🔎 Quick Facts
🔗 DarkWebInformer.com - Cyber Threat Intelligence
📅 Date: 2025-02-20 20:57:48
🚨 Title: Alleged LPE Vulnerability in Multiple Windows Versions
🛡️ Victim Country: Unspecified
🏭 Victim Industry: Unspecified
🏢 Victim Organization: Unspecified
🌐 Victim Site: Not Provided
📜 Category: Vulnerability
🔗 Claim: https://forum.exploit.in/topic/254582/
🕵️♂️ Threat Actor: LukeBerry
🌍 Network: OpenWeb
📝 What Happened?
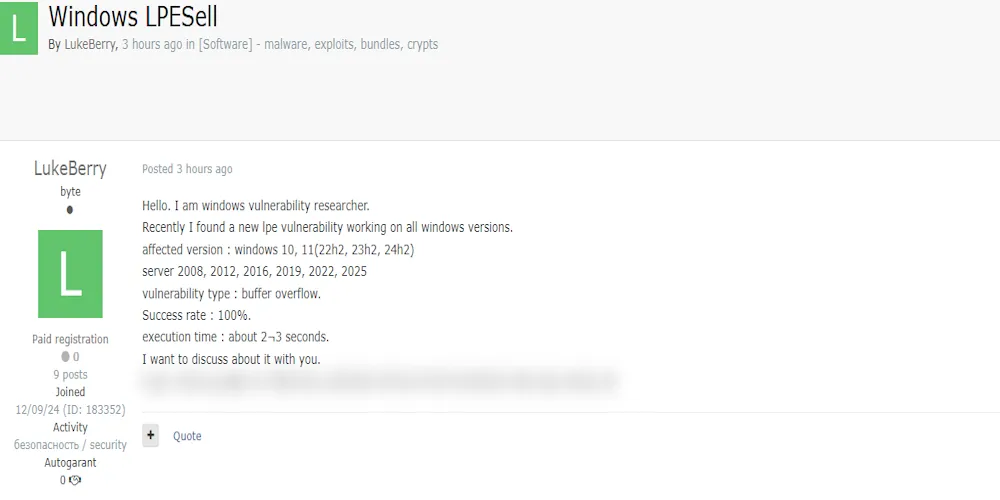
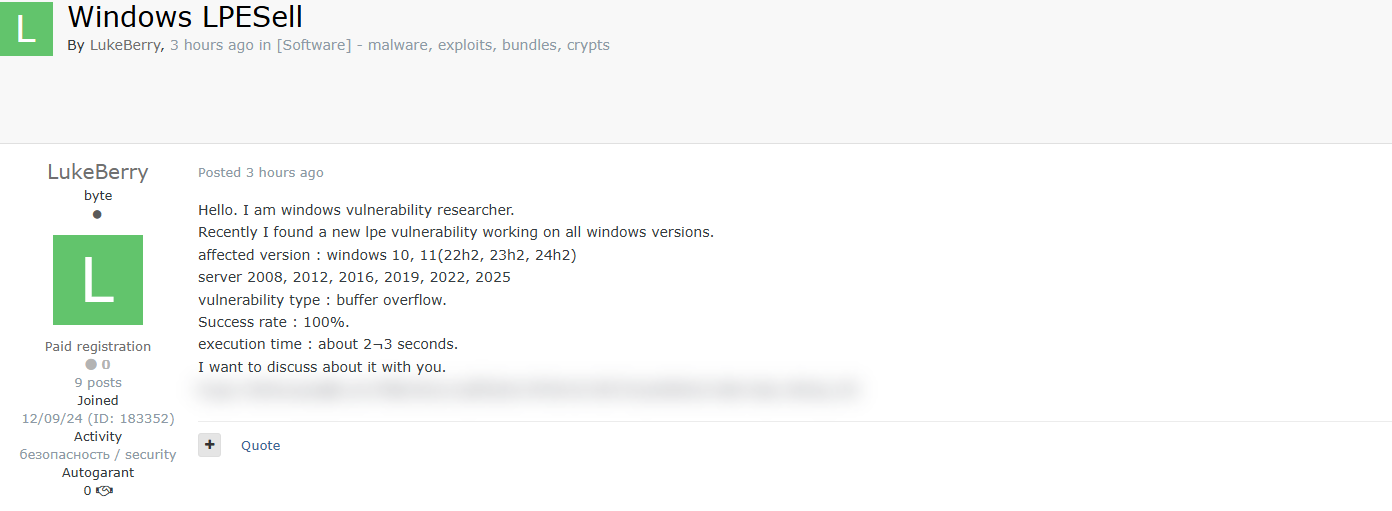
A threat actor identified as LukeBerry has claimed to have discovered a new Local Privilege Escalation (LPE) vulnerability affecting multiple versions of Microsoft Windows, including:
- Windows 10 (22H2, 23H2, 24H2)
- Windows 11 (22H2, 23H2, 24H2)
- Windows Server 2008, 2012, 2016, 2019, 2022, and 2025
According to the post, the exploit leverages a buffer overflow vulnerability, has a 100% success rate, and executes within 2-3 seconds.
The actor has not disclosed specific details publicly but appears to be offering discussions for potential sale or private disclosure on a cybercrime forum.
If legitimate, this exploit could allow attackers to gain SYSTEM privileges, potentially bypassing security controls and escalating access within Windows environments.
📊 Compromised Access Details
- Vulnerability Type: Local Privilege Escalation (LPE) via Buffer Overflow
- Potentially Affects: Windows 10, 11, and Windows Server editions
- Execution Speed: ~2-3 seconds
- Threat Actor is Seeking Buyers/Collaborators
🛡 WhiteIntel.io Data Leak Information
(No victim site disclosed)
⚠ Implications
- High Risk for Windows Environments – An LPE vulnerability with a 100% success rate could be weaponized in malware and ransomware attacks.
- Potential Zero-Day Exploitation – If unpatched, this could be an actively exploited zero-day vulnerability.
- Widespread Attack Surface – The exploit targets all major Windows releases, posing a threat to enterprise, government, and personal users.
🔧 Recommended Actions
- Endpoint & Network Protection – Organizations should monitor for LPE exploit attempts and enforce security hardening.
- Threat Intelligence Monitoring – Security teams should track dark web discussions for proof-of-concept exploits or real-world attacks.
- User Access Controls & Least Privilege Enforcement – Restrict admin privileges and implement security monitoring tools to detect unauthorized privilege escalation.
⚠ Stay informed on emerging cyber threats. Visit DarkWebInformer.com for real-time updates on security risks and breaches.