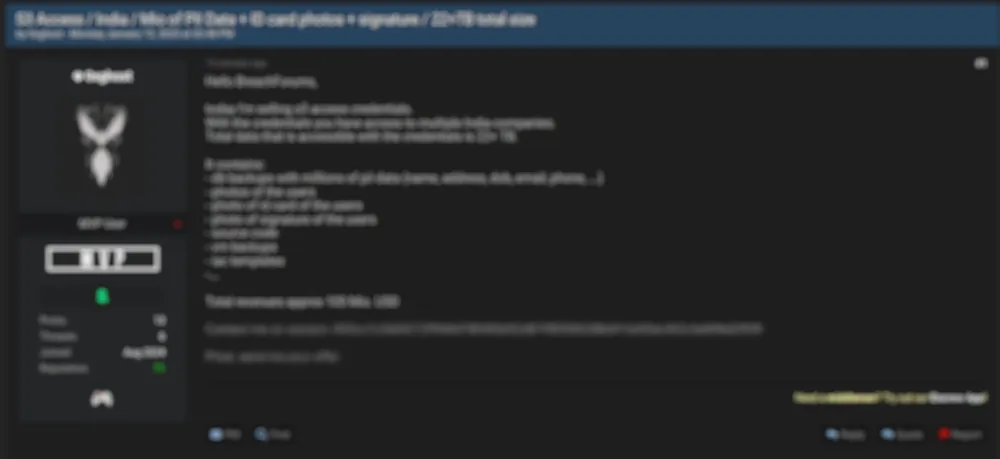
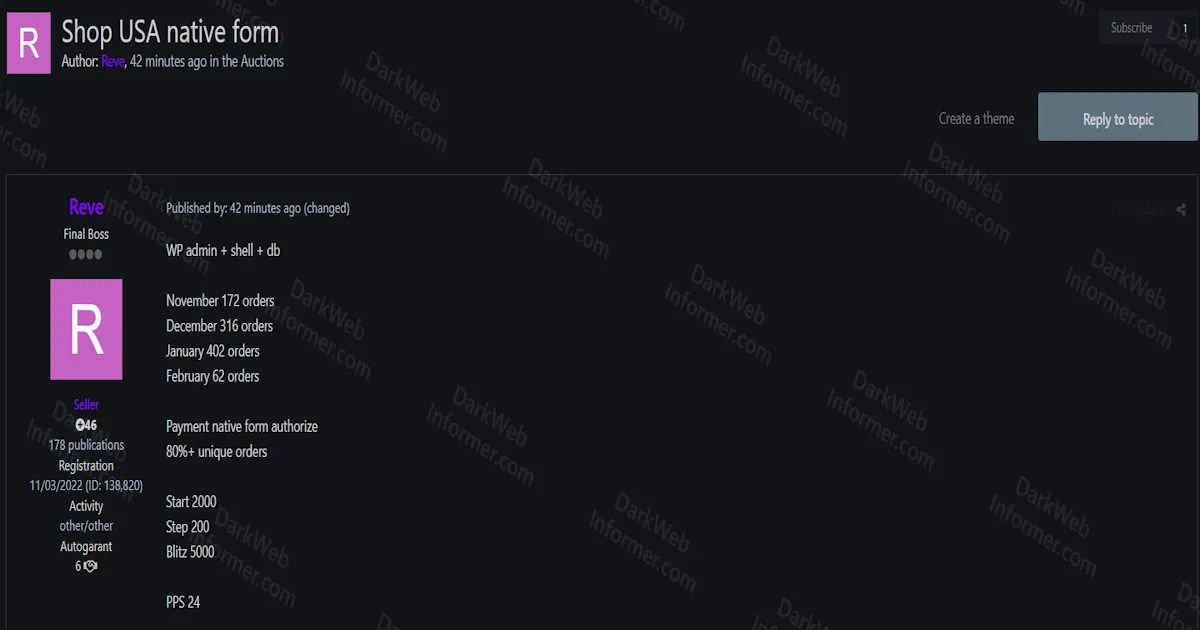
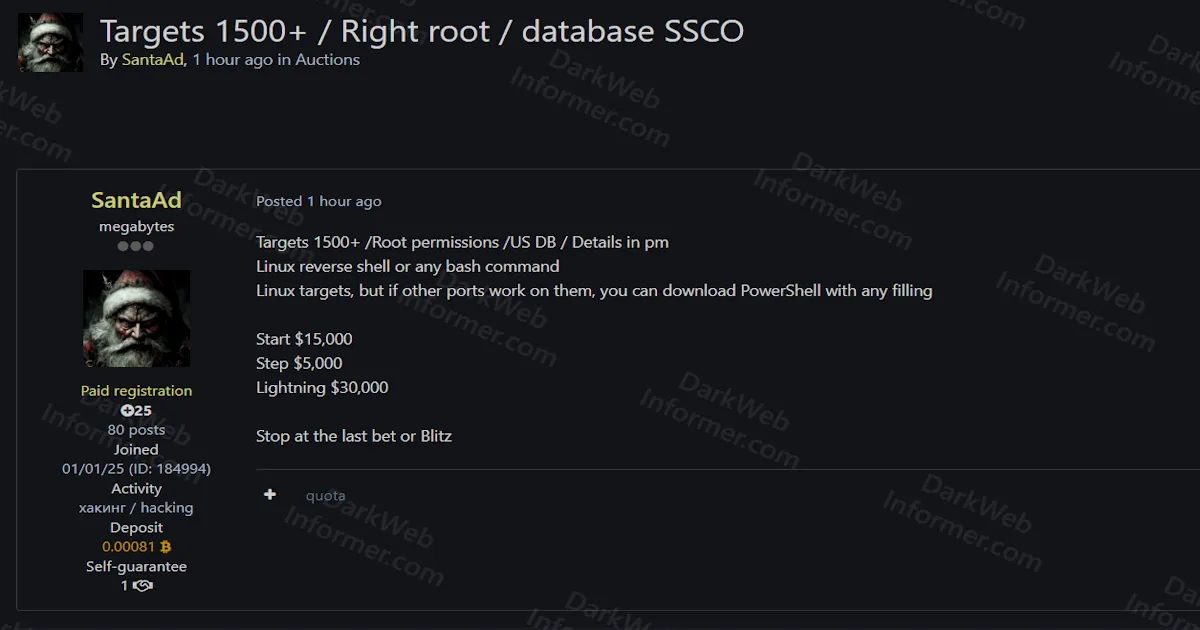
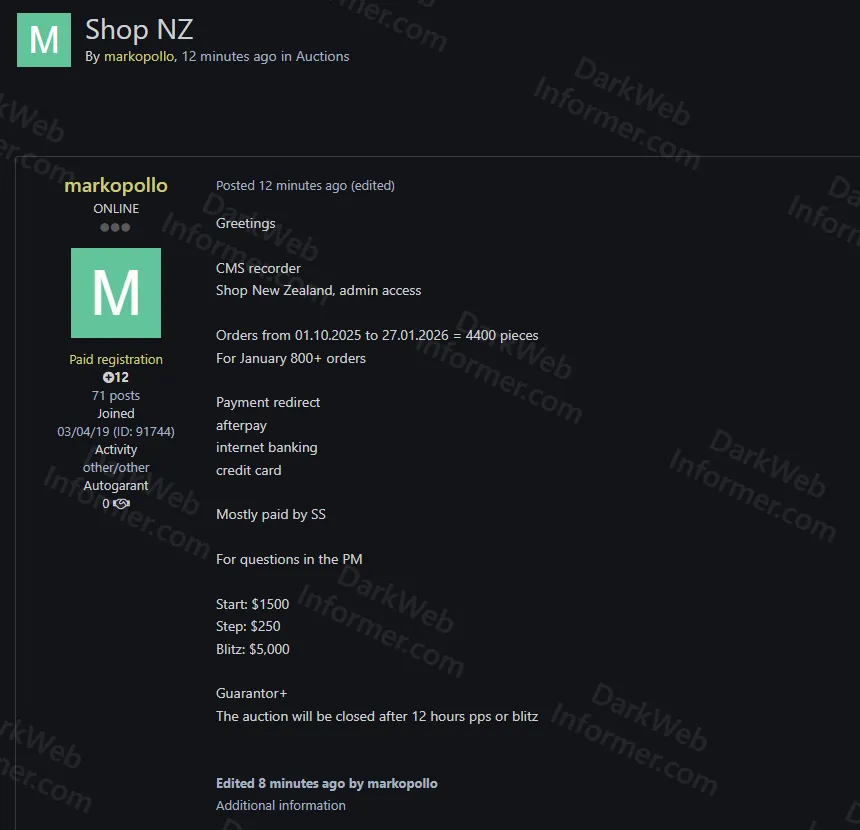
💡 Subscribe to DarkWebInformer.com for Unmatched Cyber Threat Intelligence 💡
Why Subscribe? Let me do the work and save you time.
Stay ahead of cyber threats and safeguard your digital assets while enhancing your cybersecurity awareness with these exclusive subscriber-only features:
-
📜
Detailed Threat Posts: Stay updated on breaches, ransomware, DDoS attacks, and more.
-
📡
Exclusive Threat Feeds: Access the latest ransomware victim disclosures, breaches, and other critical updates.
-
🖼️
High-Resolution Screenshots: All posts include watermark-free, high-resolution images.
-
🔗
Direct Claim URLs: Instantly access claims with direct links for fast verification.