💡 Subscribe to DarkWebInformer.com for Unmatched Cyber Threat Intelligence 💡
Why Subscribe? Let me do the work and save you time.
Stay ahead of cyber threats and safeguard your digital assets while enhancing your cybersecurity awareness with these exclusive subscriber-only features:
-
📜
Detailed Threat Posts: Stay updated on breaches, leaks, ransomware, DDoS attacks, and more.
-
📡
Exclusive Threat Feeds: Access the latest ransomware victim disclosures, breaches, leaks, and other critical updates. Approximately 100-150 alerts daily.
-
🖼️
High-Resolution Screenshots: All threat alerts include watermark-free, high-resolution images.
-
🔗
Direct Claim URLs: Instantly access claims with direct links for fast verification.
🔗 DarkWebInformer.com - Cyber Threat Intelligence
📅 Date: 2025-01-29 17:37:08
🚨 Title: Alleged Sale of RCE FortiOS Vulnerability
🛡️ Victim Country: N/A
🏭 Victim Industry: N/A
🏢 Victim Organization: N/A
🌐 Victim Site: N/A
📜 Category: Vulnerability
🔗 Claim: https://ramp4u.io/threads/rce-fortios-cve-2024-21762-reverse-shell.2591/
🕵️♂️ Threat Actor: HuanEbashes
🌍 Network: OpenWeb
📝 Description
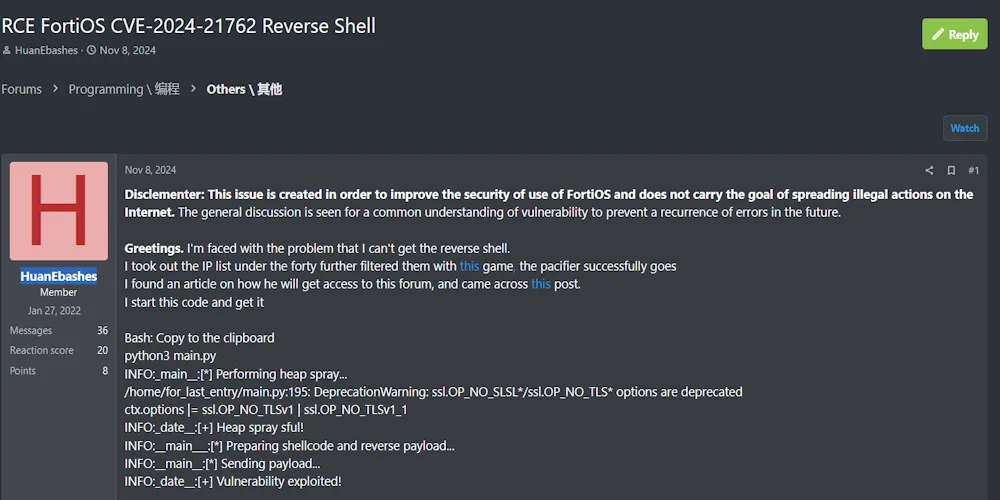
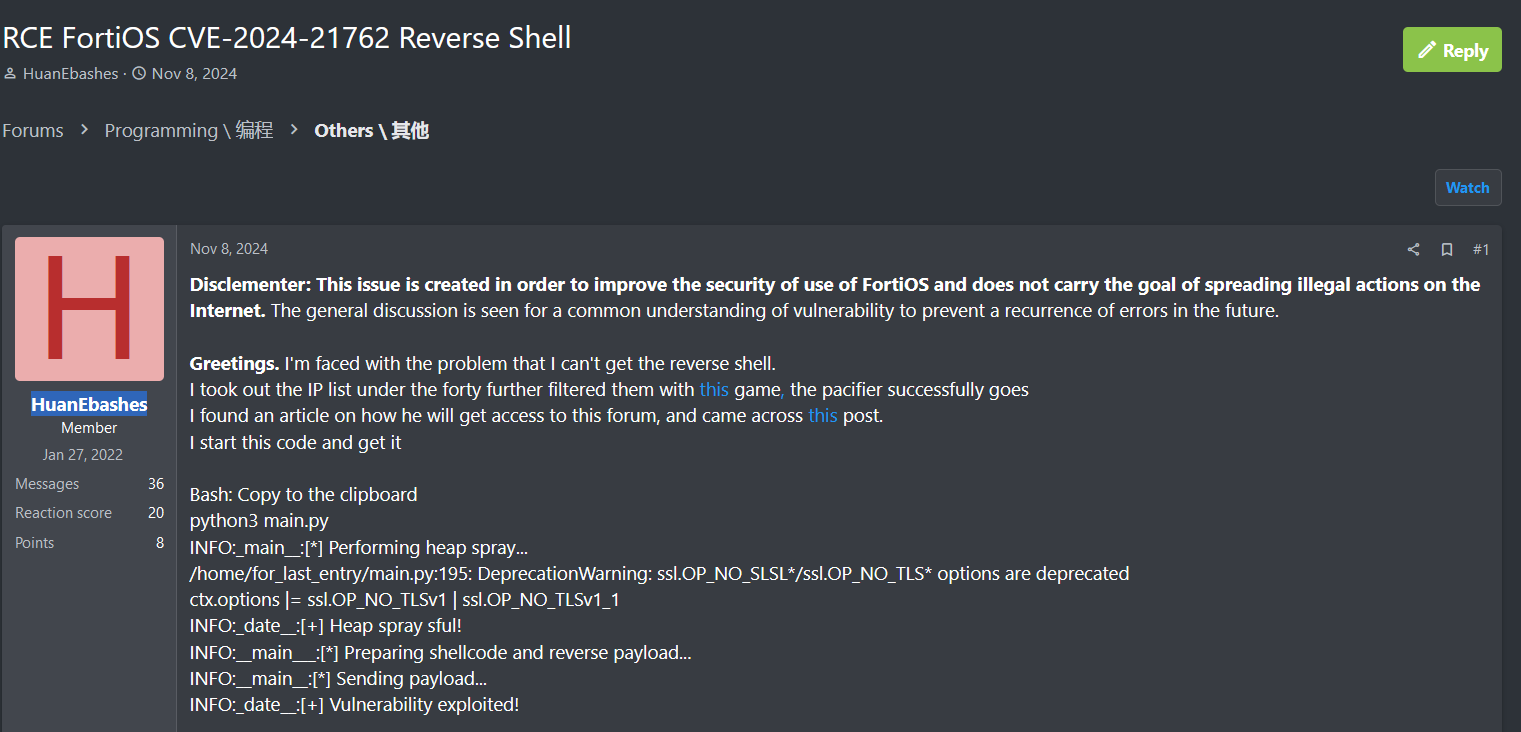
A cybercriminal operating under the alias HuanEbashes has posted on a hacking forum, advertising a working Remote Code Execution (RCE) exploit for FortiOS, specifically CVE-2024-21762. This vulnerability is being marketed as a reverse shell exploit, allowing attackers to gain unauthorized access to Fortinet devices remotely.
The post discusses difficulties in executing the reverse shell but ultimately suggests a successful exploit, with logs indicating:
- Heap Spray Execution (suggesting memory corruption techniques)
- Shellcode Preparation & Payload Delivery
- Successful Exploitation Confirmation
The listing implies that the exploit is available for purchase, posing a significant threat to organizations relying on Fortinet security appliances.
WhiteIntel.io Data Leak Information
(No victim site disclosed)
📊 Compromised Data (Potential Risks & Impact)
Potential Targets & Exposure
- Network Infrastructure: Attackers could gain full control over FortiOS-powered firewalls and VPNs.
- Enterprise Security Breaches: Unauthorized access could enable lateral movement within corporate networks.
- Data Theft & Ransomware Deployment: Threat actors may use the exploit for espionage or ransomware attacks.
Technical Capabilities of the Vulnerability
- Remote Code Execution: Allows execution of arbitrary commands with administrative privileges.
- Persistence Mechanisms: Attackers can maintain long-term access to compromised systems.
- Bypassing Security Controls: Potential to disable security monitoring and bypass firewall restrictions.
⚠️ Implications
For Organizations Using Fortinet Products:
- Critical risk of network compromise if patches are not applied immediately.
- Potential compliance violations if sensitive data is exfiltrated through an exploited firewall.
- Heightened risk of ransomware attacks leveraging the vulnerability for initial access.
For Cybersecurity & IT Teams:
- Urgent need to deploy Fortinet security patches to prevent exploitation.
- Monitor network logs for suspicious activity linked to heap spray attacks or shell execution.
- Enforce Zero Trust policies to minimize the impact of a potential breach.
For Law Enforcement & Threat Intelligence Communities:
- Growing market for zero-day and N-day exploits on underground forums.
- Difficulties in tracking attackers, as vulnerabilities are quickly weaponized.
- Need for collaborative defense strategies to mitigate widespread exploitation.
🔧 Recommendations
For Organizations Using Fortinet Firewalls & VPNs:
- Patch FortiOS immediately to remediate CVE-2024-21762.
- Restrict remote access and disable unnecessary admin interfaces.
- Deploy advanced threat detection tools to identify unusual activity.
- Enable multi-factor authentication (MFA) to prevent unauthorized access.
- Conduct internal security assessments to detect potential compromise.
For Security Researchers & IT Defenders:
- Monitor dark web forums for emerging exploit sales and activity.
- Simulate attacks in controlled environments to assess organizational exposure.
- Report exploitation attempts to cybersecurity vendors and authorities.
- Educate security teams on mitigation strategies for RCE vulnerabilities.
For real-time updates on cybersecurity threats and vulnerability exploits, visit DarkWebInformer.com.